Threat modeling is a powerful technique that helps characterize higher level threats and separates them into more manageable sub-threats that can be addressed. Threat modeling can help an organization discover the core issue that lies beneath a high level threat, such as a denial of service (DoS).
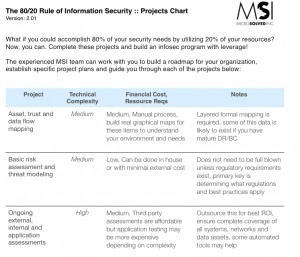
There are different approaches toward threat modeling. One is to examine an existing application. The other is to evaluate a threat during every stage of the software development lifecycle (SDLC). With our “80/20 Rule of Information Security” project list, we tackle what regulations apply to your company and assess the risks.
For instance, let’s say a regulation requires strong access control measures to be in place. A high-level threat would be when a malicious user escalates privileges. In order to do this, the user would need to bypass the authentication process. With a Risk Management Threat Modeling Project, MSI would analyze the applications to find alternate entry points in order to harden them and ensure that only authorized users have access.
What is important is discovering where threats exist and then developing security solutions to address them. MSI also examines data flow diagrams that charts the system. Once we see the data flows, we can then start looking for vulnerabilities.
We use the STRIDE approach, which stands for: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. With each phase, we carefully examine all of the loopholes that could leave your company’s data exposed. For instance, “spoofing” is pretending to be something you’re not. Many attackers use email to send notices to individuals that may look as though it was coming from a reputable source (like PayPal) but a quick look at the link address would prove otherwise. These attacks now have a name: phishing.
No business wants a Denial of Service. This happens when an attack overloads your server with fake requests so that it crashes the system. MSI’s HoneyPoint Security Server is an excellent way to prevent such attacks from happening.
Tampering attacks can be directed against static data files or network packets. Most developers don’t think about tampering attacks. When reading an XML configuration file, for example, do you carefully check for valid input? Would your program behave badly if that configuration file contained malformed data? These are some of the questions to consider when analyzing for risk.
MSI can help you achieve a more secure posture. Why not give us a call today?