As I referred to earlier, our team has been doing some research on popular content management systems and potential security vulnerabilities in them. We were doing this as a part of a review of the Syhunt Sandcat4PHP product that our partner has released.
As a part of that project, we have identified significant vulnerabilities in each of the popular content managers we reviewed. Several of the products were found to have various types of injection vulnerabilities (SQL/command/etc.), arbitrary file disclosure and access issues and tons of cross-site scripting (XSS) problems. We are now in the process of notifying each of the product teams about the vulnerabilities we identified.
How bad were things? One word, abysmal…
Here is an inside glimpse of the raw math of the scanning tool’s findings:
CMS Injections & File Issues XSS “Risk Rating”
==================================================
Bitweaver 37 7 42.25
Drupal 97 2 98.50
Joomla 4 15 15.25
Mambo 45 207 200.25
WordPress 5 166 129.50
** The “risk rating” was based upon each injection and file issue being given a score of 1.0 and each XSS being given a score of .75, then adding them together. It should be noted that this was an arbitrarily chosen mechanism created to give a simple basis for comparison and is NOT reflective of any specific risk rating system or the like. Also, no general weighting or anything is included, so I use the term “risk” loosely…
I also dropped the data into InspireData, a quick and dirty visualization tool I like to play with. It produced these quick images (Note that you can download them for a clearer view):
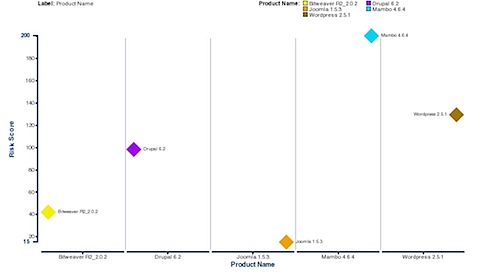
This graph shows a plot of the “risk score” by the product tested.
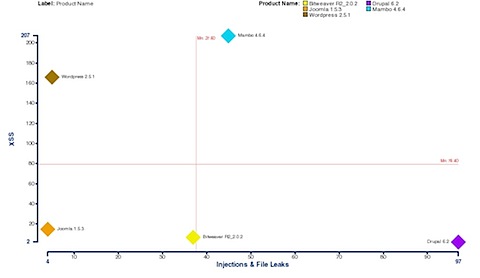
This graph shows a matrix of the products plotted across an axis for Injections and File Leaks and an axis for XSS. Interestingly, the red lines show the mean values of the plot just for a quick reference.
As I said before, our team is in the process of contacting each of the CMS projects that we tested and will be disclosing the vulnerability information to them for their mitigation. Our team did some basic testing and analysis on the data that the Syhunt tool found and determined it to be pretty good at finding the issues. We found very few false positives, and the ones we did find were areas where other functions are involved in testing inputs beyond the initial layer of the source code.
The Syhunt tool did very well. It is a great tool for a 1.00 release and very much worth the cost. If you have PHP and javascript applications in your environment, I would suggest grabbing your team a copy. If you have applications that you would like tested by a third party, please feel free to contact us for a quote. Let us know if we can be of any assistance or if you have questions about what we did or the like.
Please note that we will NOT be making disclosures of the identified vulnerabilities at this time, so don’t ask. We will be working with the project teams to mitigate any vulnerabilities identified.
Note that all products were downloaded from public sources and are “open” projects. Versions were current as of the download date. We only scanned the source of core products, no plugins/add ons/expansions or modules outside of the core products were tested in this project. Your paranoia may vary and you should not take any of the results of these tests as advice or endorsement of any of these projects or products. Use the results at your own risk…… 😉
