Data breaches from stolen or lost laptops are in the news far too often. And you know it happens even more often off the news. MicroSolved’s recommendation for field laptops that may contain databases with sensitive and personal information is to encrypt the data or entire volume. Using the BitLocker feature on Windows is one such solution.
Continue reading
Author Archives: Johnny Chuah
People Like to Fish. Statistics Show They Tend to be Phished.
Several paths led me to a blog on this topic. I have a friend and a close relative who are currently going through a home loan process. In addition, in a work-related project, I have been researching mortgage fraud and real estate scams. Statistics reveal about 1% of loan applications contained an element of fraud, and it has been on a general upward trend for the last decade.
Continue reading
IoT. Is one called an Internet of Thing?
In several recent engagements, we came across some IoT (Internet of Things) devices within client networks. There’s a growing presence of these ubiquitous devices within corporate environments. They measure, they detect, they capture, they sense. Then they send the info to some app on your phone.
These devices make life easier. Safer. More convenient. Many times, just simply accessible when it was not possible before.
But there can be risks. I’ve always held the belief that security has an inverse relationship with accessibility. The more doors you have to enter a building, the more accessible it is to get inside. But with this accessibility to authorized persons with keys to the doors, likewise, the risk for a burglar to pick the locks to break in increases.
Continue reading
Business IT and Security Staffing
Several months ago, MSI was called for an incident response. The business was under a denial of service attack (DoS). They had no internet connectivity. They had no phone service. They were under attack.
Compliance
In a previous blog on healthcare information access concerns, I had expressed concerns for internal origins for data breaches. Further research to help mitigate some of these concerns has led to an observation that many data breach incidents could be funneled to a few common origins. The intent for sharing below some of the more unusual or high profile cases is to drive home the point that it really does happen in real life. And passive awareness of regulatory controls are not enough; active exercising and use of in-place policies is necessary.
Be it intentional, malicious or accidental HIPAA information disclosure, information leak occurs. Continue reading
The Weakest Link is…
2018 was a record year. But not in a good way. U.S. organizations paid out a record $28 million in settlements or judgments for data breaches 1. That number was boosted by Anthem’s $16 million settlement for the largest healthcare breach in history.
But information security is getting better, isn’t it? Alright, fines for the year is not reflective of the number of data breaches for the same year, after all, the actual breaches for the fines mentioned above occurred years prior. Such as, the Anthem cyber-attack occurred in 2014 and 2015 2, and the $4.3 million judgment against the University of Texas MD Anderson Cancer Center occurred in 2012 and 2013.
In the Protenus 2019 Breach Barometer Report 3, the U.S.Department of Health and Human Services HHS reported 503 health care data breaches that compromised over 15 million patient records. That is up from 2017 of 477 data breaches with 5.5 million patient records. A 5% increase in number of breaches resulted in triple the number of patient records compromised.
How data was compromised varied from stolen/lost credentials, unauthorized insider access, “hacking” from an external source, human error, and phishing. One of the most common vector for intrusion comes through 3rd party vendors.
Continue reading
Complex Does Not Equal Strong
Another year, and again, another annual report (this one from SplashData) lists the easy and bad passwords have remained relatively unchanged.
As a domain network administrator, you may not be terribly concerned. You think you have a robust password policy as well as an account lockout policy to prevent brute force attacks. Your users cannot use any of those simple passwords on that list. No simple guessing a password is going to let an attacker into your network. Think again.
Most corporate domain password policies require complex passwords with a minimum password length. Many implement a minimum password length of 7 through 10, and with most password complexity rules, passwords should contain characters from 3 of 4 categories: uppercase, lowercase, numerals and special characters. Often times, the password is also restricted from containing the account name as well.
Continue reading
Healthcare information access concerns
“Healthcare…the only industry where employees are the predominant threat actors in breaches.” Straight out of Verizon’s 2017 Data Breach Investigations Report, p.22. No, no, no, you can’t lock out all your employees completely from the hospital network; The nurse needs to get to my medical profile to know what and how much of a drug dose to give me.
