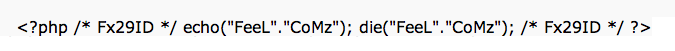Recently, I found another new mutation of a PHP bot infector, with zero percent detection by anti-virus software. There was an anti-security tool code included, as well.
Recently, I found another new mutation of a PHP bot infector, with zero percent detection by anti-virus software. There was an anti-security tool code included, as well.
For those interested, you can view this link to see that the total number of anti-virus detections was 0.
However, when I decoded the PHP backdoor, I got 17 anti-virus hits on it. It seems they locked into the c99 backdoor code remnants, which is a pretty old backdoor PHP trojan. This leads to the question about evasion techniques and how effective anti-virus applications are at doing code de-obfuscation. For example, if you want a currently effective AV evasion technique in PHP, it comes down to this simple line of code: (gzinflate(str_rot13(base64_decode($code)))); – There’s the cash money key in terms of evading most, if not all, current anti-virus tools.
However, if you have a process that runs grep against your files looking for base64_decode and alerts you to new ones, you’ll get visibility to it and many, many others like it. Base64 encoding is still quite a popular call in PHP attack and compromise tools.
Here are some examples of this specific trivial control — here, and here. Now you have a real life example of how it pays off. So simple, yet so effective at detecting these slippery backdoors.
Finding specific nuance controls that pay off against specific threats to your assets is a key way to better security. It’s a win, all around!