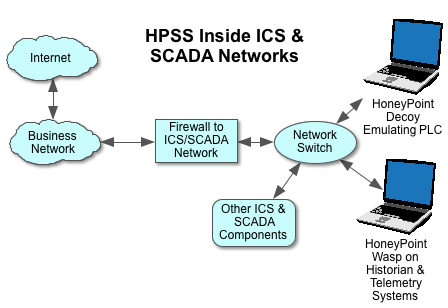
One of the biggest questions we get when we talk to Credit Unions is about threats. They often want to know who might be targeting Credit Unions and how they might get attacked. Based on these questions and how often we hear them, we have come up with a way for you to actually get some metrics and intelligence around your own threat postures.
I am proud to introduce a new short-term service for Credit Unions that leverages our patent-pending HoneyPoint technology in a useful, powerful, easy and affordable way. The MSI Threat Posture Analysis is a new service that does just that. The service is comprised of the following phases:
1. Initial consultation – our teams work together to plan for a quick, safe and easy deployment of our HoneyPoint technology; this initial discussion helps us decide if we are going to leverage a HoneyPoint hardware, software or combined deployment and exactly what we want to emulate for metrics gathering; the length of the metrics gathering mission is also determined (usually 90 days).
2. Pricing and contracts – based on our work together, fixed bid pricing is provided for the analysis and monitoring.
3. Delivery of technology – our teams work together to deliver and install the technology; MSI monitors the deployment remotely back at our NOC.
4. Analysis – MSI performs analysis of the data gathered; generating a set of reports that details sources of attacks, general estimated capabilities, attack frequency and other metrics designed to feed real world threat data into the Credit Union’s information security program.
5. Decommission and return of the technology – our teams work together to uninstall the technology and return any hardware to MSI.
6. Follow on Q&A – for 3 months, MSI will continue to be available to answer questions or discuss the data and metrics identified in the analysis.
It’s that easy. You can quickly, easily, safely and affordably, move from blunt estimations of threats to real world data and intelligence. If you would like that intelligence as an ongoing basis, give us a call and we can discuss our managed services with you as well.
So, if you’re tired of doing risk assessments without real numbers to back up your data or if your team has hit the maturity point where they can use real world metrics and threat source data to create firewall rules, black holes and other dynamic defenses, this approach can give them the data they are hungry for.
If you would like to discuss the analysis or hear more about it, give your account executive a call or reach out to me on Twitter (
@lbhuston). I look forward to talking with you about the successes we are seeing.
As always, thanks for reading and stay safe out there!