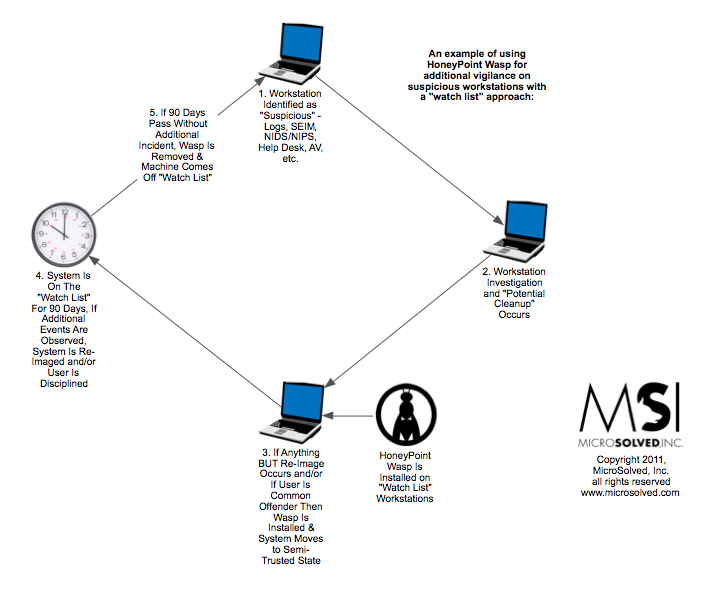
On Twitter, Brent Huston (@lbhuston), CEO and Security Evangelist, posed this question: Does the introduction of speed bumps into a neighborhood reduce overall burglaries and petty crime?
On Twitter, Brent Huston (@lbhuston), CEO and Security Evangelist, posed this question: Does the introduction of speed bumps into a neighborhood reduce overall burglaries and petty crime?
There was some speculation that it may not impact burglaries but could impact violent crime. An Oakland study showed that bumps decrease the casual traffic pattern by 33%. As it turns out, speed bumps decrease speeding by 85%. Less casual traffic means less scouting for break-ins. So, speed bumps make you more secure. A study done by the Portland Bureau of Transportation shows a full examination of the impact of speed bumps.
Although speed bumps may deter criminal traffic, there’s a good possibility that the criminals just head toward an area that doesn’t have speed bumps. The same can be true with hardening your home security. If you take precautions and make your home more difficult to enter, the burglar may instead target one of your neighbor’s homes.
Although there may be instances where criminal activity increased due to speed bumps, those are not common and serve as the exception rather than the rule. Still, logic dictates that with more controls comes a decrease in crime. (Less speeding, less petty crime.)
And if you do find yourself in a neighborhood with speed bumps, slow down. They can sometimes break the cars of speeders.
This leads us to the next question: What do speed bumps tell us about information security?