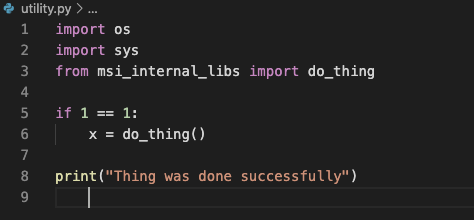
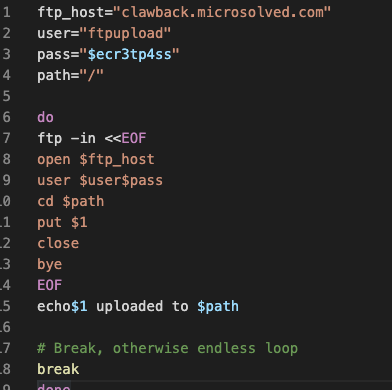
It’s been about a month since we released Clawback, and we’ve received some good feedback. Others are asking how works and how it can help them? So, I’ve set up a small demonstration just to show how it would work in a couple scenarios that we’ve seen before.
Example 1.
A developer, contractor or other internal user erroneously uploads some internal code that either has sensitive data, or just shouldn’t be publicly exposed. We’ve seen this happen several ways, where the uploader didn’t realize they uploaded to a public repository, they uploaded a lot of internal utility scripts but didn’t realize 1 or 2 of them had sensitive data, or somebody asks for help on a forum but didn’t sanitize the code in question well enough.
The one thing you must do when setting up your monitoring terms in Clawback, is figure out exactly what to monitor. We’ve designed it where you enter common pieces of information, unique strings that might appear in your code (variable names, libraries, usernames etc). Let’s see how that works
This contrived example might be from a web application or some other application developed in house. We can see that at the top we’re using a library that probably only exists internally, so if this shows up anywhere publicly it means something has been leaked.
Here is a script that might be used internally for uploading files somewhere on a regular basis. We have less to go on here, the username is pretty generic. There is a hostname here though.
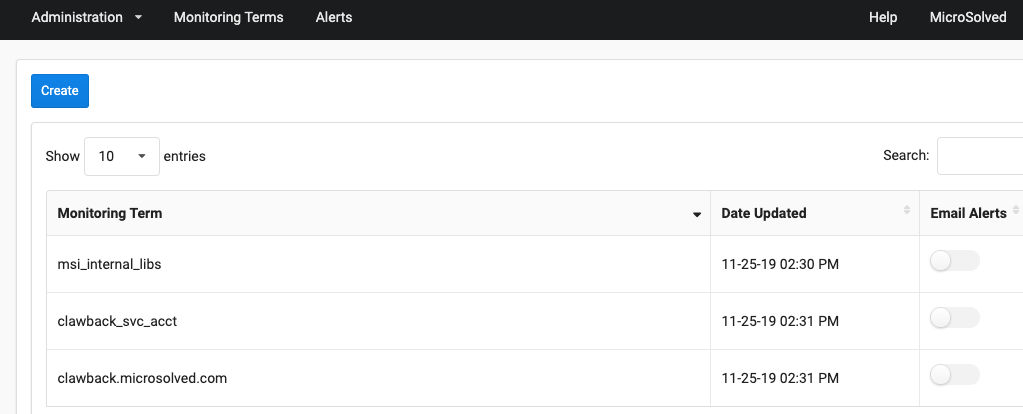
For our last example, we look through our domain for unique user accounts, and we have found one named “clawback_svc_acct”.
Setting up the Monitoring Terms
Before I get to the actual set up, a small funny story. I was setting up the demo files late at night, uploaded to github. First thing the next morning, Brent (our CEO) tells me he got an alert in Clawback and linked me to the repository I had uploaded the night before, and making sure it was me that put it there.
We’ve set up our 3 monitoring terms here. Simple to do, you just click “create”, enter your unique string, and choose if you want email alerts or not.
