This post describes a malware detection event that I actually experienced a few short years ago.
My company (Company B) had been acquired by a much larger organization (Company A) with a very large internal employee desktop-space. A desktop-space larger than national boundaries.
We had all migrated to Company A laptops – but our legacy responsibilities required us to maintain systems in the original IP-space of company B. We used legacy Company B VPN for that.
I had installed the HPSS honeypoint agent on my Company A laptop prior to our migration into their large desktop space. After migration I was routinely VPN’ed into legacy Company B space, so a regular pathway for alerts to reach the console existed.
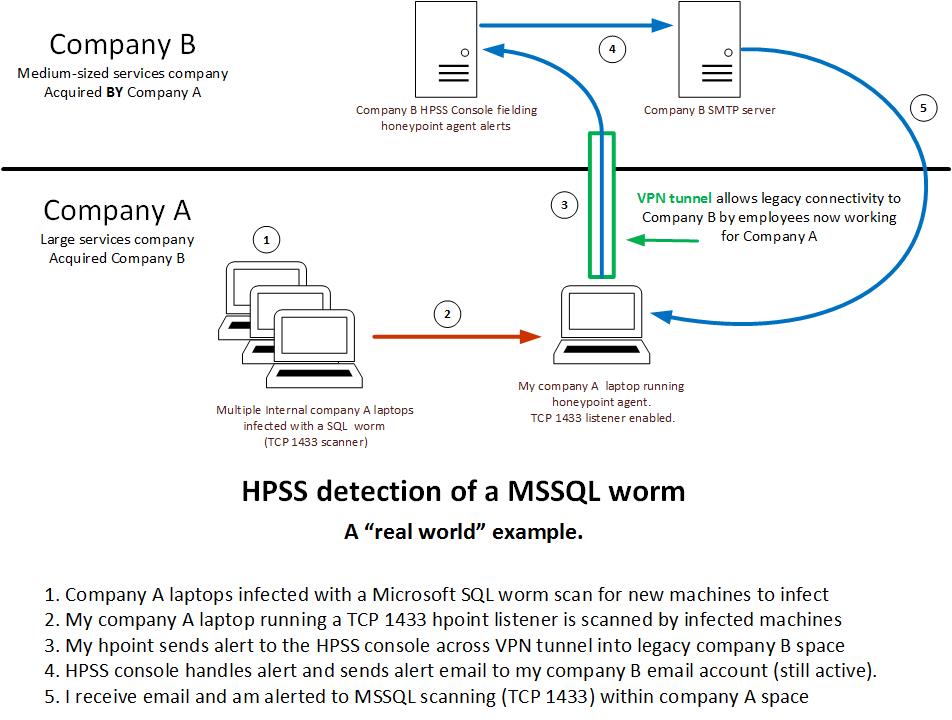
After a few months, the events shown in the diagram below occurred.
I started to receive email alerts directed to my Company B legacy email account. The alerts described TCP 1433 scans that my Company A laptop was receiving. The alerts were all being thrown by the MSSQL (TCP 1433 – Microsoft SQL Server) HoneyPoint listener on my laptop.
I was confused – partly because I had become absorbed in post-acquisition activities and had largely forgotten about the HPSS agent running on my laptop.
After looking at the emails and realizing what was happening, I got on the HPSS console and used the HPSS event viewer to get details. I learned that the attackers were internal within Company A space. Courtesy of HPSS I had their source IP addresses and the common payload they all delivered. Within Company A I gathered information via netbios scans of the source IPs. The infected machines were all Company A laptops belonging to various non-technical staff on the East Coast of the U.S.
All of that got passed on to the Company A CIO office. IDS signatures were generated, tweaked, and eventually the alerts stopped. I provided payload and IP information from HPSS throughout the process.
I came away from the experience with a firm belief that company laptops, outfitted with HoneyPoint agents, are an excellent way of getting meaningful detection out into the field.
I strongly recommend you consider something similar. Your organization’s company laptops are unavoidably on the front-line of modern attacks.
Use them to your advantage.