Category Archives: Phishing
How to Avoid Getting Phished
Never Store Anything on the Cloud that You Wouldn’t Want Your Mamma to See
It’s great now days, isn’t it?
You carry around devices with you that can do just about anything! You can get on the Internet and check your email, do your banking, find out what is new on Facebook, send a Tweet or a million other things. You can also take a picture, record a conversation, make a movie or store your work papers – and the storage space is virtually unlimited! And all this is just great as long as you understand what kind of risks this freedom poses to your privacy.
Remember that much of this stuff is getting stored on the cloud, and the only thing that separates your stuff from the general public is a user name, password and sometimes a security question. Just recently, a number of celebrities have complained that their photos (some of them explicit) have been stolen by hackers. These photos were stored in iCloud digital vaults, and were really very well defended by Apple security measures. But Apple wasn’t at fault here – it turns out that the celebrities themselves revealed the means to access their private stuff.
It’s called Phishing, and there are a million types of bait being used out there to fool or entice you. By clicking on a link in an innocent-looking email or answering a few simple questions, you can give away the keys to the kingdom. And even if you realize your mistake a couple of hours later, it is probably already too late to do anything about it. That naughty movie you made with your spouse during your romantic visit to Niagara Falls is already available from Peking to Panama!
Apple announced that they will soon start sending people alerts when attempts are made to change passwords, restore iCloud data to new devices or when someone logs in for the first time from new Apple devices. These are valuable controls, but really are only detective in nature and won’t actually prevent many data losses. That is why we recommend giving yourselves some real protection.
First, you should ensure that you educate yourself and your family about the dangers hackers and social engineers pose, and the techniques they use to get at your stuff. Second, it is really a lot better to store important or sensitive data on local devices if possible. But, if you must store your private data in the cloud, be sure it is well encrypted. Best of all, use some sort of good multi-part authentication technique to protect your stuff from being accessed easily by hackers. By that I mean something like a digital certificate or an RSA hard token – something you have or something you are, not just something you know.
If you do these things, then it’s a good bet your “special moments” won’t end up in your Momma’s inbox!
Thanks to John Davis for this post.
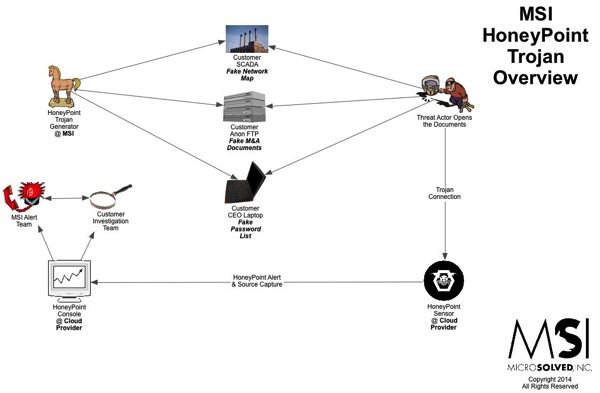
HoneyPoint Trojans Overview
Here’s another quick overview graphic of how HoneyPoint Trojans work. We have been using these techniques since around 2008 and they are very powerful.
We have incorporated them into phishing exercises, piracy studies, incident response, intrusion detection, intelligence gathering, marketing analysis and even privacy research. To hear more about HoneyPoint Trojans, give us a call.
If the graphic below is blurry on your device, you can download a PDF version here.
YAPT: Yet Another Phishing Template
Earlier this week, we gave you the touchdown task for July, which was to go phishing. In that post, we described a common scam email. I wanted to post an example, since some folks reached out on Twitter and asked about it. Here is a sample of the email I was discussing.
<paste>
Hi My name is Mrs. Hilda Abdul , widow to late Dr. Abdul A. Osman, former owner of Petroleum & Gas Company, here in Kuwait. I am 67 years old, suffering from long time Cancer of the breast.
From all indications my condition is really deteriorating and it’s quite obvious that I won’t live more than 3 months according to my doctors. This is because the cancer stage has gotten to a very bad stage.
