Got a file that you want to know more about? Have the MD5 hash for it, and want to know if it is known to be malware? This seems to be a common problem.
Got a file that you want to know more about? Have the MD5 hash for it, and want to know if it is known to be malware? This seems to be a common problem.
Talking to Your Management Rationally About Malware
 Malware with comparisons to Stuxnet are all the rage these days. CNN and other popular media outlets now run stories about new Trojans, viruses and exploits. Much of what is in the media is either hysteria, hype, confusion or outright wrong.
Malware with comparisons to Stuxnet are all the rage these days. CNN and other popular media outlets now run stories about new Trojans, viruses and exploits. Much of what is in the media is either hysteria, hype, confusion or outright wrong.Audio Blog Post: Twitter Favorites
 We’re kicking off the week by talking about some of our favorite feeds on Twitter!
We’re kicking off the week by talking about some of our favorite feeds on Twitter!
Brent Huston, CEO and Security Evangelist for Microsolved, Inc., interviews Chris Lay, Account Executive and Mary Rose Maguire, Marketing Communication Specialist, about their favorite kinds of tweets.
We like Twitter to keep up with other security professionals to discover what’s trending. It’s a great way to exchange quick information and alert others when a security issue arises. Plus, our #HITME stream through our MSI HoneyPoint Feed Twitter account has already helped other organizations by alerting them to suspicious activity caught on various ports.
If you’d like to follow the MSI crew, here we are:
- Brent Huston: @lbhuston
- Chris Lay: @GetInfoSecHere
- Mary Rose Maguire: @MRMaguire
- Constance Matthews: @Cahnee
- Phil Grimes: @grap3_ap3
- Adam Hostetler: @adamhos
Here are a few of our favorites we mentioned:
- @SansInstitute
- @Laughing Squid
- @Wired
- @Lifehacker
- #security
- @CIOMagazine
- @ITWorld
- @ArsTechnica
- @Technorati
Click Here To Listen To The Audio Blog Post!
Hooray! An Open-Source Password Analyzer Tool!
I’m one of the resident “Password Hawks” in our office. Our techs consistently tell people to create stronger passwords because it is still one of the most common ways a hacker is able to infiltrate a network.
However, we live in an age where it’s not just hackers who are trying to steal an organization’s data. There are also a variety of malcontents who simply want to hack into someone’s account in order to embarrass them, confirm something negative about them, or be a nuisance by sending spam.
This is why it is important to create a strong password; one that will not be easily cracked.
Enter password analyzer tools. Sophos’ “Naked Security” blog posted a great article today about the often misleading security policies of popular online social sites. Developer Cameron Morris discovered that if he followed one social site’s policy, he actually created a more easily “crackable” password than the one they deemed weak.
About three years ago, developer Cameron Morris had a personal epiphany about passwords, he recently told ZDNet’s John Fontana: The time it takes to crack a password is the only true measure of its worth.
Read the rest of the article here.
There is a free analyzer you can use and I strongly suggest you test the strength of your passwords with it.
Also, Morris created a tool for administrators that would allow them to configure a password policy based on the time to crack, the possible technology that an attacker might be using (from an everyday computer on up to a $180,000 password attacker), and the password protection technology in use (from Microsoft Windows System security on up to 100,000 rounds of the cryptographic hash function SHA-1/).
OWASP Password Creation Slide-Tool
This is one of the best articles I’ve read on password security, plus it has tools for both the end-user and the administrator. Test them out yourself to see if you have a password that can resist a hacker!
As for me, I think I need to do a little more strengthening…
Have a great Memorial Day weekend (for our U.S. readers) and stay safe out there!
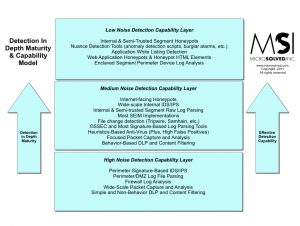
Audio Blog Post: Moving Toward Detection in Depth
Brent Huston, CEO and Security Evangelist for MicroSolved, Inc., explains how organizations need to move from a focus on prevention to detection.
Joined by MSI’s Account Executive Chris Lay and Marketing Communication Specialist Mary Rose Maguire, Brent maps out how an organization can get detective controls closer to the data and shows that IT departments can have a “payoff” if they pursue nuanced detection.
