Today, I just wanted to remind folks about the capabilities and use cases for HoneyPoint Security Server™. Got questions? Just ping us at info@microsolved.com.
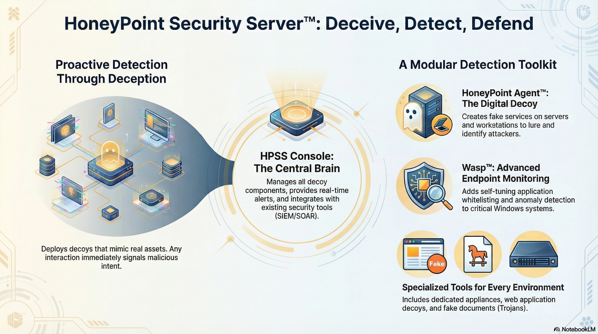

Today, I just wanted to remind folks about the capabilities and use cases for HoneyPoint Security Server™. Got questions? Just ping us at info@microsolved.com.

As APIs now power over half of global internet traffic, they have become prime real estate for cyberattacks. While their agility and integration potential fuel innovation, they also multiply exposure points for malicious actors. It’s no surprise that API abuse ranks high in the OWASP threat landscape. Yet, in many environments, API security remains immature, fragmented, or overly reactive. Drawing from the latest research and implementation playbooks, this post explores a comprehensive and modernized approach to API threat detection and response, rooted in pragmatic security engineering and continuous evolution.

Even among security-mature organizations, API environments often suffer from critical blind spots:
For many defenders, SIEM and XDR platforms are underutilized in the API realm. Yet these platforms offer enormous untapped potential:
Start simple, but start smart:
1. Inventory Everything – Use API gateways, WAF logs, and network taps to discover both documented and shadow APIs. Automate this discovery to keep pace with change.
2. Log the Essentials – Capture detailed logs including timestamps, methods, endpoints, source IPs, tokens, user agents, and status codes. Ensure these are parsed and structured for analytics.
3. Integrate with SIEM/XDR – Normalize API logs into your central platforms. Begin with the API gateway, then extend to application and infrastructure levels.
Then evolve:
Deploy rule-based detections for common attack patterns like:
Enrich logs with context—geo-IP mapping, threat intel indicators, user identity data—to reduce false positives and prioritize incidents.
Add anomaly detection tools that learn normal patterns and alert on deviations, such as late-night admin access or unusual API method usage.
API defense demands speed. Automation isn’t a luxury—it’s survival:
And in the near future, we’ll see predictive detection, where machine learning models identify suspicious behavior even before it crosses thresholds, enabling preemptive mitigation actions.
When an incident hits, a mature API response process looks like this:
You can’t improve what you don’t measure. Monitor these key metrics:
The state of API security is rapidly shifting. Attackers aren’t waiting. Neither can we. By investing in foundational visibility, behavioral intelligence, and response automation, organizations can reclaim the upper hand.
It’s not just about plugging holes—it’s about anticipating them. With the right strategy, tools, and mindset, defenders can stay ahead of the curve and turn their API infrastructure from a liability into a defensive asset.
Let this be your call to action.
Call us (+1.614.351.1237) or drop us a line (info@microsolved.com) for a no-hassle discussion of these best practices, implementation or optimization help, or an assessment of your current capabilities. We look forward to putting our decades of experience to work for you!
* AI tools were used as a research assistant for this content, but human moderation and writing are also included. The included images are AI-generated.
Brent Huston, CEO and Security Evangelist for MicroSolved, Inc., explains how organizations need to move from a focus on prevention to detection.
Joined by MSI’s Account Executive Chris Lay and Marketing Communication Specialist Mary Rose Maguire, Brent maps out how an organization can get detective controls closer to the data and shows that IT departments can have a “payoff” if they pursue nuanced detection.
On May 18th, I will be presenting on detection in depth at the CMH ISSA Summit. I look forward to a good discussion of the ideals, organizational needs, and maturity models. Given all of the focus on re-allocating resources from “prevention only” strategies to an equal spread across the core values of prevention, detection and response, this is likely to be a useful discussion to many organizations.
Join the Business of Security to hear from Brent Huston, recent winner of (ISC)2 Information Security Leadership Award, who will lay out the need for and principles of performing detection in depth. Brent, CEO and Security Evangelist of MicroSolved, will share his research and hands-on experience that validates the leading approach for detecting threats against your most precious assets.
When: Wednesday, December 7th, Noon EDT
Where: GoToWebinar
Cost: Complimentary Register to attend live or to receive the event archive information for on-demand viewing at: http://www.businessofsecurity.com/
You’ll learn:
Brent’s contribution to the community was recognized by (ISC)2 for employing the HoneyPoint Internet Threat Monitoring Environment (HITME) to alert critical infrastructure organizations whose machines are compromised. MSI provides pro-bono services to help them to mitigate the compromise and manage the threat.
Earn (1) CPE Group A credit for the CISSP and SSCP: This event meets the criteria for a Continuing Professional Education (CPE) activity for the Information Security and Risk Management domain.