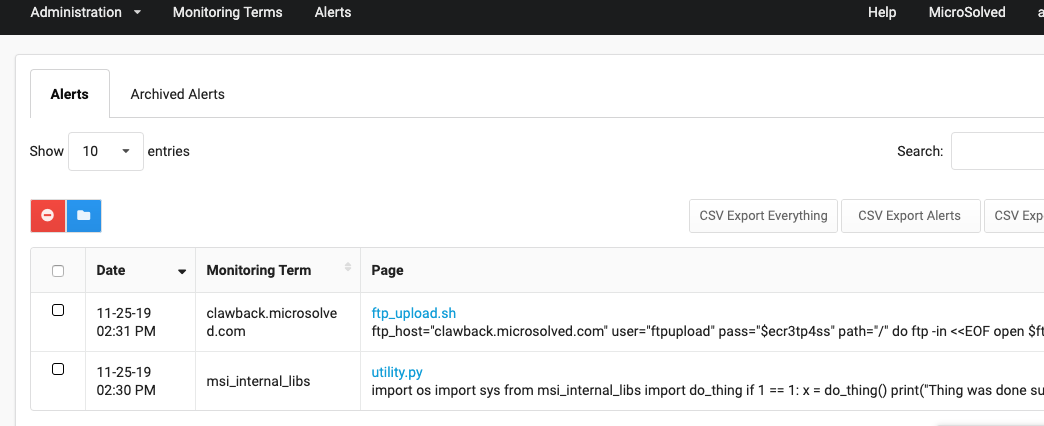
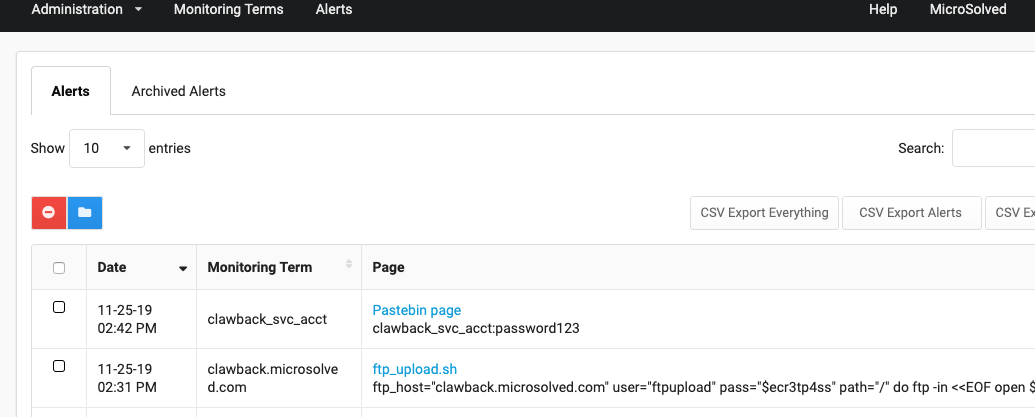
Immediately, we can go to the alerts tab and see we have 2 alerts. What happened is as soon as you enter a new term, Clawback does a historical search to identify anything already existing that matches your terms. After that it goes in to “monitor mode” and continuously monitors for any new matches.
It comes up with the github repository I had created previously, with a direct link to the matching files and a small snippet of whats in it, around the matching term.
https://github.com/adamhos/cbdemo/blob/5647b81f9a7289e66f6a838e68d81a5201d062ea/ftp_upload.sh
https://github.com/adamhos/cbdemo/blob/5647b81f9a7289e66f6a838e68d81a5201d062ea/utility.py
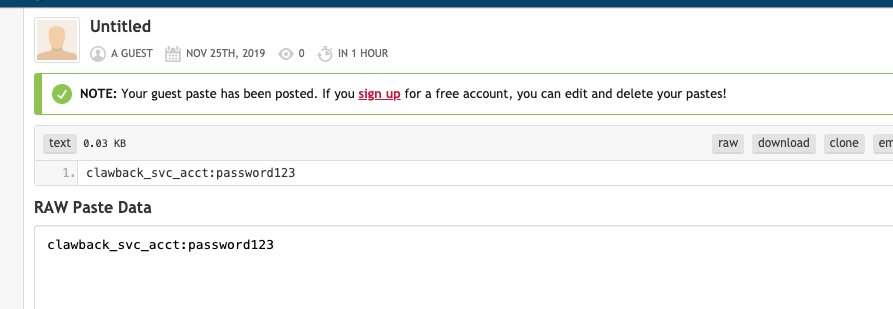
Nothing came up for the username we entered. Let’s put a “leak” in pastebin and see what happens.
After a few minutes we are alerted that the monitoring term “clawback_svc_acct” matched something. We go to view it and see the pastebin “leak”, with a link to it and the relevant content.
I hope that answers some questions, and gives you an idea of what you can monitor with Clawback. If you have any questions, comments or would just like to talk more about it you can reach us at info@microsolved.com, or catch me on twitter @adamhos