“….(His) Inner eye opened to the stepped scarlet pyramid of the Eastern Seaboard Fission Authority burning beyond the green cubes of Mitsubishi Bank of America, and high and very far away he saw the spiral arms of military systems, forever beyond his reach.”
from “Neuromancer“, William Gibson
… and off in the corner of that vast array of light and shadow – that brave new world we have created beyond the pixels – sits you and your organization. Your company, your school, your governmental organization….visible in a way you may have never seen.
And that’s the problem.
William Gibson’s protagonist has the ability to “jack into the matrix” and see this new world for what it is: A universe of manipulable interfaces and data constructs that radiates beyond the physical world. Invisible to those not so gifted.
My experience over the last few years has made me aware that many organizations that have a face they present to this new world are unaware of what it looks like.
Attackers do. They see your presence on the Internet with bright clarity.
Its not the building you drive to everyday. Its not the office, cubicle farm, memos, meetings, and daily internal dramas that occupy so much of our work day.
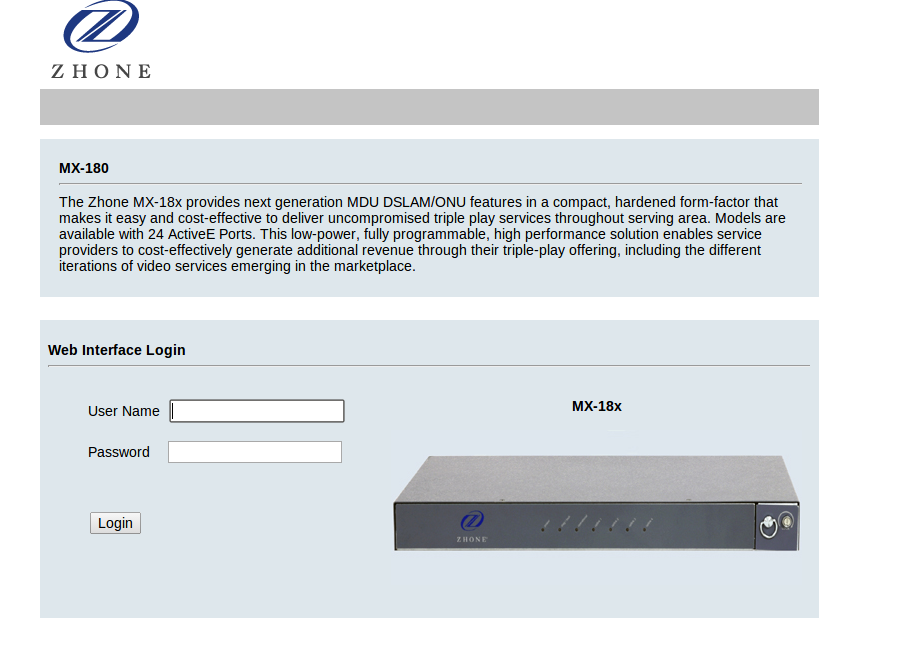
It’s not these windows an attacker sees:
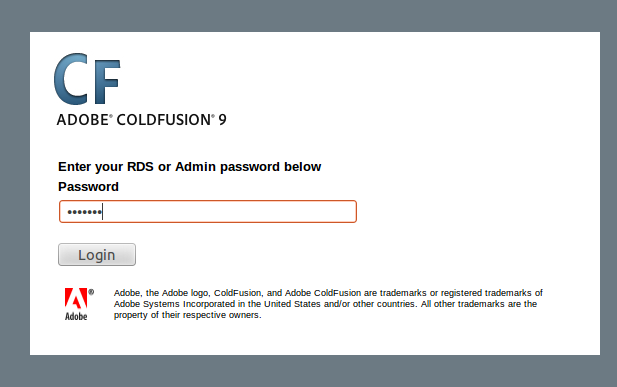
It’s windows like this one – visible to any Internet attacker:
… or this:
There’s nothing inherently wrong with having such a “window” on the Internet, just as there’s nothing wrong about having windows in your house. But – you know ALL the windows in your house. You make sure they are closed, locked, and in some cases you replace the more vulnerable ones with glass brick, or remove them entirely.
Do you know the windows your enterprise shows to the Internet? And if your reaction is, “Well, I don’t, but I’m sure someone does.” – you may be surprised to find they don’t. Your techs – including your networking techs – may know the exposures they are responsible for – but they may be completely unaware of exposures created 10 years ago by some previous group. These exposures live on, potentially populated by systems no longer being maintained. It happens – a lot.
What to do? How to learn who you are on the Internet?
- Talk to your network admins about the Internet ranges assigned to your organization.
- They will know what they manage – but that may be all they know.
- They may be unaware of network ranges that are in use ( or were at one time) by other portions of your enterprise now or in the past.
- If your organization has grown as a result of mergers an acquisitions there could very well be ranges in use they are completely unaware of.
- Be aware also that “mistakes happen”. Firewall rules are typo’ed and unintended exposures occur.
- Contact your Billing department.
- Make sure you can account for all payments to Internet Service Providers (ISPs) by your organizations. Get contact info.
- Contact your known ISPs.
- Ask them what IP ranges you are assigned. Be aware that you may be told a range of IP addresses that is actually larger than what you are assigned – a range that encompasses other organization’s assignments. You will have to check.
- Ask them what IP ranges you are assigned. Be aware that you may be told a range of IP addresses that is actually larger than what you are assigned – a range that encompasses other organization’s assignments. You will have to check.
- Become familiar with ARIN (American Registry for Internet Numbers) and the other “Regional Internet Registries” (RIR).
- ARIN handles IP range registration for North America
- IP ranges may be specifically allocated to your organization, or they may be suballocated by your Internet Service provider (ISP) functioning as a “Local Internet Registry“
- Try a lookup of one of your known IP address at: https://www.arin.net/
- Be aware that your primary public web site may be at a hosting facility and not at an IP address actually allocated to your own organization. FTP, VPN and other such services are more likely to be “yours”.
- Become familiar with the WHOIS command, available on all Linux variants.
- Do WHOIS lookups based on IP addresses you know to be yours.
- Various web services provide WHOIS lookup:
- Depending on the diligence of your ISP ( and that of any upstream providers they in turn use) you may find specific information about your sub-allocation. If not – talk to your ISP
Verify your new list of Internet IP addresses! ( as in “trust, but verify“)
- FIRST! – Let you ISP know you will be doing checks against your assigned IPs.
- Examine each Internet IP address for its service exposure – look for returned banners and check each web server exposure with a browser.
- Are they all yours? – If not ( and it happens) contact your ISP to resolve.
- Make a definitive list of your confirmed IP addresses and their services.
- Circulate that list within your organization – look for confirmation or objection.
- Publish the list when finalized – make sure everyone who could remove or create a new exposure knows that they must keep that list current!
Your organization now knows what it looks like on the Internet.
- Keep the list updated and disseminated within your organization.
- Either perform or commission regular (quarterly?) security assessments against ALL your Internet services.
- These assessments will test the security of your services AND inventory them.
- You may be surprised when new services appear or old ones disappear. Change management is a great – when it works. 😉
- Act quickly to resolve any security findings. No internal excuses for public vulnerabilities!
Following the above steps will help you to know what your organization looks like in the “new” real world and will help ensure that look is a secure and confident one.
Questions? Email: info@micrsosolved.com


My current MSI ramble: http://t.co/a7kQ69ZDow