The mathematician as extortionist: ransomware “smart” contracts
Source: https://en.wikipedia.org/wiki/Brazen_head
A few weeks ago I wrote about the “proof of work” concept inherent in the implementation of the blockchain used to support bitcoin. I have continued down the blockchain path and have been exploring another child of the blockchain revolution: Ethereum.
Ethereum is a blockchain that has its own cryptocurrency (“ether”) which is in many ways similar to bitcoin.
But – Ethereum has something else: “smart contracts” that are effectively programs that can execute on the “Ethereum Virtual Machine” (EVM).
The EVM is just what the name implies – a distributed computing environment made up of the various computers supporting the Ethereum blockchain. Smart contracts are programs typically written in Ethereum’s “Solidity” programming language and then compiled into code that lives on the blockchain itself. Once deployed, they can be interacted with by end users who pay for that interaction using ether.
The end user sends the ether to the contract from their Ethereum “wallet“. If sufficient funds are sent, the contract executes on the EVM and performs the contractual obligations. The contract owner (or his designates) gets the ether, the user gets the good or services.
Users can be given a copy of the solidity program that describes the contract and can validate that the deployed contract matches the code. With a knowledge of Solidity, they can (hopefully) assure themselves of how it will behave when they pay.
So imagine instead of a lawyer reviewing a traditional written contract you would employ a programmer/lawyer to review the Solidity contract.
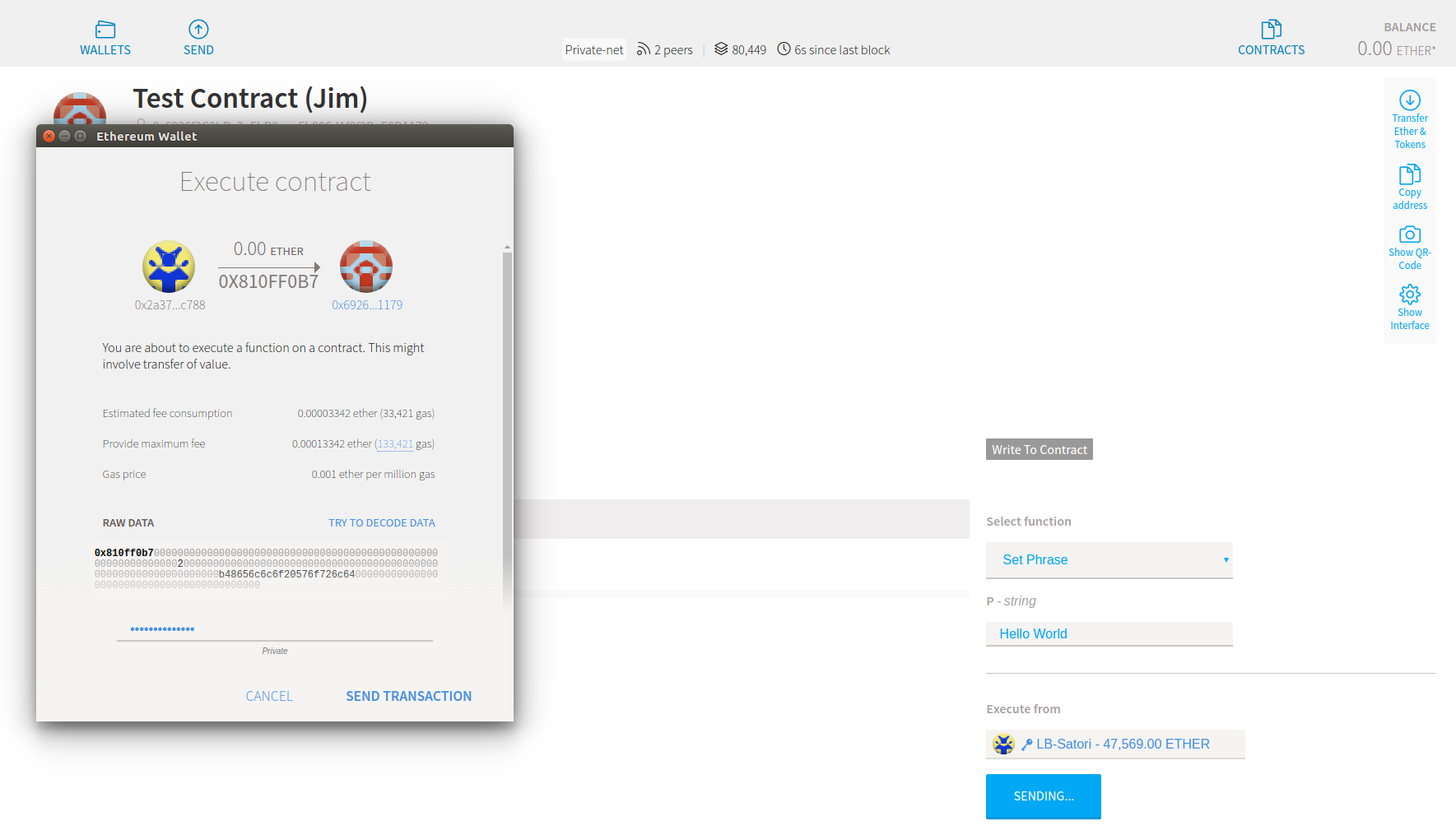
We run a test Ethereum blockchain environment at MicroSolved which I have taken advantage of to write smart contracts and see them in action. I have used the “Mist” wallet application to interact with that test environment.
