As we wander the information superhighway it’s no secret there is an abundance of thieves, pirates, and stalkers out there just looking for low hanging fruit to make a quick buck and move on to the next mark. We’ve all heard horror stories of hacker-ish ways good people have fallen prey to the black hats out there, this is encouragement for those who’d like to take as much power back into their own hands as possible; to make thyself a harder target.
Microsoft’s Windows operating system is the market leader in terms of home computer users and there is an entire subculture of people out there who pretty much work to break it by any means for fun and profit! Taking the following countermeasures makes you a little less susceptible to the threats on the Internet.
Windows Automatic Updates
This is a necessary evil of using the Windows operating system. Microsoft launches updates weekly as well as periodic urgent updates that are designed to keep your computer patched against the latest threats. While some prefer to have control over when these updates are applied, it is strongly encouraged to take advantage of the automatic feature- a sort of “set it and forget it” tool that allows one to not continually worry whether they’re up to date or not. Enable or modify your update settings as follows:
Click on Start, open the Control Panel and select Security Center. At the bottom, open Automatic Updates.
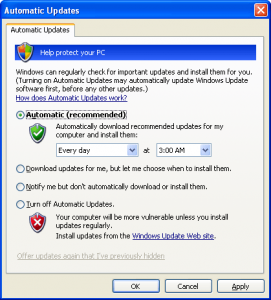
By selecting the automatic option, windows will phone home at the time specified by you. Some prefer to set this for a time when the machine is not in use to prevent the updates from interfering with normal use, such as overnight. Once the desired settings are chosen, click “Apply”, then “OK” and close up shop.
Anti Virus Solutions
Anti Virus and Firewall programs are essential to the protection of any windows computer that is connected to a network. These programs work together to monitor the flow of data through your machine and to give warnings or indications of what might not be “quite right”. While there are premium options available on the market, there is also a set of free tools that do a fine job of protecting the average user.
AVG Anti Virus offers a free solution that offers extensive virus protection with live updates and a nice user interface that allows at-a-glance confirmation that the program is functioning. While there are more features in the subscription version of this product, there is a very comprehensive program in the Free Edition:
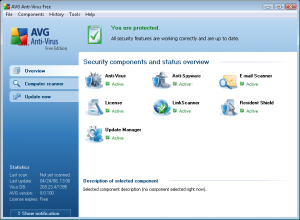
The update menu also has an automatic feature that allows for the “set it and forget it” freedom. Updating immediately will allow AVG to “phone home” and get the latest virus definitions before the first scan of your system. Once these updates are complete (a restart may be required), you’re ready to spend time in the Computer scanner menu setting up preferences and then scanning your system to ensure it’s clean.
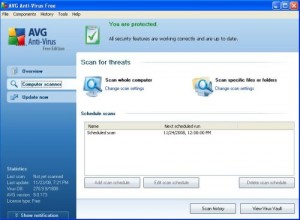
It’s important to first set a scan schedule. Once you’ve got that done, scan the whole computer. This will take some time. Grab a cup of coffee (or my preference, a Monster Drink) and find something to kill some time with. If your Windows partition has any chance of infection (ie, this is NOT a fresh install) then you’ll want to check in periodically to ensure you’re not prompted to address any juicy discoveries. After the initial scan of your machine, you’ll have FREE, real time protection against a good portion of the software threats facing home users today.
Comodo Firewall
Yes, it’s true Comodo offers an “all in one” solution which is a firewall AND an anti virus in one package, but I’ve always been of the mind that my proctologist shouldn’t be doing my mechanic’s work and vice versa. AVG has been my go-to anti virus for some time and it out performs the other freebies while still offering a very easy to use program, and Comodo makes for a great firewall- so I recommend exactly that in Comodo’s Personal Firewall Free Edition. This means it will be important NOT to install the anti virus that comes with the Comodo package:
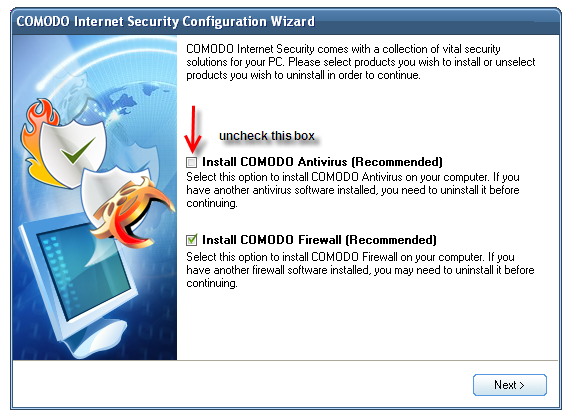
This is VERY important because having more than one anti virus program running at once can cause them to conflict each other and might not protect you to their fullest potential.
Once installed, spend some time learning the interface. Again you’ll want to allow it to update (which is an option under the MISCELLENEOUS menu). When the update is complete, the firewall will want to scan your system. This again sets a baseline by which Comodo can assess future changes to alert you and get permission before taking place.
After the initial scan, you’ll want to spend some time doing typical tasks to let the firewall learn from you. Comodo pops up alerts from the system tray with an outline of a detected action. When you’re teaching it something new, you’ll want to allow the action and usually to “Remember my answer”. It’s a good idea to read these alerts and thoroughly understand this interface to ensure your firewall is functioning properly. This learning period tends to be tedious, but is necessary for the full benefit of “educating” the firewall. Notice the “Treat this application as” option. This puts the firewall into an “installation mode” which will let software be updated or installed without asking permission for every single change.
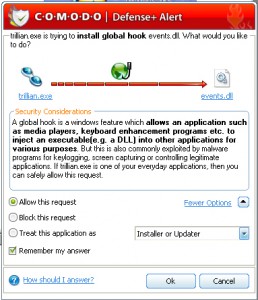
Once Comodo learns your typical activities, you’ll rarely hear from it. The updater will ask permission to phone home and it will alert you of any odd looking traffic, but in reading the alert you should get a good understanding of whether you want to allow it or not. I actually use the Firefox addon “Malware Search”; which adds right click menus that link you to Process Library, &System Lookup, and Google where I’ll search down anything I don’t recognize. If it’s unidentifiable, it doesn’t get through.
Secunia Personal Software Inspector
Secunia PSI is an invaluable tool to the home user. In a nutshell, this program will monitor your system for any available updates and let you know. It’s like a central command and control center for all your software. PSI will advise you of new updates, and re-evaluate to ensure you’re fully covered.
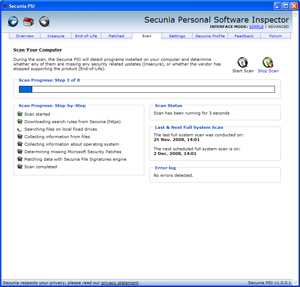
After scanning the computer, PSI will ensure all programs are up to date and will set the process in motion to address any that might not be.
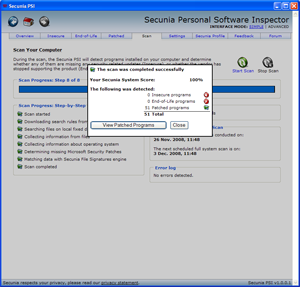
These free tools will set a solid security foundation on any home computer. These things are necessary today in a cyber world where identity theft, spam, and botnets are rampant. It’s us against them and we shouldn’t allow ourselves to be easier targets than absolutely necessary. The MSI team will continue to search out ways of protecting and educating the good guys while thwarting the bad guys.









