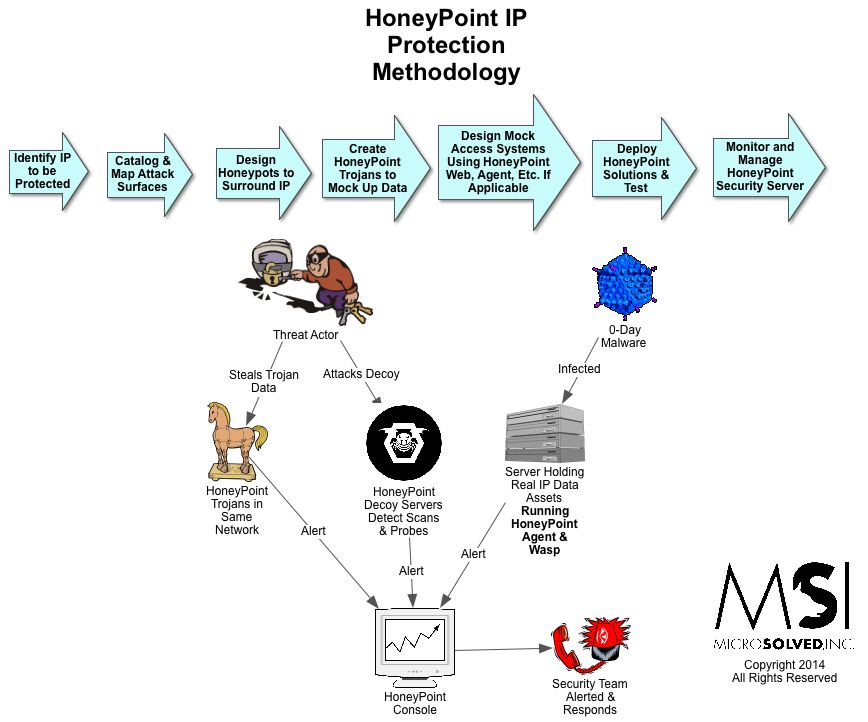
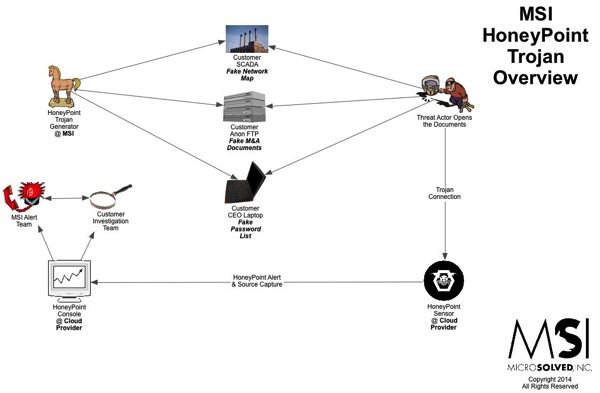
We are thrilled to announce the immediate availability for a new position at MSI. Yes, if you have what it takes, you can join our team! We are seeking a very talented, motivated individual who can come aboard and help us with tasks related to HoneyPoint and TigerTrax. The new position is detailed below. The successful candidate will be local to the Central Ohio area (must be able to be work from the Columbus HQ) and will be motivated, engaging and capable of self-directed work. Primarily, the position will be focused on helping clients with scoping and installation of HoneyPoint and performing TigerTrax engagements.
Future career options for the position would be a choice between pursuing a future position on the technical security team (including pen-testing, etc.) or to grow into the deeper intelligence/research team that currently is embodied by TigerTrax. While the initial position will expose you to both, together, we can help scope where your interests and talents lie. Management and team leadership are also possible in either career path, as well.
This is a full time salary position, with benefits and a wide range of flexible working arrangements once the proper skills and trust are built. It also includes profit sharing, 401K with match and a variety of other benefit packages.
Successful candidates will present a resume, cover letter and a sample of their professional writing. You can apply for the position by emailing these items (PDF format) to info <at> microsolved <dot> com. No calls or placement/recruiters, please.
Further details of the position:
The information technology analyst is a key member of the MicroSolved, Inc. team who specializes in our software and research tool set. This team member must be:
- proficient with research skills
- knowledgeable of social media networks and formats
- knowledgeable of basic networking skills
- proficient with Windows, Mac OS/X and Linux at the command line
- proficient with command line scripting (shell/Python) and be a power-user of the Internet
The successful analyst should be detail oriented, enjoy reading, solving logic and language puzzles and be proficient with technical writing and technical reports. Occasional travel, including internationally, is required.
This team member is responsible for research projects beginning with data generation through report preparation and delivery to the client. This team member is also responsible for the scoping and deployment of MicroSolved, Inc’s threat detection platform – HoneyPoint Security Server (HPSS).
As always, thanks for reading, and I hope to see you on the team very soon!