Despite the fact that the Shellshock bug was disclosed last fall, it appears that a wide variety of systems are still falling victim to the exploit. For example, in the last 30 days, our HoneyPoint Internet Threat Monitoring Environment has observed attacks from almost 1,000 compromised QNAP devices. If you have QNAP devices deployed, please be sure to check for the indicators of a compromised system. If your device has not been affected, be sure to patch it immediately.
Once compromised via the Shellshock bug, the QNAP system downloads a payload that contains a shell script designed specifically for QNAP devices. The script acts as a dropper and downloads additional malicious components prior to installing the worm and making a variety of changes to the system. These changes include: adding a user account, changing the device’s DNS server to 8.8.8.8, creating an SSH server on port 26 and downloading/installing a patch from QNAP against the Shellshock bug.
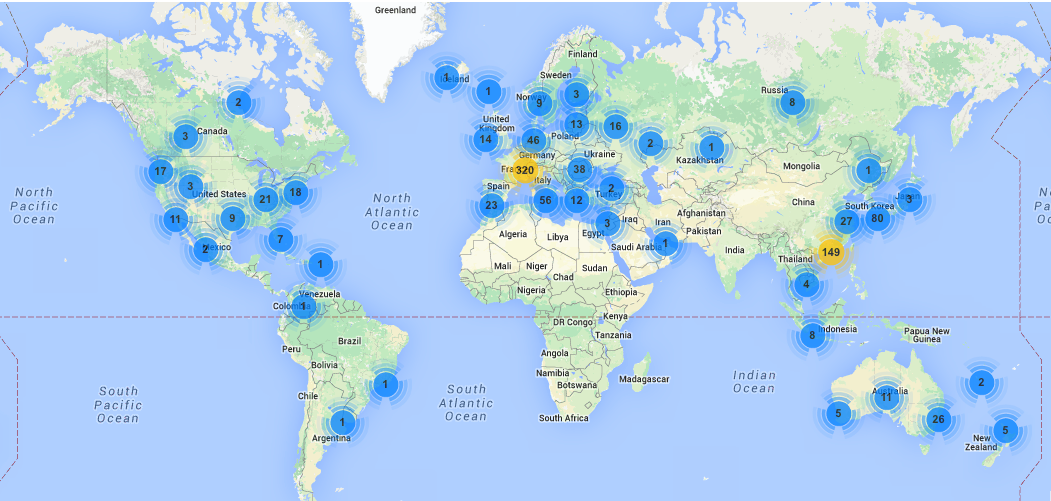
The map below shows the locations of compromised QNAP systems that we observed to be scanning for other unpatched QNAP systems. If you have any questions regarding this exploit, feel free to contact us by emailing info <at> microsolved.com.