COLUMBUS, Ohio October 9, 2012 – The second annual ICS/SCADA Security Symposium, to be held November 1 2012 in Columbus, is designed to serve as a level set for teams and organizations who are actively managing production ICS/SCADA environments. Once again, this full day session will include best practices advice, incident response, detection techniques and a current threat briefing focused on ICS/SCADA providers. Presenters will cover a variety of topics about what is working, what is not working so well in terms of information security, network protection and trust management. To learn more about the event and to see if you qualify to attend, please contact us via email (info<at sign>microsolved(<dot>)com) or via phone by calling 614.351.1237 ext 215. Chris Lay (@getinfosechere) is handling the invitee list for the event and will be happy to discuss the event with you in more detail. Attendance is free of charge, meals will be provided and a limited number of seats are still available if you qualify.
Tag Archives: ICS
MSI Announces The Second Annual ICS/SCADA Security Symposium
COLUMBUS, Ohio October 9, 2012 – The second annual ICS/SCADA Security Symposium, to be held November 1 2012 in Columbus, is designed to serve as a level set for teams and organizations who are actively managing production ICS/SCADA environments. Once again, this full day session will include best practices advice, incident response, detection techniques and a current threat briefing focused on ICS/SCADA providers. Presenters will cover a variety of topics about what is working, what is not working so well in terms of information security, network protection and trust management. To learn more about the event and to see if you qualify to attend, please contact us via email (info<at sign>microsolved(<dot>)com) or via phone by calling 614.351.1237 ext 215. Chris Lay (@getinfosechere) is handling the invitee list for the event and will be happy to discuss the event with you in more detail. Attendance is free of charge, meals will be provided and a limited number of seats are still available if you qualify.
Quick & Dirty Plan for Critical Infrastructure Security Improvement

I was recently engaged with some critical infrastructure experts on Twitter. We were discussing a quick and dirty set of basic tasks that could be used an approach methodology for helping better secure the power grid and other utilities.
There was a significant discussion and many views were exchanged. A lot of good points were made over the course of the next day or so.
Later, I was asked by a couple of folks in the power industry to share my top 10 list in a more concise and easy to use manner. So, per their request, here it is:
@LBHuston’s Top 10 Project List to Help Increase Critical Infrastructure “Cyber” Security
1. Identify the assets that critical infrastructure organizations have in play and map them for architecture, data flow and attack surfaces
2. Undertake an initiative to eliminate “low hanging fruit” vulnerabilities in these assets (fix out of date software/firmware, default configurations, default credentials, turn on crypto if available, etc.)
3. Identify attack surfaces that require more than basic hardening to minimize or mitigate vulnerabilities
4. Undertake a deeper hardening initiative against these surfaces where feasible
5. Catalog the surfaces that can’t be hardened effectively and perform fail state analysis and threat modeling for those surfaces
6. Implement detective controls to identify fail state conditions and threat actor campaigns against those surfaces
7. Train an incident investigation and response team to act when anomalous behaviors are detected
8. Socialize the changes in your organization and into the industry (including regulators)
9. Implement an ongoing lessons learned feedback loop that includes peer and regulator knowledge sharing
10. Improve entire process organically through iteration
The outcome would be a significant organic improvement of the safety, security and trust of our critical infrastructures. I know some of the steps are hard. I know some of them are expensive. I know we need to work on them, and we better do it SOON. You know all of that too. The question is – when will WE (as in society) demand that it be done? That’s the 7 billion people question, isn’t it?
Got additional items? Wanna discuss some of the projects? Drop me a line in the comments, give me a call at (614) 351-1237 or tweet with me (@lbhuston). Thanks for reading and until next time, stay safe out there!
PS – Special thanks to @chrisjager for supporting me in the discussion and for helping me get to a coherent top 10 list. Follow him on Twitter, because he rocks!
Ask The Experts: Important SCADA Security Tips
This time the question comes from an online forum where we were approached about the MSI Expert’s Opinions on an interesting topic. Without further ado, here it is:
Question: In your opinion, what is the single most important question that security teams should be discussing with SCADA asset owners?
Adam Hostetler (@adamhos) replies:
Do your SCADA managers and IT have a culture of security? It’s still found that many SCADA industries still have a weak culture. This needs to be changed through ongoing education and training (like the DHS training). This will help engineers and IT develop and deploy stronger network architectures and technologies to combat increasing SCADA risks in the future.
John Davis also weighed in:
I would say the most important question to discuss with SCADA asset owners is this: do you have short term, mid term and long term plans in place for integrating cyber-security and high technology equipment into your industrial control systems? Industrial concerns and utilities have been computerizing and networking their SCADA systems for years now. This has allowed them to save money, time and manpower and has increased their situational awareness and control flexibility. However, industrial control systems are usually not very robust and also very ‘dumb’. They often don’t have the bandwidth or processing power built into them for mechanisms like anti-virus software, IPS and event logging to work, and these systems are usually made to last for decades. This makes most industrial control systems extremely vulnerable to cyber-attack. And with these systems, availability is key. They need to work correctly and without interruption or the consequences vary from loss of revenue to personal injury or death. So, it behooves those in charge of these systems to ensure that they are adequately protected from cyber-attack now and in the future. They are going to have to start by employing alternate security measures, such as monitoring, to secure systems in the short term. Concerns should then work closely with their SCADA equipment manufacturers, IT specialists, sister concerns and information security professionals to develop mid term and long term plans for smoothly and securely transitioning their industrial control systems into the cyber-world. Failure to do this planning will mean a chaotic future for manufacturers and utilities and higher costs and inconveniences for us all.