I don’t want your pity but I need your trust. My late husband died early last year from Heart attack, and during the period of our marriage we couldn’t produce any child. My late husband was very wealthy and after his death, I inherited all his businesses and wealth .The doctor has advised me that I will not live for more than 3 months ,so I have now decided to spread all my wealth, to contribute mainly to the development of charity in Africa, America,
Asia and Europe .Am sorry if you are embarrassed by my mail. I found your e-mail address in the web directory, and I have decided to contact you, but if for any reason you find this mail offensive, you can ignore it and please accept my apology. Before my late husband died he was major oil tycoon in Kuwait and (Eighteen Million Dollars)was deposited in a Bank in cote d ivoire some years ago, that’s all I have left now,
I need you to collect this funds and distribute it yourself to charity .so that when I die my soul can rest in peace. The funds will be entirely in hands and management. I hope God gives you the wisdom to touch very many lives that is my main concern. 20% of this money will be for your time and effort includin any expensese,while 80% goes to charity. You can get back to me via my private e-mail: (hilda.abdul@yahoo.com) God bless you.
1. Full name :
2. Current Address :
3. Telephone N° :
4. Occupation :
5. Age :
6. Country :
MRS. Hilda Abdul
<end paste>
As you can see, this is a common format of a phishing scam. In this case, you might want to edit the targeting mechanism a bit, so that they have to click through to a web page to answer or maybe even include a URL as supposed proof of the claim. That way you would have two ways to catch them, one by email reply and two by click through to the simple phish application.
As always your milage and paranoia may vary, but it is still pretty easy to get people to click or reply ~ even with age old spam phish attacks like this. What kind of return percentages did you get? What lessons did you learn? Drop us a line on Twitter (@lbhuston) and let us know.
Go Phish :: How To Self Test with MSI SimplePhish
Depending on who you listen to, phishing (especially spear phishing), is either on the increase or the decrease. While the pundits continue to spin marketing hype, MSI will tell you that phishing and spearphishing are involved in 99% of all of the incidents that we work. Make no mistake, it is the attack of choice for getting malware into networks and environments.
That said, about a year ago or more, MSI introduced a free tool called MSI SimplePhish, which acts as a simplified “catch” for phishing campaigns. The application, which is available for Windows and can run on workstations or even old machines, makes it quite easy to stand up a site to do your own free phishing tests to help users stay aware of this threat.
To conduct such a campaign, follow these steps:
PreCursor: Obtain permission from your security management to perform these activities and to do phishing testing. Make sure your management team supports this testing BEFORE you engage in it.
1. Obtain the MSI SimplePhish application by clicking here.
2. Unzip the file on a the Windows system and review the README.TXT file for additional information.
3. Execute application and note the IP address of the machine you are using. The application will open a listening web server on port 8080/TCP. Remember to allow that port through any host-based firewalls or the like.
4. The application should now be ready to catch phishing attempts and log activity when the following URL structure is clicked on: http://<ip address of the windows system>:8080/ and when that URL is accessed, a generic login screen should be displayed.
5. Create an email message (or SMS, voice mail, etc.) that you intend to deliver to your victims. This message should attempt to get them to visit the site and enter their login information. An example:
Dear Bob,
This message is to inform you that an update to your W-2 tax form is required by human resources. Given the approaching tax deadline, entering this information will help us to determine if an error was made on your 2012 W-2. To access the application and complete the update process, please visit the online application by clicking here. (You would then link the clicking here text to your target URL obtained in step 4.)
6. Deliver the messages to your intended targets.
7. Watch and review the log file MSISimplePhishLog.txt (located in the same directory as the binary). Users who actually input a login and password will get written to the log as “caught”, including their IP address, the login name and **the first 3 characters** of the password they used. Users who visit the page, but do not login, will be recorded as a “bite”, including their IP address.
** Note that only the first 3 characters of the password are logged. This is enough to prove useful in discussions with users and to prove their use, but not enough to be useful in further attacks. The purpose of this tool is to test, assess and educate users, not to commit fraud or gather real phishing data. For this reason, and for the risks it would present to the organization, full password capture is not available in the tool and is not logged. **
8. Let the exercise run for several days, in order to catch stragglers. Once complete, analyze the logs and report the information to the security stakeholders in your organization. Don’t forget to approach the users who use successfully phished and give them some tips and information about how they should have detected this type of attack and what they should do to better manage such threats in the future.
That’s it – lather, rinse and repeat as you like!
If you would like to do more advanced phishing testing and social engineering exercises, please get in touch with an MSI account executive who can help put together a proposal and a work plan for performing deep penetration testing and/or ongoing persistent penetration testing using this and other common attack methods. As always, thanks for reading and until next time, stay safe out there!
