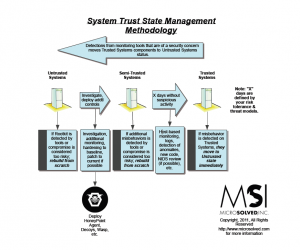
A lot of folks have written in asking for a simple methodology overview of how to use the spreadsheet we published in a previous post. Here is a quick and dirty overview of the methodology we use to manage the security trust state of systems in our work. Check out the diagram and let us know if you have any questions or feedback.
Thanks for reading and we hope this helps your team in a meaningful way! Click to enlarge image. Click here to downlaod the PDF.