13 Tips to Secure Your Virtual Machine Environment
 Virtual environments are becoming more popular, providing advantages such as enabling multiple OS environments to co-exist and providing disaster recovery solutions.
Virtual environments are becoming more popular, providing advantages such as enabling multiple OS environments to co-exist and providing disaster recovery solutions.
Virtual machines easily tests scenarios, consolidate servers, and can move disk files and some configuration files between physical machines.
Safeguarding your virtual server environment is vital, even though it doesn’t have the same issues as a physical environment. Here are a few tips to keep things running smoothly:
- Install only what you need on the host machine. Keep your OS and applications current for both virtual and host machines.
- Isolate each virtual machine you have by installing a firewall. Only allow approved protocols to be deployed.
- Ensure that antivirus programs are installed on the virtual machines and kept current with updates. Virtual machines, like physical machines are at risk for viruses and worms.
- Utilize strong encryption between the host and virtual machines.
- Avoid internet surfing from the host computer. Spyware and malware could easily infiltrate through the the host computer and spread to the virtual machines.
- Prevent unauthorized access by securing accounts on the host machine.
- Only use what you need. If you’re not utilizing a virtual machine, shut it down.
- If a virtual machine does not need to connect with each other, isolate it. Use a separate network card on a different network range.
- Monitor the event log and security events on both the host machine and on the virtual machine. These logs need to be stored in your log vault for security and for auditing purposes at a later date.
- Ensure that any hardware you use is designed for VM usage.
- Strictly manage remote access to virtual machines and especially to the host machine, this will make exposure less likely.
- Remember, the host machine represents a single point of failure. Technologies like replication and continuity help with reducing this risk.
- Avoid sharing IP addresses. Again this is typical of sharing a resource and will attract problems and vulnerabilities.
Using these tips will help you make the most of your physical and virtual environments so if anything interrupts your business, you are prepared.
Are You Attending the 2012 Central Ohio InfoSec Summit?
We’re excited to be a part of this year’s 5th Annual 2012 Central Ohio InfoSec Summit! Each year it keeps getting better and better, and this year is no different.
MicroSolved’s CEO and founder, Brent Huston will be presenting “Detection in Depth: Changing the PDR Focus.” Phil Grimes will also present “Attacking Mobile Devices” in the Advanced Technical Track.
There are other great speakers lined up. Included are:
- Bill Hagestad, author of 21st Century Chinese Cyber Warfare
- Jay Jacobs, a Principal with Verizon’s RISK Intelligence team, will focus on cyber crime
- Curtis Levinson, who has served two sitting Presidents of the United States, two Chairman of the Joint Chiefs of Staff and the Chief Justice of the United States, who will be presenting on a balanced approach for survivability and sustainability in the cyber realm
There are more great speakers, plus over thirty vendors who help businesses stay secure. We hope to see you at the event! It promises to be a great time re-connecting with old friends, making new connections, and learning new approaches toward a proactive information security strategy.
See you there!
Twitter Hack! 5 Ways to Avoid Being the Victim of a Phishing Attack
 Twitter is downplaying a security breach that exposed tens of thousands of user emails and passwords.
Twitter is downplaying a security breach that exposed tens of thousands of user emails and passwords.
The leaked information, comprising 58,978 username and password combinations, appeared Monday on Pastebin. While Twitter said that it’s investigating the breach, it’s also downplayed the supposed size and severity of the data dump.
“We are currently looking into the situation,” said spokeswoman Rachel Bremer via email. “It’s worth noting that, so far, we’ve discovered that the list of alleged accounts and passwords found on Pastebin consists of more than 20,000 duplicates, many spam accounts that have already been suspended, and many login credentials that do not appear to be linked (that is, the password and username are not actually associated with each other).”
Information Week Security article
Whenever you read about such breaches, it is always a good idea to change your password, especially if you’ve not changed it for some time.
The compromised Twitter accounts could have been the result of phishing attacks. A phishing attack is when an attacker acquires personal information by duping the user into revealing it through manipulating their emotions.
Remember how one of your wiser friends told you it’s never a good idea to make a big decision while you’re overly-emotional? The same stands true for avoiding phishing attacks.
