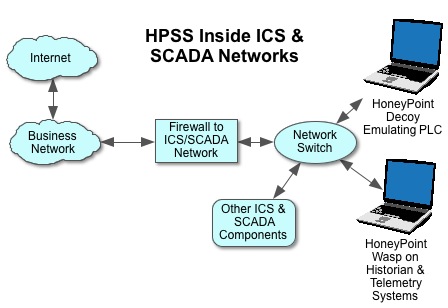
I was recently engaged with some critical infrastructure experts on Twitter. We were discussing a quick and dirty set of basic tasks that could be used an approach methodology for helping better secure the power grid and other utilities.
There was a significant discussion and many views were exchanged. A lot of good points were made over the course of the next day or so.
Later, I was asked by a couple of folks in the power industry to share my top 10 list in a more concise and easy to use manner. So, per their request, here it is:
@LBHuston’s Top 10 Project List to Help Increase Critical Infrastructure “Cyber” Security
1. Identify the assets that critical infrastructure organizations have in play and map them for architecture, data flow and attack surfaces
2. Undertake an initiative to eliminate “low hanging fruit” vulnerabilities in these assets (fix out of date software/firmware, default configurations, default credentials, turn on crypto if available, etc.)
3. Identify attack surfaces that require more than basic hardening to minimize or mitigate vulnerabilities
4. Undertake a deeper hardening initiative against these surfaces where feasible
5. Catalog the surfaces that can’t be hardened effectively and perform fail state analysis and threat modeling for those surfaces
6. Implement detective controls to identify fail state conditions and threat actor campaigns against those surfaces
7. Train an incident investigation and response team to act when anomalous behaviors are detected
8. Socialize the changes in your organization and into the industry (including regulators)
9. Implement an ongoing lessons learned feedback loop that includes peer and regulator knowledge sharing
10. Improve entire process organically through iteration
The outcome would be a significant organic improvement of the safety, security and trust of our critical infrastructures. I know some of the steps are hard. I know some of them are expensive. I know we need to work on them, and we better do it SOON. You know all of that too. The question is – when will WE (as in society) demand that it be done? That’s the 7 billion people question, isn’t it?
Got additional items? Wanna discuss some of the projects? Drop me a line in the comments, give me a call at (614) 351-1237 or tweet with me (@lbhuston). Thanks for reading and until next time, stay safe out there!
PS – Special thanks to @chrisjager for supporting me in the discussion and for helping me get to a coherent top 10 list. Follow him on Twitter, because he rocks!