Here is a simple “hello world!” example. It has only two functions:
- Set a phrase displayed to the user interacting with the contract.
- Display the current phrase.
Here is my interaction with the contract. I am authorizing the transfer of funds (0 in this test case) to allow me to set the returned phrase to “Hello World!”
Using a test instance of a blockchain explorer application (“Etherchain Light“) I can watch my transaction being added to the test chain after validation by “miner” nodes: 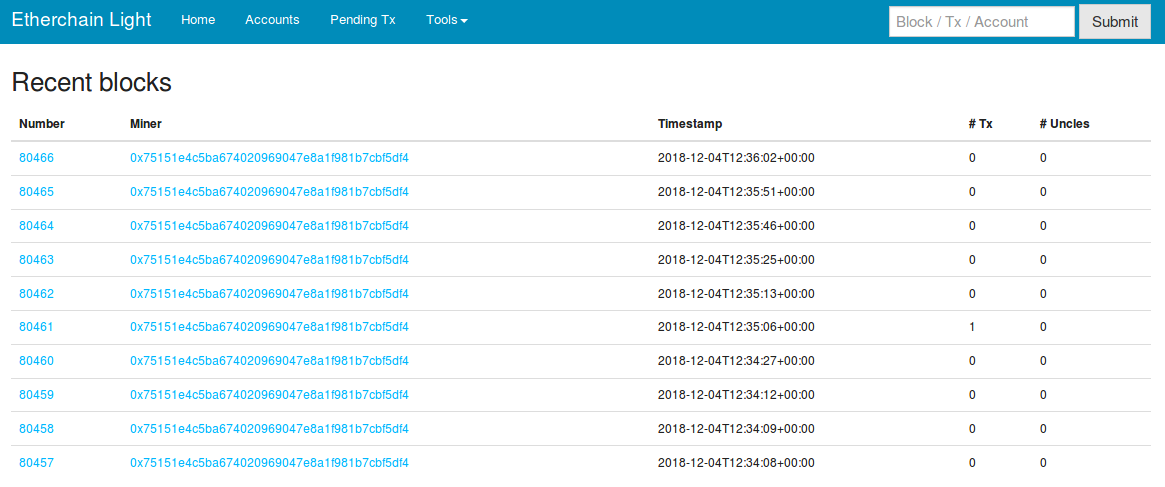
And after validation I can interact with contract and see my new phrase has been set.
Actual smart contracts can be highly complex, interact with other contracts, and even potentially interact with other blockchains.
So now for the ransomware angle…..
Smart contracts are often described as a way to establish trust between actors who have no basis for that trust. Quoting from Investopedia:
“…smart contracts permit trusted transactions and agreements to be carried out among disparate, anonymous parties without the need for a central authority, legal system, or external enforcement mechanism. They render transactions traceable, transparent, and irreversible.”
So the immediate question came to my mind:
“Can smart contracts be used to facilitate ransomware?