Here are some ways to stay safe:
- Do not give out your financial information ever through an email appeal. I hope we all know now that you haven’t won the Nigerian lottery or that some prince or princess is willing to give you part of their inheritance if only you’ll keep their money in your bank account. Emails of this nature prey upon people who would love to “win” money or worse, may lose money in their account unless they give out their account information. Never give out your personal information. Instead, call your bank to verify that they need the information. You could also have some fun with the hackers like I did.
- Don’t call any phone number or visit a website that is linked in the email. There’s a good chance it will connect you directly to the attacker. Look at the URL associated with the link. Does it contain words, letters, or numbers that seem odd? It’s likely an attempt to masquerade as an organization’s true website address, so don’t click it. You can see the URL by hovering over it or highlighting it with your mouse. Again, if you think it may be a legitimate request for information, verify it by contacting your financial institution directly.
- Never fill out forms in an email that asks for personal information. Most organizations like PayPal notify their customers but do not ask for personal information to be placed into forms. Again, verify, verify, verify.
- Regularly check your online banking accounts. Don’t allow months to go by before checking in. By frequently monitoring your account, you’ll be able to immediately see suspicious activity.
- Patch it! When that annoying “Software Updates Available Now” window pops up, don’t ignore it. (I’m talking mainly to myself, now.) Click to install. Patches fix vulnerabilities and many attackers will jump on the opportunity to hit an un-patched machine. If you’re in doubt about whether your browser system is up-to-date, check by clicking your browser’s info link or your system’s and click “Software Update” or “Check for updates.” (In Firefox, it’s in the “Tools” section.)
Finally, you can report phishing attacks to the following organizations:
- The Federal Trade Commission at spam@uce.gov.
- Forward the email to the “abuse” email address to the company that is being spoofed (i.e. “abuse@XYZcompany.com” or “spam@XYZcompany.com”). Make sure to forward the complete email message with the original email header.
- Notify the Internet Fraud Complaint Center of the FBI by filing a complaint on their website: http://www.ic3.gov/default.aspx There is an excellent selection of tips on the FBI site to help you avoid fraud, so make sure to check it out.
The key to avoid becoming a victim is to stay alert, stay suspicious, and stay on top of changing your passwords.
Stay safe!
Resources for Mobile Application Security
 Mobile application security continues to be a hot topic within the information security community. With more and more employees expecting to use their own devices at their workplaces, IT departments are scrambling to develop the right approach for securing their data.
Mobile application security continues to be a hot topic within the information security community. With more and more employees expecting to use their own devices at their workplaces, IT departments are scrambling to develop the right approach for securing their data.
If you’re working on developing security policies or seeking ways to secure your mobile applications, you may find some of these resources helpful. Stay safe out there!
- Programming Mobile Devices: In Introduction for Practitioners by Tommi Mikkonen
- Embedded Java Security: Security for Mobile Devices by Mourad Debbabi, Mohamed Salah, Chamseddiing Talhi, Sami Zhioua
- Advances in Security and Payment Methods for Mobile Commerce by Wen-Chen Hu, Chung-wei Lee, Weidong Kou
- Construction and Analysis of Safe, Secure, and Interoperable Smart Devices: International Workshop CASSIS 2004, by Gilles Barthe (Editor)
- Anti-Virus Software for Smartphones (CNET)
- Guidelines for Security Mobile Computing Devices (Stanford University)
- Mobile Security Definition and Solutions (CIO Magazine)
- Five Steps to Protect Mobile Devices Anywhere, Anytime (TechRepublic)
- Mobile Device Security Through Virtualization (EDN)
- Mobile Device Protection (SC Magazine)
Quick Wireless Network Reminders
 I recently tested a couple of Android network stumblers on a drive around the city and I found that not a lot has changed for consumer wireless networks since I last stumbled.
I recently tested a couple of Android network stumblers on a drive around the city and I found that not a lot has changed for consumer wireless networks since I last stumbled.
There are still a TON of unprotected networks, default SSIDs and WEP networks out there. It appears that WPA(x) and WPS have been slower to be adopted than I had expected. I don’t know if that is consumer apathy, ignorance or just a continued use of legacy hardware before the ease of push button WPS. Either way, it was quickly clear that we still have a long way to go to deprive criminals of consumer-based wireless network access.