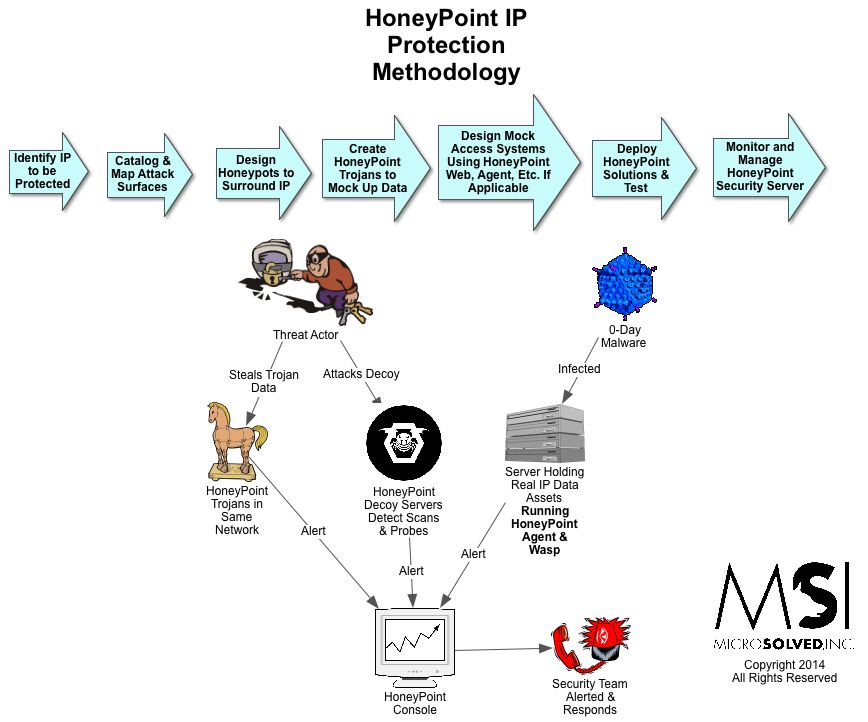
Here’s another use case scenario for HoneyPoint Security Server. This time, we show the methodology we use to scope a HoneyPoint implementation around protecting a specific set of Intellectual Property (IP).
If you would like an in-depth discussion of our process or our capability, please feel free to reach out to us and schedule a call with our team. No commitment and no hard sale, guaranteed.
If the graphic below is blurry on your device, you can download a PDF version here.

HoneyPoint IP Protection Methodology | MSI :: State of #Security http://t.co/KNMZYqUUY7 <How to use HPSS to protect IP, great stuff!
HoneyPoint IP Protection Methodology | MSI :: State of #Security http://t.co/TVGB6wZ3Fc <This is how we do it… 🙂 #honeypot
HoneyPoint IP Protection Methodology | MSI :: State of #Security http://t.co/P0FjQuw6rf <How to use HPSS to protect IP, great stuff!
RT @lbhuston: HoneyPoint IP Protection Methodology | MSI :: State of #Security http://t.co/P0FjQuw6rf <How to use HPSS to protect IP, great…
HoneyPoint IP Protection Methodology | MSI :: State of #Security http://t.co/iO31NHUCow <This is how we do it… 🙂 #honeypot