Over the years, phishing campaigns have evolved from crude HTML forms to shockingly convincing impersonations of the web infrastructure we rely on every day. The latest example Adam spotted is a masterclass in deception—and a case study in what it looks like when phishing meets full-stack engineering.
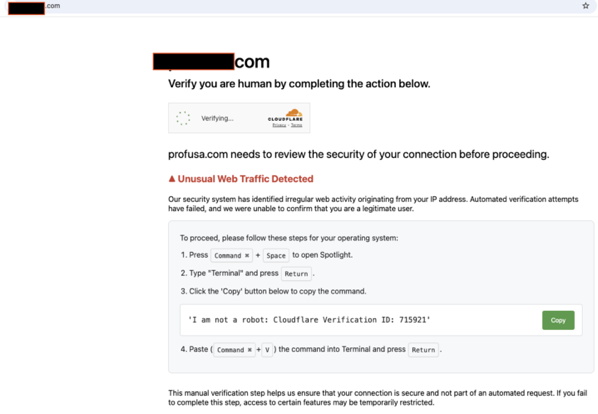
Let’s break it down.
The Setup
The page loads innocuously. A user stumbles upon what appears to be a familiar Cloudflare “Just a moment…” screen. If you’ve ever browsed the internet behind any semblance of WAF protection, you’ve seen the tell-tale page hundreds of times. Except this one isn’t coming from Cloudflare. It’s fake. Every part of it.
Behind the scenes, the JavaScript executes a brutal move: it stops the current page (window.stop()), wipes the DOM clean, and replaces it with a base64-decoded HTML iframe that mimics Cloudflare’s Turnstile challenge interface. It spoofs your current host into the title bar and dynamically injects the fake content.
A very neat trick—if it weren’t malicious.
The Play
Once the interface loads, it identifies your OS—at least it pretends to. In truth, the script always forces "mac" as the user’s OS regardless of reality. Why? Because the rest of the social engineering depends on that.
It shows terminal instructions and prominently displays a “Copy” button.
The payload?
Let that sink in. This isn’t just phishing. This is copy-paste remote code execution. It doesn’t ask for credentials. It doesn’t need a login form. It needs you to paste and hit enter. And if you do, it installs something persistent in the background—likely a beacon, loader, or dropper.
The Tell
The page hides its maliciousness through layers of base64 obfuscation. It forgoes any network indicators until the moment the user executes the command. Even then, the site returns an HTTP 418 (“I’m a teapot”) when fetched via typical tooling like curl. Likely, it expects specific headers or browser behavior.
Notably:
-
Impersonates Cloudflare Turnstile UI with shocking visual fidelity.
-
Forces macOS instructions regardless of the actual user agent.
-
Abuses clipboard to encourage execution of the curl|bash combo.
-
Uses base64 to hide the entire UI and payload.
-
Drops via backgrounded
nohupshell execution.
Containment (for Mac targets)
If a user copied and ran the payload, immediate action is necessary. Disconnect the device from the network and begin triage:
-
Kill live processes:
-
Inspect for signs of persistence:
-
Review shell history and nohup output:
If you find dropped binaries, reimage the host unless you can verify system integrity end-to-end.
A Lesson in Trust Abuse
This isn’t the old “email + attachment” phishing game. This is trust abuse on a deeper level. It hijacks visual cues, platform indicators, and operating assumptions about services like Cloudflare. It tricks users not with malware attachments, but with shell copy-pasta. That’s a much harder thing to detect—and a much easier thing to execute for attackers.
Final Thought
Train your users not just to avoid shady emails, but to treat curl | bash from the internet as radioactive. No “validation badge” or CAPTCHA-looking widget should ever ask you to run terminal commands.
This is one of the most clever phishing attacks I’ve seen lately—and a chilling sign of where things are headed.
Stay safe out there.
* AI tools were used as a research assistant for this content, but human moderation and writing are also included. The included images are AI-generated.