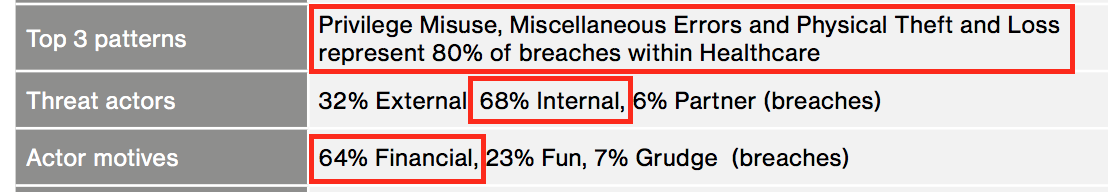
The healthcare industry has to balance between securing large amounts of private and sensitive data, yet allow quick access to it for doctors and nurses, emergency and healthcare personnel. 68% of threat actors within healthcare are from internal, and 64% of all incidents and breaches are financially motivated. And 80% of breaches are due to abuse of privileges, physical theft or loss and miscellaneous errors 1.
* The above image captured from Verizon’s 2017 Data Breach Investigations Report, p.22
Internal threat actors could be:
Encrypt That Drive
Promise me you’ll return to this blog piece, but go ahead and open a new tab and search for “stolen laptop.” Filter the search results for a specific year. Or refine the search within an industry, eg. healthcare or financial. Too many results. Too many incidents. The U.S. Department of Health and Human Services, Office for Civil Rights, has a breach portal – https://ocrportal.hhs.gov/ocr/breach/breach_report.jsf – only incidents involving more than 500 PHI records are in the database. Search for theft of laptop.
They Price It Right! Come on down…
Healthcare from United States, come on down! Welcome to “They Price It Right!” There goes the industry, high-fiving all the other industries in the studio as it rushes towards Drew Carrey and the stage. And pays the ransom.
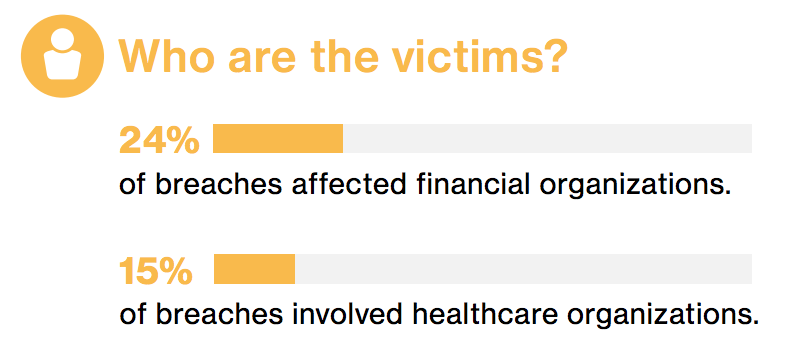
In 2017, healthcare organizations accounted for 15% of all security incidents and data breaches, second only to financial institutions (from Verizon’s 2017 DBIR). 66% of malware was installed through either email links or attachments. The healthcare industry has also been hard hit with ransomware in recent years.
* The above images captured from Verizon’s 2017 Data Breach Investigations Report
The last several years have seen a dramatic increase in ransomware within healthcare. To quote the CEO of an organization that DID pay out the ransom demand, “These folks have an interesting business model. They make it just easy enough. They price it right.” Symantec’s ISTR on Ransomware 2017 reports the average ransom demand “appears to have stabilized at US$544 indicating attackers may have found their sweet spot.” Ahhh…can just picture the blackmailer getting a notification that their target had succumbed and paid up…that hit the sweet spot.
However, a reminder; a $500 ransom may not seem much to an organization with millions or billions in revenue, but that’s per infection (sorry, pun not intended as we’re discussing the healthcare industry). Dozens or hundreds of infection can easily tally up the ransom to total in the tens or hundreds of thousands.
