As I mentioned in my last post (Datacenter Attack Surfaces), I’d like to take some time to discuss the basics of “Egress Filtering“.
Egress = “the action of going out of or leaving a place“. In the context of controlling information flow within a datacenter, egress filtering is the practice of examining, and potentially denying, outbound communication to external networks such as the Internet. The topic is discussed in the Wikipedia article on Egress Filtering, an article I have helped maintain.
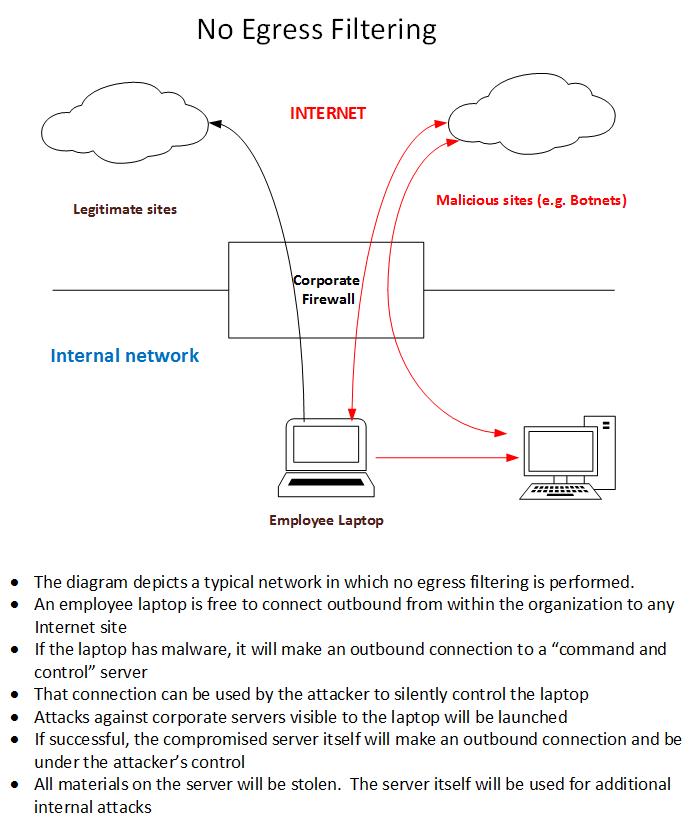
Here is a diagram that shows the type of environments I typically encounter that have no egress filtering. The risks are illustrated.
Employee laptops go home to an environment beyond your control. Regardless of your “end-point” security, a subset of those laptops will be compromised and under the control of attackers. That control will be re-asserted the minute the laptop fires up within your organization and makes that unfiltered outbound connection. The diagram above shows what can – and does, in my experience – happen.
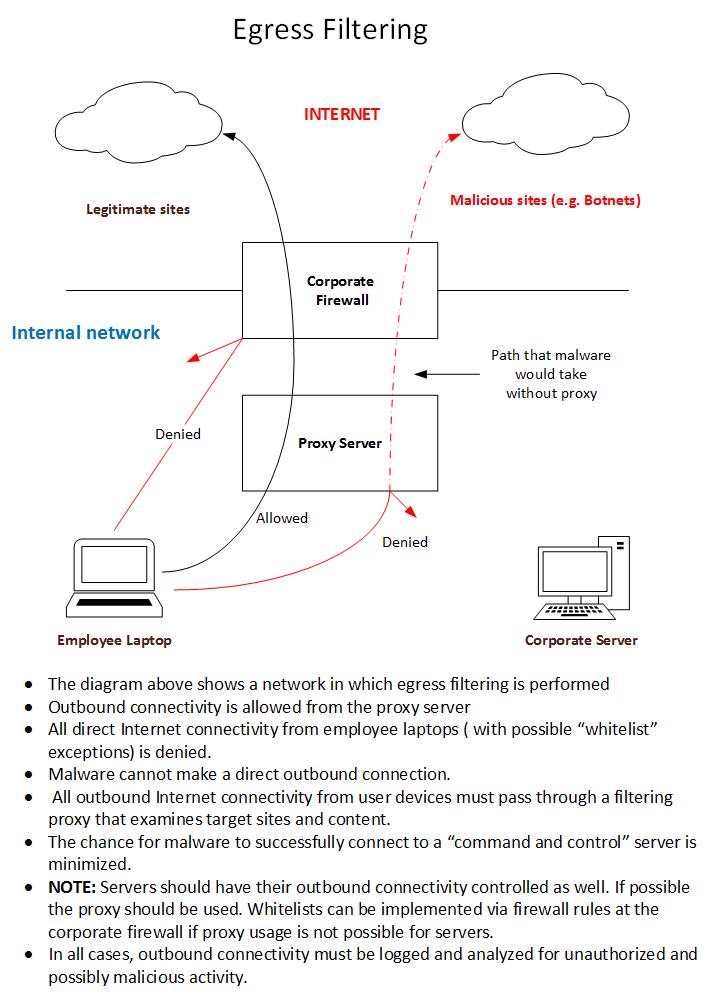
The next diagram shows an environment with egress filtering in place.
Egress filtering as depicted above has a chance of minimizing the potential impact to your organization from a compromised laptop. By tightly controlling outbound access and paying strict attention to denied attempts you will be able to quickly zero in on a subset of your compromised internal machines.
Various proxy or “content filtering” solutions exist that will satisfy the basic requirements for an intermediary device that examines outbound connection attempts. An open-source Squid proxy alone can blunt the effect of much malware. More elaborate (and costly) commercial solutions exist that can update restrictions in real-time based on malware events being reported globally.
Finally, as discussed in the “Datacenter Attack Surfaces” post, try to limit the network visibility your core servers have from the vantage point of your employee’s machines. That will limit the ability of a compromised laptop being used as a attack platform against your datacenter.
Minimizing your internal attack surfaces and controlling egress gives you a fighting chance against modern malware. If you have trouble convincing management that the cost and effort is worth it, get in contact with us. We can help you make the case.
Good luck… and as always: Watch your logs!
References:
- http://en.wikipedia.org/wiki/Content-control_software
- http://en.wikipedia.org/wiki/Proxy_server
- http://en.wikipedia.org/wiki/Squid_(software)
- http://www.sans.org/reading-room/whitepapers/firewalls/performing-egress-filtering-32878
- http://www.darkreading.com/attacks-breaches/tech-insight-how-to-defend-against-zeus/227600055

Egress Filtering http://t.co/55YOtnNx0h