One of the SANS topics discussed in March and early April caught my attention recently:
See:
Quote from the link:
“Update:Just found what looks like a bitcoin miner on the infected DVR. There are two more binaries. D72BNr, the bitcoin miner (according to the usage info based on strings) and mzkk8g, which looks like a simplar http agent, maybe to download additional tools easily (similar to curl/wget which isn’t installed on this DVR by default). I will add these two files to https://isc.sans.edu/diaryimages/hikvision.zip shortly.
Last week, we reported that some of the hosts scanning for port 5000 are DVRs (to be more precise: Hikvision DVRs, commonly used to record video from surveillance cameras [1] ).”
Basically what is claimed is that compromised video equipment (HIKVISION) is scanning TCP 5000 looking for network attached storage devices (SYNOLOGY) that have a flaw: http://www.scip.ch/en/?vuldb.10255
And also – that the compromised video equipment has had bitcoin mining software installed. Nice touch.
I have an Internet-facing honeypoint listening on TCP 5000 – I did it out of curiosity.
Got this within 30 minutes
satori received an alert from 177.206.XXX.XXX at 2014-03-31 18:18:45 on port 5000 Alert Data: GET /webman/info.cgi?host= HTTP/1.0 Host: 71.XXX.XXX.XXX:5000 User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1) Content-Type: application/x-www-form-urlencoded Content-Length: 0
Then I took a look at: 177.206.XXX.XXX ( IP is in Brazil )
PORT STATE SERVICE
21/tcp open ftp
23/tcp open telnet
443/tcp open https
554/tcp open rtsp
990/tcp open ftps
8001/tcp open vcom-tunnel
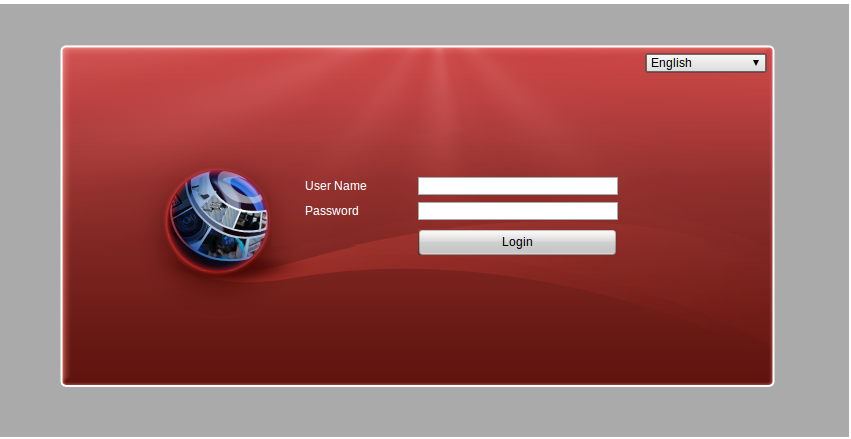
Screenshot of the site – below:
Here is the html source for the page:
<!DOCTYPE html PUBLIC “-//W3C//DTD XHTML 1.0 Strict//EN”
“http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd”>
<html>
<head>
<title></title>
<meta http-equiv=”Content-Type” content=”text/html; charset=utf-8″>
<link rel=”stylesheet” href=”../css/base.css” type=”text/css” />
<link rel=”stylesheet” href=”../css/login.css” type=”text/css” />
<script type=”text/javascript” src=”../script/jquery-1.7.1.min.js”></script>
<script type=”text/javascript” src=”../script/jquery.cookie.js”></script>
<script type=”text/javascript” src=”../script/login.js”></script>
<script type=”text/javascript” src=”../script/common.js”></script>
<script type=”text/javascript” src=”../script/Translator.js”></script>
</head>
<body onload=”initLogin()”>
<div id=”container”>
<div>
<div>
<select id=”LanguageSelect” name=”LanguageSelect” onchange=”changeFrameLanguage(this.value)”></select>
</div>
<div>
<div>
<span>
<label id=”lausername” name=”lausername”></label>
</span>
<span>
<input type=”text” id=”loginUserName” maxlength=”16″ />
</span>
</div>
<div>
<span>
<label id=”lapassword” name=”lapassword”></label>
</span>
<span>
<input type=”Password” id=”loginPassword” maxlength=”16″ />
</span>
</div>
<div>
<span></span>
<span onclick=”doLogin()” onmousemove=”this.className=’loginbtnon'” onmouseout=”this.className=’loginbtn'”>
<label id=”lalogin” name=”lalogin” ></label>
</span>
</div>
</div>
</div>
<!–<div>
<label name=”laCopyRight”>©Hikvision Digital Technology Co., Ltd. All Rights Reserved.</label>
</div>–>
</div>
</body>
</html>
Bingo – so I have a confirmed case of compromised video equipment in Brazil scanning my home Internet IP for a vulnerability affecting NAS storage devices.
Small world, no?
This was genuinely fun for me as it allowed me to take an interesting but somewhat remote piece of the constant security news-stream and render it immediate and real – that was MY IP being scanned.
BTW: Does your organization have video equipment with exposed interfaces on YOUR Internet perimeter? Many of you do… and don’t know it.

http://t.co/epcGNYTpYx
Video equipment scanning for SAN devices: http://t.co/epcGNYTpYx