What do you think? Let us know on Twitter (@microsolved) or drop us a line in the comments below.
Remember Public Cellular Networks in Smart Meter Adoption
 One of the biggest discussion points at the recent MEA Summit was the reliance of Smart Meter technology on the public cellular networks for communication.
One of the biggest discussion points at the recent MEA Summit was the reliance of Smart Meter technology on the public cellular networks for communication.
There seemed to be a great deal of confusion about negotiating private cellular communications versus dependence on fully public networks. Many folks also described putting in their own femtocell and microcell deployments to greatly reduce the dependence on communication assets that they did not own. However, as you might expect, the purchase, install, management, and maintenance of private cellular infrastructure is expensive, requires skilled personnel, and often bumps into regulatory issues with frequency control and saturation.
Getting Your ICS/SCADA Components Security Tested
 Recently, at the MEA Summit, I had the opportunity to engage in a great discussion with a number of SCADA owners about security testing of their devices. Given all of the big changes underway concerning SCADA equipment, connectivity and the greater focus on these systems by attackers; the crowd had a number of questions about how they could get their new components tested in a lab environment prior to production deployment.
Recently, at the MEA Summit, I had the opportunity to engage in a great discussion with a number of SCADA owners about security testing of their devices. Given all of the big changes underway concerning SCADA equipment, connectivity and the greater focus on these systems by attackers; the crowd had a number of questions about how they could get their new components tested in a lab environment prior to production deployment.
Snort and SCADA Protocol Checks
Recently, ISC Diary posted this story about Snort 2.9.2 now supporting SCADA protocol checks. Why is this good news for SCADA?
Because it is a lower cost source of visibility for SCADA operators. Snort is free and a very competitive solution. There are more expensive commercial products out there, but they are more difficult to manage and have less of a public knowledge base and tools/options than Snort. Many security folks are already familiar with Snort, which should lower both the purchase and operational cost of this level of monitoring.
Those who know how to use Snort can now contribute directly to more effective SCADA monitoring. Basically, people with Snort skills are more prevalent, so it becomes less expensive to support the product, customize it to their specific solution and manage it over time. There are also a wide variety of open source add-ons, and tools that can be leveraged around Snort, making it a very reasonable cost, yet powerful approach to visibility. Having people in the industry who know how the systems work and who know how Snort works allows for better development of signatures for various nefarious issues.
It is likely to be a good detection point for SCADA focused malware and manual probes. The way these new signatures are written allows them to look for common attacks that have already been publicly documented. The tool should be capable of identifying them and can do so with ease. In terms of trending malware, (not currently) these attack patterns have been known for some time.
The specifics of the probes are quite technical and we would refer readers to the actual Snort signatures for analysis if they desire.
By learning the signatures of various threats to the industry, people in the field can translate that into Snort scripts which can detect those signatures on the network and make the proper parties aware in a timely manner. Snort has the flexibility (in the hands of someone who knows how to use it) to be molded to fit the needs of nearly any network.
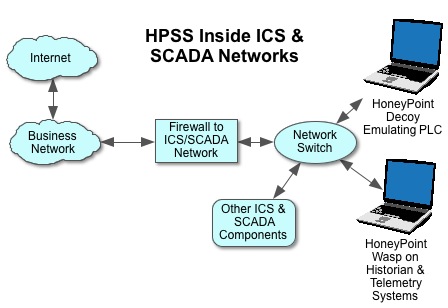
It makes an excellent companion tool to a deployment of HoneyPoint deep inside SCADA and ICS networks. In this case, Snort is usually deployed on the internal network segment of the ICS/SCADA firewall, plugged into the network switch. HPSS is as shown.
If you’re looking for a low-cost solution and plenty of functionality for your SCADA, this recent development is a welcome one!
MSI Strategy & Tactics Ep. 17: Thoughts On The SCADA Breach In Springfield, Illinois
What happened with the water facility SCADA breach in Springfield Illinois? ICS-SCADA security has been on our radar for a few months, now. The recent attack on a water plant in Illinois has highlighted existing vulnerabilities that open the door to malware. In this special edition of MSI Strategy & Tactics, Chris Lay, Account Executive, interviews MSI CEO, Brent Huston on the breach. Take a listen! Discussion questions include:
- Breaking down the nuts and bolts of the attack
- The similarities and differences of the attack vs. the Stuxnet worm
- What ICS-SCADA organizations can learn from this attack
Click the embedded player to listen. Or click this link to access downloads. Stay safe!
Presentation Slides Available from The Ohio SCADA Security Symposium
Although we had a panel discussion, (and some presentations that were confidential) we do have a few we can share. If you’d like to view the slides for them, please visit our presentation page. We’re looking forward to doing this again next year! Thanks to all who came and to our speakers, who were very generous with their time and expertise!
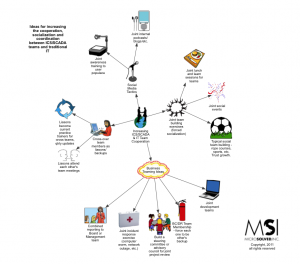
How To Increase Cooperation Between SCADA/ICS and the IT Department
Here is a mind map of a set of ideas for increasing the cooperation, coordination and socialization between the ICS/SCADA operations team and their traditional IT counterparts. Last week, at the Ohio SCADA Security Symposium this was identified as a common concern for organizations. As such, we wanted to provide a few ideas to consider in this area. Let us know in the comments or on twitter if you have any additional ideas and we’ll get them added to a future version of the mind map. Click here to download the PDF.