Why Building Cybersecurity Like the Human Immune System Is the Only Strategy That Survives the Unknown
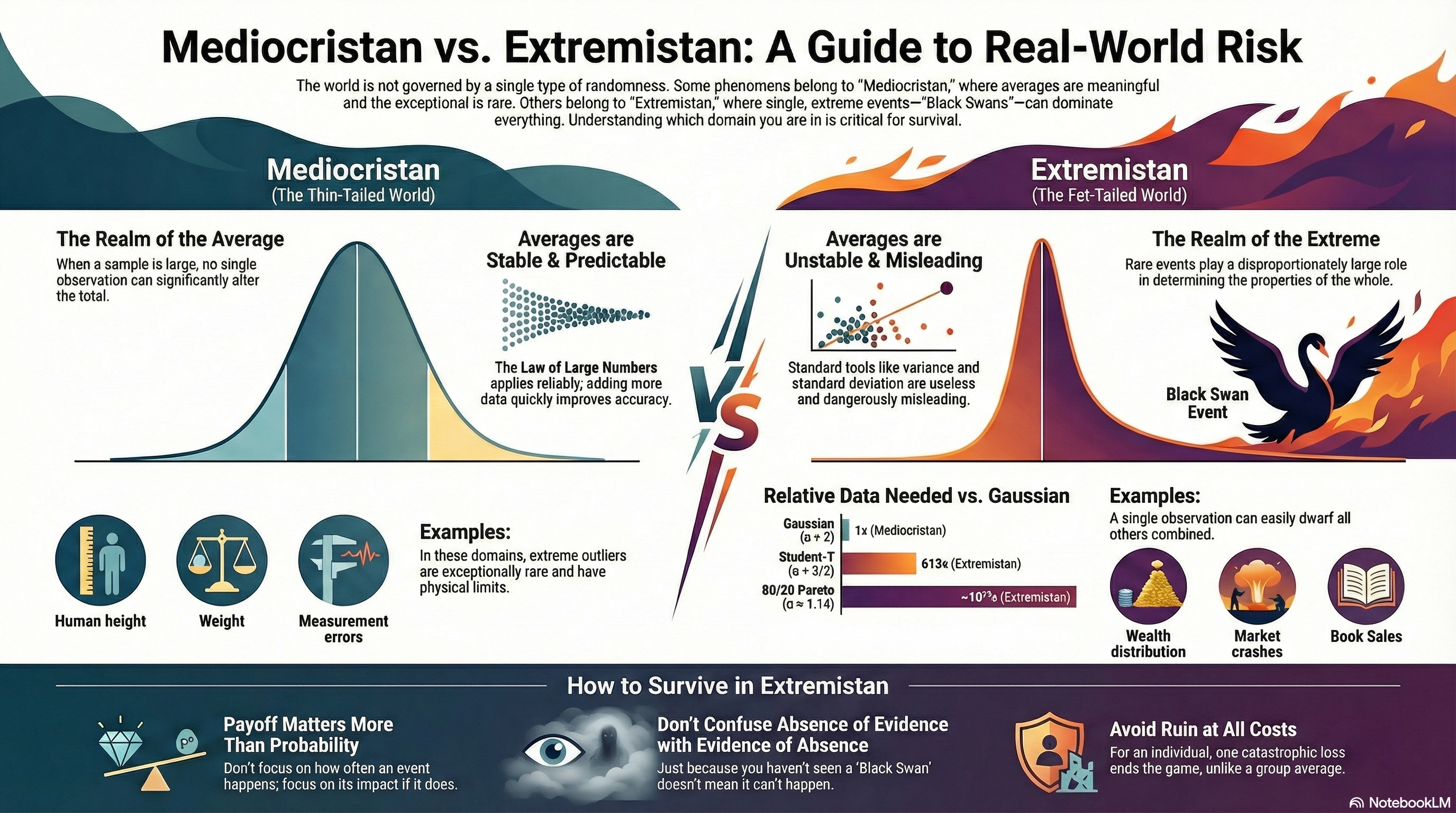
We don’t live in “Mediocristan” anymore.
