“Healthcare…the only industry where employees are the predominant threat actors in breaches.” Straight out of Verizon’s 2017 Data Breach Investigations Report, p.22. No, no, no, you can’t lock out all your employees completely from the hospital network; The nurse needs to get to my medical profile to know what and how much of a drug dose to give me.
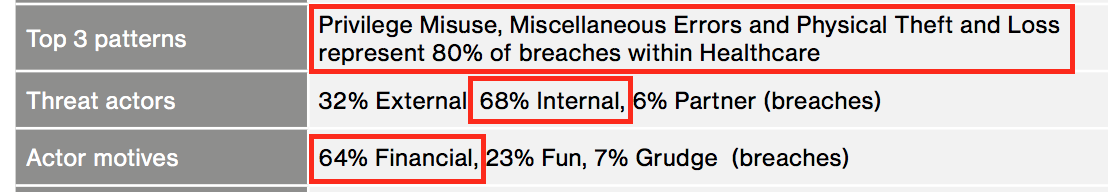
The healthcare industry has to balance between securing large amounts of private and sensitive data, yet allow quick access to it for doctors and nurses, emergency and healthcare personnel. 68% of threat actors within healthcare are from internal, and 64% of all incidents and breaches are financially motivated. And 80% of breaches are due to abuse of privileges, physical theft or loss and miscellaneous errors 1.
* The above image captured from Verizon’s 2017 Data Breach Investigations Report, p.22
Internal threat actors could be:
- An insider looking up an admitted celebrity’s address or a family member’s diagnosis report.
- A nurse texting or emailing another nurse a patient’s lab results for convenience.
- Mis-delivery of a patient file from emailing or faxing to a wrong destination through a simple transposition of 2 letters/numbers.
- A doctor checking into a patient’s progress from her home computer and leaves the logged on information onscreen and steps away to check on dinner.
- An insurance agent discloses a little too much information when pressed on by a “client’s son”. (I’ve used that line in a social engineering phone call phishing exercise for a client before and it worked)
- Really bad actors driven by financial gains, such as identity theft or tax or credit fraud.
No, we’re not blackballing the healthcare professionals, the overwhelming majority are caring, self-sacrificing, altruistic professionals. The healthcare industry includes so many other sub-industries involving subcontractors, vendors and numerous other 3rd parties. The flow of information is so vast and often time-sensitive, the abuse of access from a couple bad apples can expose data for a large number of patients.
Malicious, altruistic, careless or just simple human error, PII and PHI can and does end up in unauthorized hands. Policies, education, staff training, firewalls, filters, scanners, domain group policies, encryption, audits, imposing fines on violators – all steps to help mitigate an attack surface.
There are numerous issues and methods for mitigation, too many for this blog. Up for discussion, access controls. Minimizing or completely eradicating unauthorized access to protected information.
Display of private information left on screen where unauthorized eyes may come across. Most institutions have policies for screen saver locks or automated log off after a short set time. That does not stop BYOD, home or other remote devices access to the same private information because these features were not configured. Shared computers at home or a work laptop left logged on with information on screen are an easy and common target. What is your institution’s policy on non-company managed devices having access to protected information?
Should a nurse be able to access all patients’ records in the hospital? Should his access be limited to those under his care, his floor, his department…? What about file shares within the network; are access controls configured properly to prevent one authenticated user from accessing another’s files (we come across such a misconfiguration often)?
How about network segmentation? Should the administrative assistant in the hospital be able to see the imaging device in radiology over the hospital network? Even if access controls are configured adequately preventing unauthorized access to files in the system, vulnerabilities can exist where a malicious actor who has gained access to a front desk computer station can launch an attack on a host over the private network and cause a denial of service.
Sometimes there’s no easy answers in the form of technical controls. Some staffers do need access to patient data for the proper execution of their job. What are the lessons learned from the incident in Florida in 2013, when an emergency room staffer sold motor accident patient data to an attorney 2? No role-based access controls can prevent a bad apple from taking a phone photo of a patient’s data while he was in the middle of completing his assigned task.
Numerous technical controls can and should be implemented to protect our data: strong access controls should be in place. Users should only be allowed access to data they need to have access to. Role-based access controls is one way. Access to other parties, 3rd party vendors, shared access with other practitioners should be granted with deliberate and discriminate determination.
Even after it has been granted, access should be audited and evaluated on a regular basis. Monitoring of access should be also logged and evaluated. Can the data be removed from the internal network, shared with other staffers, copied, printed, emailed, etc. – all should be considered and can be technically managed. Network segmentation where access between certain groups of users or devices should be implemented.
The health care industry definitely should be up to task and be responsible with the vast amount of sensitive information they have collected from us. I often vacillate between “they’re responsible and professionals, and have things under control” and sleepless nights of “what’s the point of having unique strong passwords for all my online accounts.”
Accidents do happen but anyone with access to our information should care about our data as much as they care for the patients themselves,
If you would like to know more about MicroSolved or its services please send an e-mail to info@microsolved.com or visit microsolved.com.
Resources:
1 https://www.verizonenterprise.com/resources/reports/2017_dbir_en_xg.pdf
2 https://www.observeit.com/blog/throwback-thursday-fl-hospital-worker-caught-selling-patient-data/