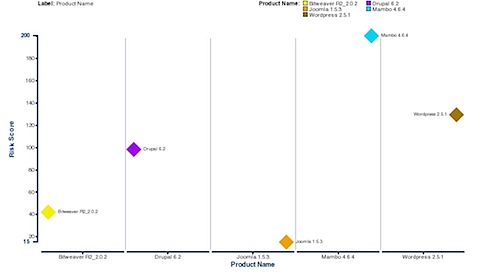
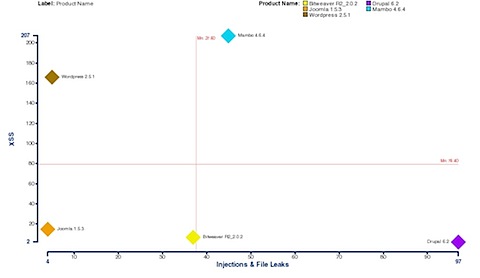
OK, now we have some more bad news on the DNS front. There have been new developments along the exploit front that raise the bar for protecting DNS servers against the cache poisoning attacks that became all the focus a few weeks ago.
A new set of exploits have emerged that allow successful cache poisoning attacks against BIND servers, even with the source port randomization patches applied!
The new exploits make the attack around 60% likely to succeed in a 12 hour time period and the attack is roughly equivalent in scope to a typical brute force attack against passwords, sessions or other credentials. The same techniques are likely to get applied to other DNS servers in the coming days and could reopen the entire DNS system to further security issues and exploitation. While the only published exploits we have seen so far are against BIND, we feel it is likely that additional targets will follow in the future.
It should be noted that attackers need high speed access and adequate systems to perform the current exploit, but a distributed version of the attack that could be performed via a coordinated mechanism such as a bot-net could dramatically change that model.
BTW – according to the exploit code, the target testing system used fully randomized source ports, using roughly 64,000 ports, and the attack was still successful. That means that if your server only implemented smaller port windows (as a few did), then the attack will be even easier against those systems.
Please note that this is NOT a new exploit, but a faster, more powerful way to exploit the attack that DK discovered. You can read about Dan’s view of the issue here (**Spoiler** He is all about risk acceptance in business. Alex Hutton, do you care to weigh in on this one?)
This brings to mind the reminder that ATTACKERS HAVE THE FINAL SAY IN THE EVOLUTION OF ATTACKS and that when they change the paradigm of the attack vector, bad things can and do happen.
PS – DNS Doberman, the tool we released a couple of days ago, will detect the cache poisoning if/when it occurs! You can get more info about our tool here.