This article builds on the What is HPSS? Series. The original overview article is here.
The HoneyPoint Security Server Console is the “brain” of the HoneyPoint product platform. It is the central component responsible for getting alert data from the sensors, tracking and maintaining the alert data, presenting it to the user and safely passing the essential alert data on to the automated plugins or other systems in the security event chain.
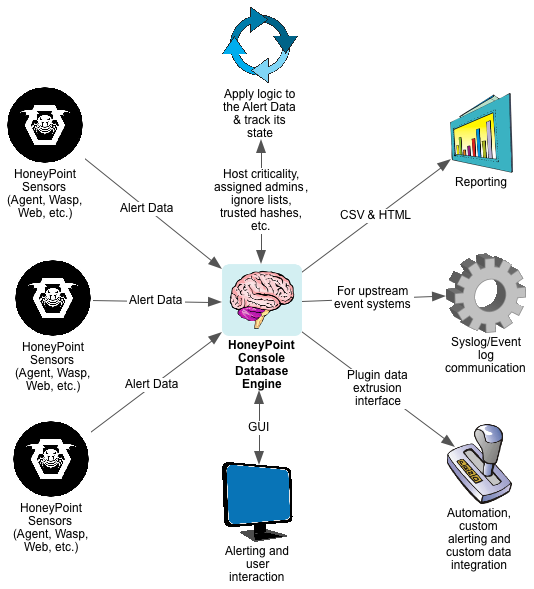
The Console is a GUI application that includes a built-in database engine for tracking Alert Data state and to empower reporting and analysis over time. Alert Data from the sensors are sent to the Console over TCP and the data is encrypted. The Console application runs on Windows, Linux and OS X.
Once the Console receives Alert Data from the sensors, it parses it to validate that the data is good and checks to see what actions it should take based on the alerting configuration, assigned admins list, ignored hosts lists, and other trust rules in place.
It then presents the alert data to the appropriate mechanisms, alerting users, passing the desired elements of the alert data to syslog/event log on the Console system for upstream processing by SEIMs or other event tools. The Console also passes certain event data as determined by the configuration into the “plugins mechanism”.
The plugins then execute the desired operations on the data, easily allowing the security team to further extend reporting to custom event handlers or perform automated responses. This flexible solution empowers the security team to integrate HoneyPoint Security Server fully into whatever technology platform/response process they desire or have in place.
Reporting from the Console is very simple. The included reporting engine can create a wide variety of canned reports in either CSV or HTML format, ensuing that the data in the HoneyPoint system is easy to use. Additionally, other reporting tools like Crystal Reports or the like, or even languages like PERL, Python or Ruby, can easily attach to the Console database to create whatever types of custom reports you desire.
All in all, HoneyPoint Security Server was designed to make it easy to use and yet flexible enough for the most demanding and mature infosec teams. The console interface is friendly, functional and easily understandable. Most teams require less than a 30 minute walk through before they are off and running with the basic detection power HoneyPoint provides. When they get comfortable with the system, they quickly master the plugins meta-language and are soon automating large groups of detection and response tasks.
To learn more about HoneyPoint Security Server or to get a demo, please contact us. We would be happy to walk you through the product and discuss how it might fit into your environment. There is even a free for personal use “Community Edition” available to get you started or to let you experience the power, ease and flexibility of the platform yourself. Just give us a call to learn more about HoneyPoint Security Server Console. You’ll be glad you did!







