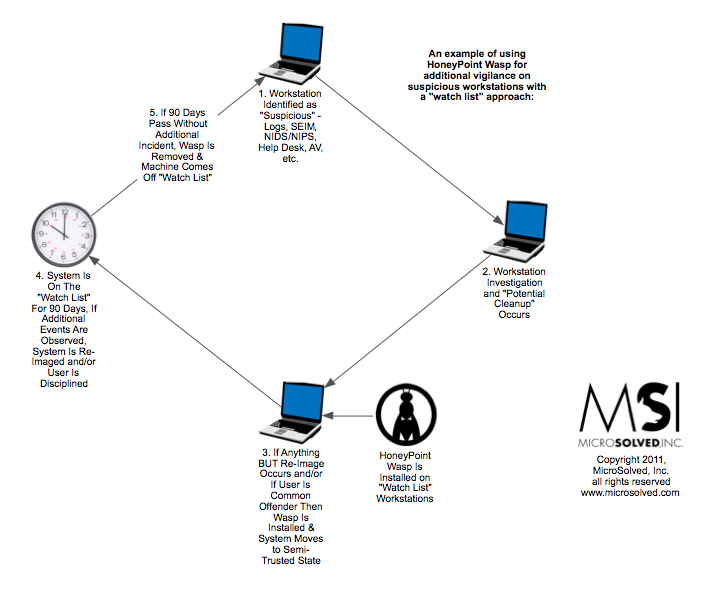
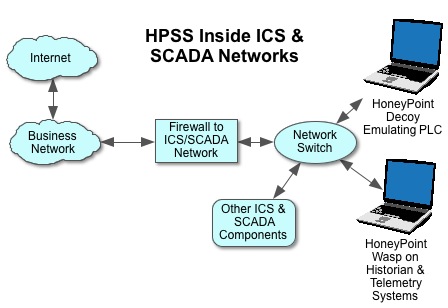
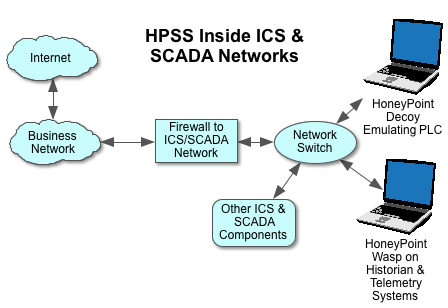
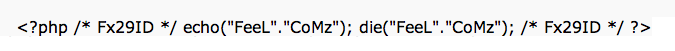Today, many sites are protesting PIPA/SOPA and the like. You can read Google or Wikipedia for why those organizations and thousands of others are against the approach of these laws. But, this post ISN’T about that. In fact, censorship aside, I am personally and professionally against these laws for an entirely different reason all together.
My reason is this; they will simply speed up the crime stream. They will NOT shut down pirate sites or illicit trading of stolen data. They will simply force pirates, thieves and data traders to embrace more dynamic architectures and mechanisms for their crimes. Instead of using web sites, they will revert to IRC, bot-net peering, underground message boards and a myriad of other ways that data moves around the planet. They will move here, laws will pass to block that, they will move there, lather, rinse and repeat…
In the meantime, piracy, data theft, data trading and online crimes will continue to grow unabated, as they will without PIPA/SOPA/Etc. Nary a dent will be made in the amount or impact of these crimes. Criminals already have the technology and incentives to create more dynamic, adaptable and capable tools to defy the law than we have to marshall against them in enforcing the law.
After all that, what are we left with? A faster, more agile set of criminals who will actively endeavor to shorten the value chain of data, including intellectual property like movies, music and code. They will strive to be even faster to copy and spread their stolen information, creating even more technology that will need to be responded to with the “ban hammer”. The cycles will just continue, deepen and quicken, eventually stifling legitimate innovation and technology.
Saddest of all, once we determine that the legislative process was ineffective against the crime they sought to curtail, we still will have a loss of speech during that time, even if the laws were to ever be repealed. That’s right, censorship has a lasting effect, and we might lose powerful ideas, ideals and potentially world changing innovations during the time when people feel they are being censored. We lose all of that, even without a single long term gain against crime.
Given the impacts I foresee from these laws, I can not support them. I do believe in free speech. I do believe in free commerce on the Internet as a global enabler. But all of those reasons aside, I SIMPLY DO NOT BELIEVE that these laws will in any way affect the long term criminal viability or capability of pirates, thieves and data traders. Law is simply not capable of keeping pace with their level of innovation, adaptation and incentives. I don’t know what the answer is, I just know that this approach is not likely to be it.
So, that said, feel free to comment below on your thoughts on the impacts of these laws. If you are against the enactment of these laws, please contact your representatives in Congress and make your voice known. As always, thanks for reading and stay safe out there!
These are my opinions, as an individual – Brent Huston, and as an expert on information security and cyber-crime. They do not represent the views of any party, group or organization other than myself.