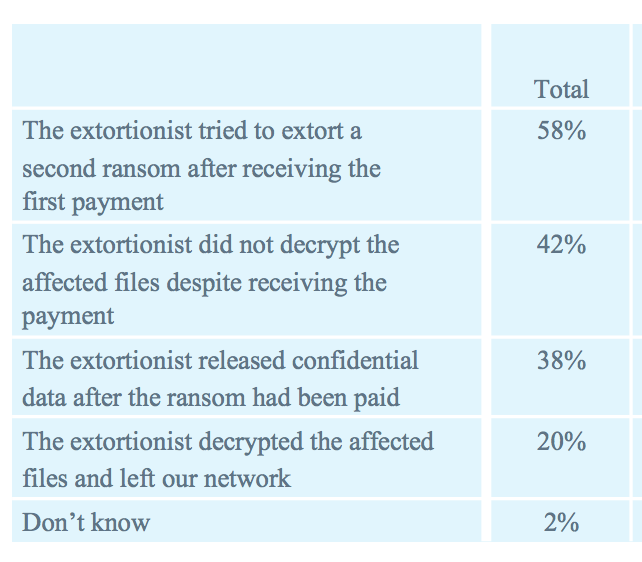
Furthermore, paying the sweet spot ransom does not guarantee even a bittersweet outcome. SentinelOne’s 2018 Ransomware Study shows 42% of ransom payments did not result in data recovery. 58% demanded a second payment.
* The above image captured from SentinelOne’s Global Ransomware Study 2018
Most ransomware is delivered through email. Phishing. Spearphishing. Targeted targets. Email addresses for an organization can easily be harvested using readily available open source tools. 15 minutes to create a phishing campaign with the newly found targets with a link or malicious attachment. The context of the email can be social media related, user needs to reset their password, they have a package that was undelivered, the CEO has attached a memo addressed to all staff. The recent Russian indictments – regardless of the reader’s political leanings – are proof that PHISHING WORKS! (Also blogged here in stateofsecurity.com)
Technology has come a long way – email filters, domain verification, Sender Policy Framework, malware and link scanners – plus many more help in filtering out the 50-70% of the email traffic that is spam. But they still get through. I know for one my Inbox is not spam-free or devoid of any phishing messages.
Since technology is not at the point where it’s able to stop all phishing email, it is up to the user to NOT click on that link or attachment. Sure, there are technologies that prevent bad things from happening if a user DOES click on a phishing link or malicious attachment. But then again, technology is not at the point where they are 100% effective.
Businesses with big budgets buy all kinds of hardware and software solutions to try to counter phishing. But they ignore a big piece of the phishing attack model, and that is the end user. And here, education and training is imperative.
Repeating phishing exercises should be conducted on all or selected groups of employees. These campaigns should be at not-too-regular intervals, so as not to evoke an anticipation from the employees – alright, here come some vaguely suspicious email on the first day of each quarter; I’ll just delete them. Then the rest of the year, they blatantly open, view and click on any and all email links. The simulated campaigns should be randomized and as unexpected as possible.
These campaigns should also be followed up with some education, either some static web pages, training video or live in person session. Phishers are always coming up with new tricks and methods. As a result, end users should be brought up to speed with their new tricks. A couple academic research papers on the efficacy of phishing training demonstrate that EDUCATION WORKS! (links under Resources below)
Then there needs to be a culture of non-retribution. Phishing exercises should be conducted with learning as the objective. Employees should come away with a heightened awareness of phishing and the social engineering tricks used by phishers that make you just want to click that link/attachment.
Employees should be encouraged to report any suspicious email so that word gets around. Homeland Security’s “See something, say something” campaign applies here too; someone is perhaps targeting your firm, alert your fellow colleagues.
Resources:
https://www.verizonenterprise.com/resources/reports/2017_dbir_en_xg.pdf
https://go.sentinelone.com/rs/327-MNM-087/images/Ransomware%20Research%20Data%20Summary%202018.pdf
https://www.healthcaredive.com/news/must-know-healthcare-cybersecurity-statistics/435983/
https://www.symantec.com/content/dam/symantec/docs/security-center/white-papers/istr-ransomware-2017-en.pdf
https://blog.barkly.com/phishing-statistics-2016
http://www.cs.cmu.edu/~jasonh/publications/apwg-ecrime2007-johnny.pdf
https://www.usenix.org/system/files/conference/soups2017/soups2017-lastdrager.pdf
https://www.dhs.gov/see-something-say-something/about-campaign
If you would like to know more about MicroSolved or its services please send an e-mail to info@microsolved.com or visit microsolved.com.