Join the Business of Security to hear from Brent Huston, recent winner of (ISC)2 Information Security Leadership Award, who will lay out the need for and principles of performing detection in depth. Brent, CEO and Security Evangelist of MicroSolved, will share his research and hands-on experience that validates the leading approach for detecting threats against your most precious assets.
When: Wednesday, December 7th, Noon EDT
Where: GoToWebinar
Cost: Complimentary Register to attend live or to receive the event archive information for on-demand viewing at: http://www.businessofsecurity.com/
You’ll learn:
- Huston’s postulate and why location matters
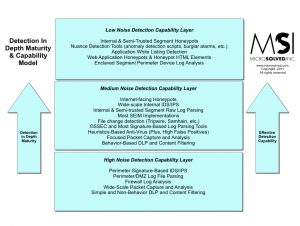
- The detection in depth maturity model
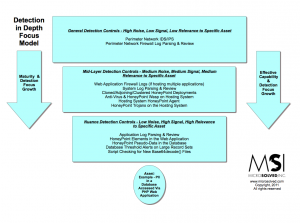
- The detection in depth focus model
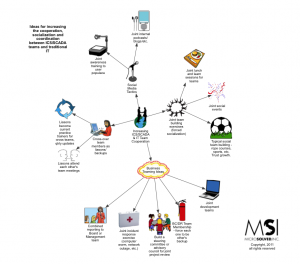
- Tools and approaches for doing detection in depth
Brent’s contribution to the community was recognized by (ISC)2 for employing the HoneyPoint Internet Threat Monitoring Environment (HITME) to alert critical infrastructure organizations whose machines are compromised. MSI provides pro-bono services to help them to mitigate the compromise and manage the threat.
Earn (1) CPE Group A credit for the CISSP and SSCP: This event meets the criteria for a Continuing Professional Education (CPE) activity for the Information Security and Risk Management domain.