A friend on a road-trip recently had an experience using hotel wifi that was a little surprising. For several hours, while on the hotel’s wifi, her machine was effectively on the open Internet with no intervening firewall,
Her laptop was instrumented with one of MSI’s “honeypoints“, a lightweight honeypot that emulates various services and reports back to a central console when these “fake” services are interacted with, possibly by an attacker.
Over the several hour period while on wifi, the following Internet probes (and in some cases clear attacks) were seen.
The attacker IP and the port probed are in bold below:
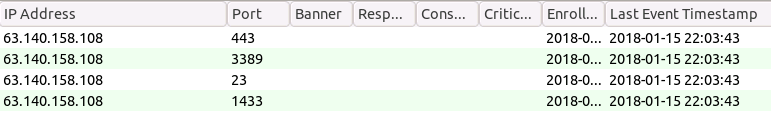
- Jan 15 18:03:43 HPSS012 HPSS Agent: Tarsus.local received an alert from: 198.20.87.98 on port 443 at 2018-01-15 18:03:42 Alert Data: Connection Received ==> https probe
- Jan 15 18:03:49 HPSS012 HPSS Agent: Tarsus.local received an alert from: 198.20.87.98 on port 443 at 2018-01-15 18:03:48 Alert Data: GET / HTTP/1.1#015#012Host: 63.140.158.108#015#012#015
- Jan 15 18:03:49 HPSS012 HPSS Agent: Tarsus.local received an alert from: 198.20.87.98 on port 443 at 2018-01-15 18:03:48 Alert Data: Non-ASCII Data Detected in Received Data.#012 File saved as Alert2215.txt
- Jan 15 18:23:02 HPSS012 HPSS Agent: Tarsus.local received an alert from: 181.214.87.7 on port 3389 at 2018-01-15 18:23:02 Alert Data: Non-ASCII Data Detected in Received Data.#012 File saved as Alert2216.txt ==> Terminal services probe from Sweden
- Jan 15 20:06:21 HPSS012 HPSS Agent: Tarsus.local received an alert from: 209.126.136.7 on port 443 at 2018-01-15 20:06:20 Alert Data: Connection Received
- Jan 15 20:06:29 HPSS012 HPSS Agent: Tarsus.local received an alert from: 209.126.136.7 on port 443 at 2018-01-15 20:06:28 Alert Data: Non-ASCII Data Detected in Received Data.#012 File saved as Alert2217.txt
- Jan 15 20:20:36 HPSS012 HPSS Agent: Tarsus.local received an alert from: 189.219.71.36 on port 23 at 2018-01-15 20:20:35 Alert Data: cat /proc/mounts; (/bin/busybox BBFMC || ) ==> Port 23 (telnet) IOT attack from Mexico. Likely from a Mirai botnet variant.
- Jan 15 20:26:22 HPSS012 HPSS Agent: Tarsus.local received an alert from: 8.3.123.42 on port 1433 at 2018-01-15 20:26:21 Alert Data: Non-ASCII Data Detected in Received Data.#012 File saved as Alert2218.txt ==> Microsoft SQL Server probe from Guam
- Jan 15 20:26:22 HPSS012 HPSS Agent: Tarsus.local received an alert from: 8.3.123.42 on port 1433 at 2018-01-15 20:26:22 Alert Data: Connection Received
- Jan 15 20:26:33 HPSS012 HPSS Agent: Tarsus.local received an alert from: 8.3.123.42 on port 1433 at 2018-01-15 20:26:32 Alert Data: Non-ASCII Data Detected in Received Data.#012 File saved as Alert2219.txt
- Jan 15 22:03:44 HPSS012 HPSS Agent: Tarsus.local received an alert from: 198.199.113.84 on port 1433 at 2018-01-15 22:03:43 Alert Data: Non-ASCII Data Detected in Received Data.#012 File saved as Alert2220.txt ==> SQL Server probe from U.S.
These alerts were being reported to the console from the IP address assigned by the hotel to my friend’s laptop: 63.140.158.108
That IP is registered to:
NetRange: 63.140.128.0 – 63.140.255.255
CIDR: 63.140.128.0/17
NetName: WAYPORT-63-140-182-NET
Wayport is an ATT wifi service providing “hotspots” to various large companies.
These are the types of probes and attacks a box on the open Internet can expect to get. It’s become like cosmic radiation – pervasive. I discussed a previous related event here: https://stateofsecurity.com/?p=4126
What is interesting in this case is the fact they happened at all.
The hotel was part of a major chain. The common assumption is they are watching out for their guests to ensure a “safe” wifi environment…and in general they are.
But – there maybe some fine print.
Some hotel wifi agreements apparently specifically allow you to request “advanced” connectivity options, in some cases as a result of wanting to do VPN from your laptop. The result of those decisions may lead to a public Internet address and full Internet exposure of your device .
So – no Internet firewall but the one you bring with you.
Bottom Line:
- Regardless of the cause, you should expect the worst from “free” wifi.
- Assume full Internet exposure and have a software firewall enabled that blocks unsolicited inbound traffic.
See:
- https://conetrix.com/blog/public-ip-addresses-and-hotels
- https://superuser.com/questions/1063910/public-ip-given-at-a-hilton-hotel
- http://www.corecom.com/ccftp/Testing_Hotspot_Security.pdf
Quote from that last:
“Most private LANs use network firewalls to defend trusted insiders against Internet-borne attacks.This is not necessarily true in hotel broadband LANs, where topologies and security practices vary widely.For example, some use private IP addressing, while others assign each user their own public IP address to facilitate VPN tunneling. Users may assume they are insulated from outsiders, but really have no idea whether any firewall lies between
their notebook and the Internet. Notebooks that do not firewall themselves or that use certain applications that open holes in firewalls could thus be exposed to intrusions from the far side of the Internet.”