Recently, ISC Diary posted this story about Snort 2.9.2 now supporting SCADA protocol checks. Why is this good news for SCADA?
Because it is a lower cost source of visibility for SCADA operators. Snort is free and a very competitive solution. There are more expensive commercial products out there, but they are more difficult to manage and have less of a public knowledge base and tools/options than Snort. Many security folks are already familiar with Snort, which should lower both the purchase and operational cost of this level of monitoring.
Those who know how to use Snort can now contribute directly to more effective SCADA monitoring. Basically, people with Snort skills are more prevalent, so it becomes less expensive to support the product, customize it to their specific solution and manage it over time. There are also a wide variety of open source add-ons, and tools that can be leveraged around Snort, making it a very reasonable cost, yet powerful approach to visibility. Having people in the industry who know how the systems work and who know how Snort works allows for better development of signatures for various nefarious issues.
It is likely to be a good detection point for SCADA focused malware and manual probes. The way these new signatures are written allows them to look for common attacks that have already been publicly documented. The tool should be capable of identifying them and can do so with ease. In terms of trending malware, (not currently) these attack patterns have been known for some time.
The specifics of the probes are quite technical and we would refer readers to the actual Snort signatures for analysis if they desire.
By learning the signatures of various threats to the industry, people in the field can translate that into Snort scripts which can detect those signatures on the network and make the proper parties aware in a timely manner. Snort has the flexibility (in the hands of someone who knows how to use it) to be molded to fit the needs of nearly any network.
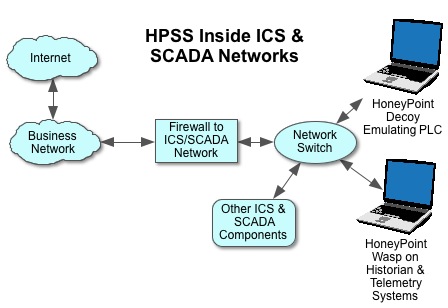
It makes an excellent companion tool to a deployment of HoneyPoint deep inside SCADA and ICS networks. In this case, Snort is usually deployed on the internal network segment of the ICS/SCADA firewall, plugged into the network switch. HPSS is as shown.
If you’re looking for a low-cost solution and plenty of functionality for your SCADA, this recent development is a welcome one!

Snort and SCADA Protocol Checks:
FB.Event.subscribe(‘edge.create’, function(response) {
_gaq.push([‘… http://t.co/2ua6qXmh