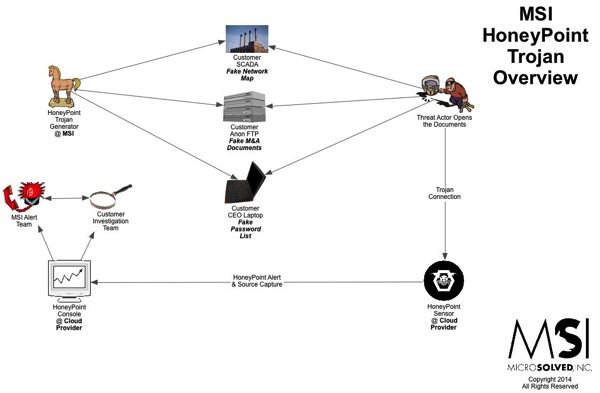
Here’s another quick overview graphic of how HoneyPoint Trojans work. We have been using these techniques since around 2008 and they are very powerful.
We have incorporated them into phishing exercises, piracy studies, incident response, intrusion detection, intelligence gathering, marketing analysis and even privacy research. To hear more about HoneyPoint Trojans, give us a call.
If the graphic below is blurry on your device, you can download a PDF version here.

HoneyPoint Trojans Overview http://t.co/UKy1vkRtT4 #infosec #honeypoint #trojan
HoneyPoint Trojans Overview | MSI :: State of Security http://t.co/mn6Weno6Uf <One of my favorite parts of HPSS, since 2008
HoneyPoint Trojans Overview | MSI :: State of Security http://t.co/WmxiY0yewt <Trojans are my favorite part of HoneyPoint
HoneyPoint Trojans Overview | MSI :: State of #Security http://t.co/FKmNNtNOZR <I love trojans, just as effective for defense as penetration