If you’re unfamiliar with the term “OSINT” (open-source intelligence) it boils down to finding information that’s publicly and freely available about you, your company or anything else. How can this help you? OSINT covers a very broad array of sources and uses, and one way it can be used is to help verify your external network surfaces, and if user emails have been found in datadumps from compromised sites.
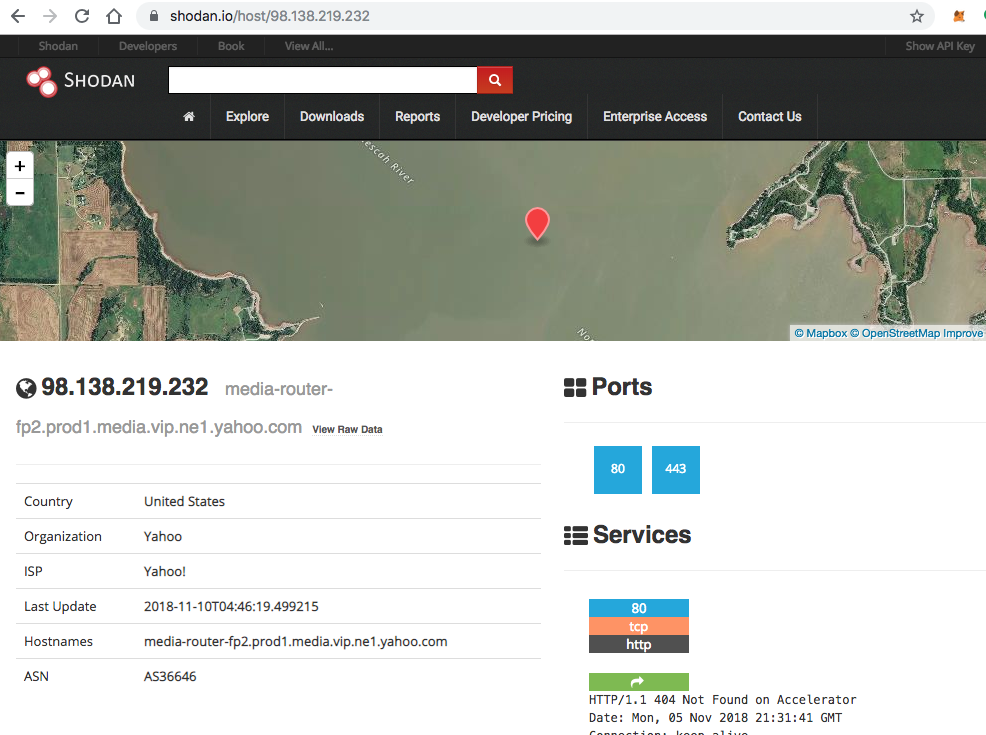
For checking external exposures Shodan is a goto site. Think of it like Google for looking up services available on a host instead of words available on a website.
You can see here this particular IP has services running on 80 (HTTP) and 443 (HTTPS). This site is very handy for sanity checking your exposures and verifying what’s really available from your IPs. Keep in mind though that Shodan does not probe every port, only a subset, so don’t rely on this information alone.
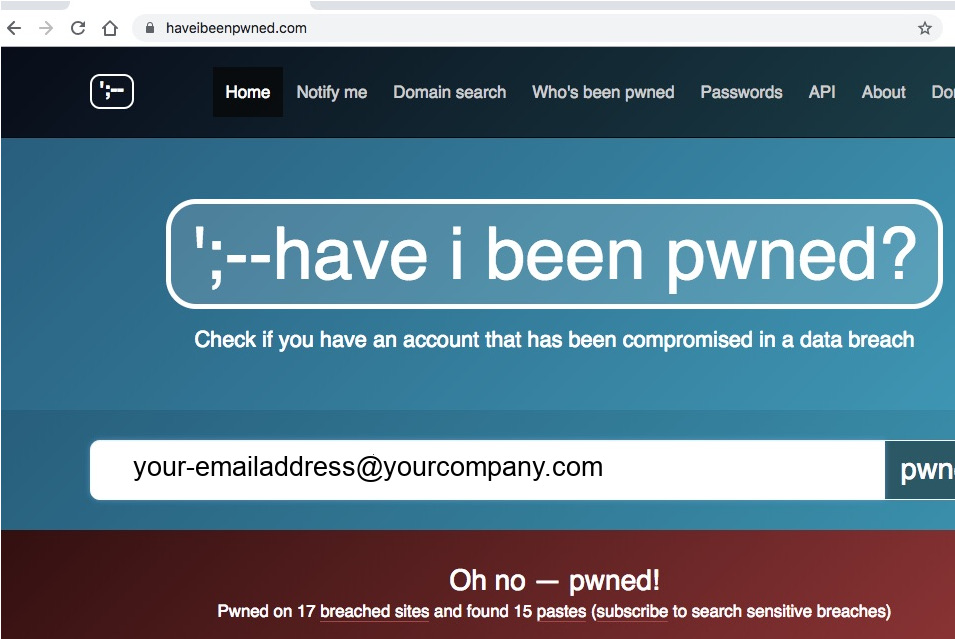
Another useful site is “have i been pwned”. This site lets you search a large catalogue of compromised accounts for your or any employees addresses. In some cases it can also tell you the site that was breached that resulted in the exposure of the credentials.
It’s a good idea to make sure everyone is aware that they shouldn’t use the same password between multiple sites, but if you find corporate email addresses in a recent breach it might be wise to reset account passwords and monitor those accounts for login attempts on external resources.
Armed with some OSINT knowledge, you can quickly check external exposures and if corporate emails have shown up in compromised data. One thing to remember about OSINT though, the source is only as good as the data it gets. so it’s easy for things to slip by, and thus shouldn’t be relied on as a sole source of truth.