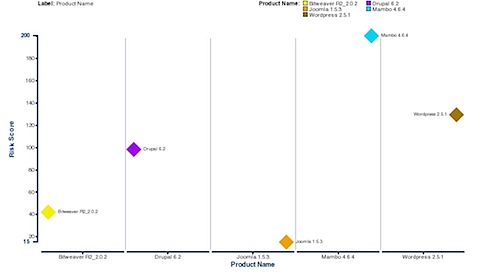
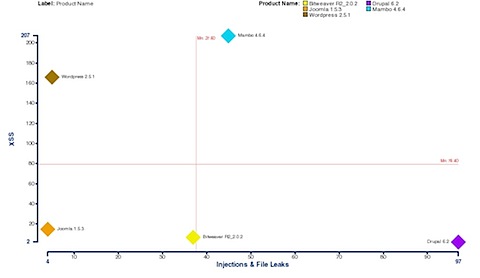
For those organizations who have decided not to patch their DNS servers because they feel protected by implemented controls that only allow recursion from internal systems, we just wanted to point out that there a number of ways that an attacker can cause a recursive query to be performed by an “internal” host.
Here is just a short list of things that an attacker could do to cause internal DNS recursion to occur:
Send an email with an embedded graphic from the site that they want to poison your cache for, which will cause your DNS to do a lookup for that domain if it is not already known by your DNS
Send an email to a mail server that does reverse lookups on the sender domain (would moving your reverse lookup rule down in the rule stack of email filters help minimize this possibility???)
Embed web content on pages that your users visit that would trigger a lookup
Trick users through social engineering into visiting a web site or the like
Use a bot-net (or other malware) controlled system in your environment to do the lookup themselves (they could also use this mechanism to perform “internal” cache poisoning attacks)
The key point here is that many organizations believe that the fact that they don’t allow recursion from external hosts makes them invulnerable to the exploits now circulating in the wild for the DNS issue at hand. While they may be resilient to the “click and drool” hacks, they are far more vulnerable than they believe to a knowledgeable, focused, resourced attacker who might be focused on their environment.
The bottom line solution, in case you are not aware, is to PATCH YOUR DNS SYSTEMS NOW IF THEY ARE NOT PATCHED ALREADY.
Please, do not wait, active and wide scale exploitation is very likely in the very near future, if it is not underway right now!