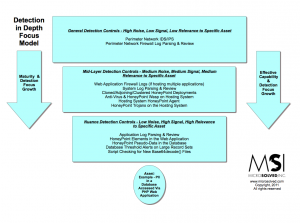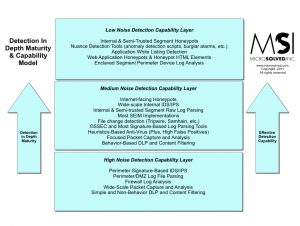
I have been discussing the idea of doing detection depth pretty heavily lately. One of the biggest questions I have been getting is about maturity of detection efforts and the effectiveness of various types of controls. Here is a quick diagram I have created to help discuss the various tools and where they fit into the framework of detection capability versus maturity/effectiveness.
The simple truth is this, the higher the signal to noise ratio a detection initiative has, the better the chance of catching the bad event. Detections layered together into various spots work better than single layer controls. In most cases, the closer you get to an asset, the more nuanced and focus (also higher signal to noise ratio) the detection mechanisms should become.
That is, for example – a tool like a script detecting new files with “base64decode()” in them on a web server is much higher signal than a generic IDS at the perimeter capturing packets and parsing them against heuristics.
When the close controls fire an alert, there better be a clear and present danger. When the distant controls alert, there is likely to be more and more noise as the controls gain distance from the asset. Technology, detection focus and configuration also matter A LOT.
All of that said, detection only works if you can actually DO something with the data. Alarms that fire and nothing happens are pretty much useless tools. Response is what makes detection in depth a worthwhile, and necessary, investment.