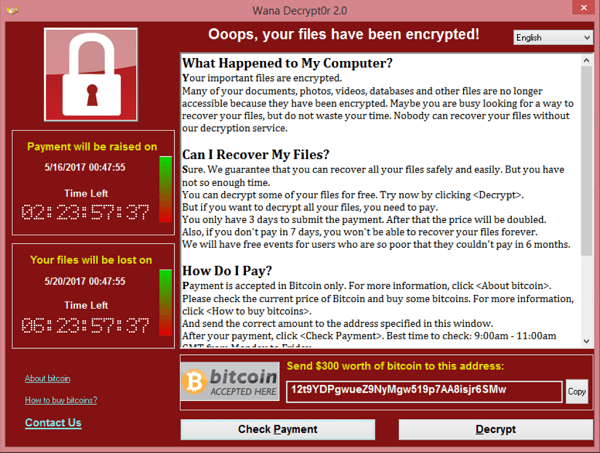
In ransomware attacks a victim has had critical files encrypted by malware, typically as a result of clicking on malicious content in a phishing email. The malware displays a ransom demand with payment instructions on the victim’s machine. Often that payment is via cryptocurrency:
Source: https://en.wikipedia.org/wiki/File:Wana_Decrypt0r_screenshot.png
The victim has no real guarantee that they will be able to decrypt their files even after paying the ransom. They have to evaluate that risk against the cost of restore from backup (if they even have backups) or simply the business cost of losing the data.
Reportedly, only 19% of victims do receive what they need to recover their data. Most pay and get nothing.
Establishing trust between the victim of a ransomware attack and the attacker such that the victim can be assured of decrypting the files and the attacker assured of receiving payment seems like the “holy grail” of smart contracts.
So… I went looking and found there is a significant amount of literature on the topic, and even a very good YouTube video by Jorn Erbguth entitled: Smart Contracts for Ransomware.
The video gives a good sense of the dynamics and ecosystem that would (do?) surround ransomware contracts, but it seems the author is glossing over some of the details that might forever consign such ransomware contracts to the realm of unicorns.
Ideally the victim should have complete trust that the key he is paying for will in fact unlock his shuttered kingdom. I’m not seeing that…. but that may be perhaps because of the cloud of mathematics that arises when you start to do the serious reading.
An example is the inevitable descent into the topic of “Zero Knowledge Proofs“, defined as “… a method by which one party (the prover) can prove to another party (the verifier) that they know a value x, without conveying any information apart from the fact that they know the value x.”
So – I have the decryption key and I can prove it such that you’ll trust me enough to send me money to get it. Sounds like the right stuff for the basis of a actual ransomware smart contract, no?
Here’s an excerpt from the Wikipedia article on the topic:
There’s no “google translate” for that (yet).
My point here is that all “proofs” of the validity of smart contracts and the underlying blockchain environments that support them are essentially abstruse mathematical proofs accessible only to a fairly small audience of “cryptographic engineers“.
I suspect that even for members of that esoteric community a certain amount of religious faith in their discipline is required to convince themselves they really do know how many “angels dance on the head of a pin“.
Still, smart contracts for ransomware seems like an inevitability, in the same way that the continued rise of blockchain technologies as part of the background infrastructure of our daily lives seems inevitable. Those mathematical ecosystems may be employed by both good and bad actors, but they will ultimately be “understood” by only a limited number of specialists.
So when that unicorn of a smart contract eventually comes calling at your door with a demand for money, be aware that behind the scenes and at some distance the supporting extortionist is a mathematician (or at least thinks they are).
Question: Have you been the victim of a ransomware smart contract? MicroSolved would love to hear about it. Give us a call.
See:
- Overview and discussion: https://randomoracle.wordpress.com/2017/06/17/designing-honest-ransomware-with-ethereum-smart-contracts-part-i
- A cryptographer’s crystal ball: https://blog.cryptographyengineering.com/2017/02/28/the-future-of-ransomware
- Zero Knowledge Proofs: https://blog.cryptographyengineering.com/2014/11/27/zero-knowledge-proofs-illustrated-primer/
- Formal Verification of Smart Contracts: https://www.cs.umd.edu/~aseem/solidetherplas.pdf
- The Ring of Gyges: Using Smart Contracts for Crime: http://www.arijuels.com/wp-content/uploads/2013/09/Gyges.pdf “
- Explain Like I’m 5: Zero Knowledge Proof: https://hackernoon.com/eli5-zero-knowledge-proof-78a276db9eff
If you would like to know more about MicroSolved or its services please send an e-mail to info@microsolved.com or visit microsolved.com.