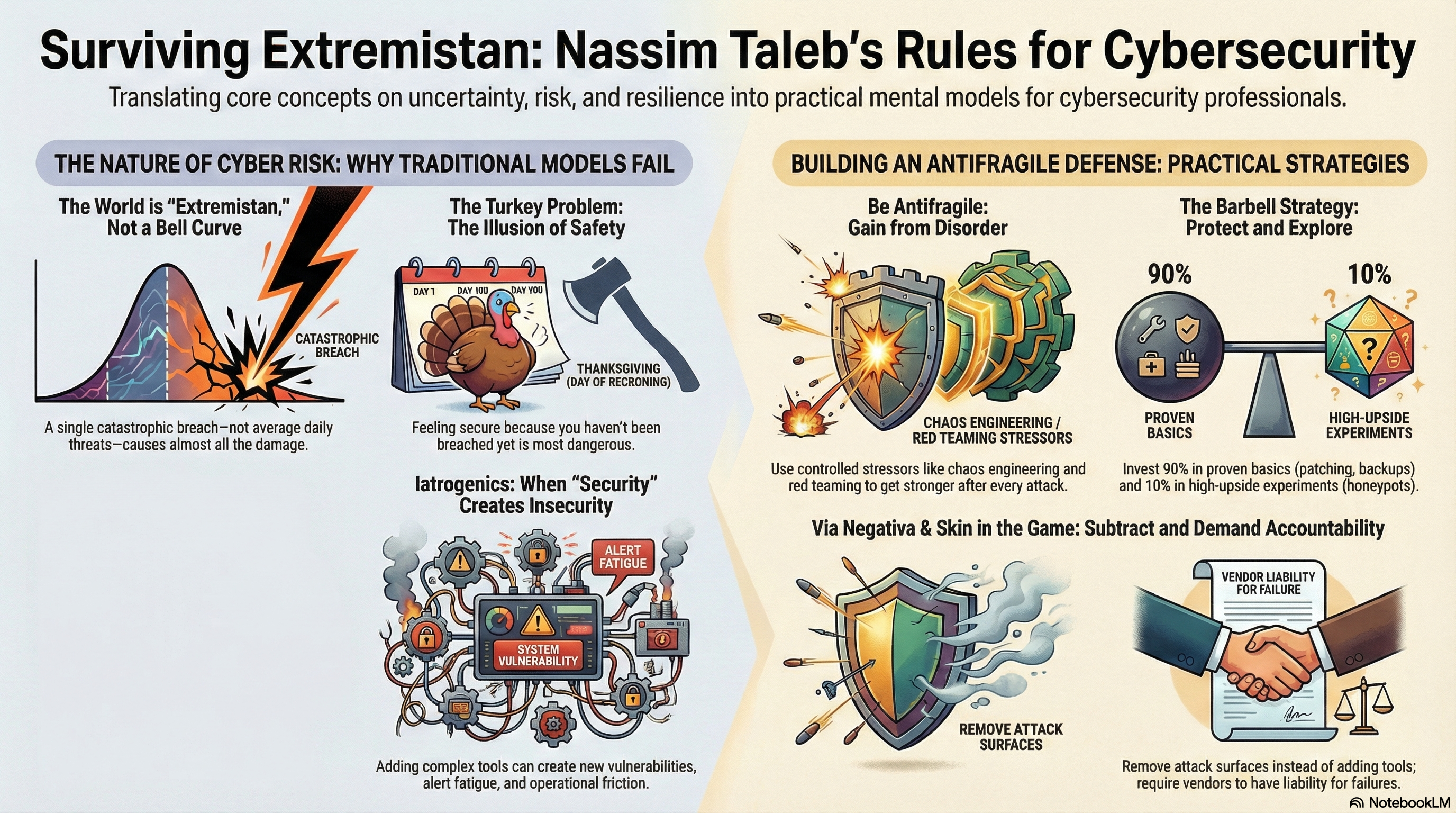
In the controlled world of Gaussian curves and predictable outcomes, most security strategies make sense—if you’re still living in the realm where human height and blood pressure are your biggest threats. But for cybersecurity practitioners, the real world looks more like “Extremistan”—the place where Black Swan events dominate, where a single breach can wipe out decades of effort, and where average behavior is not just irrelevant, it’s dangerously misleading.
That’s the world Nassim Taleb described in The Black Swan, and it’s the reality we live in every day as defenders of digital infrastructure.
And if you’re using traditional models to manage cyber risk in this world, you’re probably optimizing for failure.
From Robust to Antifragile: Why Survival Isn’t Enough
Taleb coined the term antifragile to describe systems that don’t just resist chaos—they improve because of it. It’s the difference between a glass that doesn’t break and a muscle that gets stronger after lifting heavy weight. Most security programs are designed to be robust—resilient under stress. But that’s not enough. Resilience still assumes a limit. Once you pass the red line, you break.
To thrive in Extremistan, we need to design systems that learn from stress, that benefit from volatility, and that get stronger every time they get punched in the face.
1. Security by Subtraction (Via Negativa)
In medicine, there’s a term called iatrogenics—harm caused by the treatment itself. Sound familiar? That’s what happens when a security stack becomes so bloated with overlapping agents, dashboards, and tools that it becomes its own attack surface.
Antifragile security starts with subtraction:
-
Decommission Legacy: Every unmonitored web server from 2009 you forgot about is a potential ruin event.
-
Minimize Privilege: If your domain admin group has more people than your bowling team, you’re in trouble.
-
Simplify, Aggressively: Complexity is fragility disguised as maturity.
Less isn’t just more—it’s safer.
2. Controlled Stressors: Hormesis for Systems
An immune system kept in a bubble weakens. One that’s constantly challenged becomes elite. The same goes for cyber defenses.
-
Red Teams as Immune Response Training: Stop treating red teams as adversaries. They’re your vaccine.
-
Chaos Engineering: Don’t just test recovery—induce failure. Intentionally break things. Break them often. Learn faster than your adversaries.
-
Study the Misses: Every alert that almost mattered is gold dust. Train on it.
This isn’t about drills. It’s about muscle memory.
3. The Barbell Strategy: Secure Boring + Wild Bets
One of Taleb’s more underappreciated ideas is the barbell strategy: extreme conservatism on one end, high-risk/high-reward exploration on the other. Nothing in the middle.
-
90%: Lock down the basics. IG1 controls. Patching. Backups. Privilege minimization. The boring stuff that wins wars.
-
10%: Invest in weird, bleeding-edge experiments. Behavioral traps. Decoy data. Offensive ML. This is your lab.
Never bet on “average” security tools. That’s how you end up with a little risk everywhere—and a big hole somewhere you didn’t expect.
4. Skin in the Game: Incentives That Matter
When the people making decisions don’t bear the cost of failure, systems rot from within.
-
Vendors Must Own Risk: If your EDR vendor can disclaim all liability for failure, they’ve got no skin in your game.
-
On-Call Developers: If they wrote the code, they stay up with it. The best SLAs are fear and pride.
-
Risk-Based Compensation: CISOs must have financial incentives tied to post-incident impact, not checkbox compliance.
Fragility flourishes in environments where blame is diffuse and consequences are someone else’s problem.
5. Tail Risk and the Absorbing Barrier
Most CIS frameworks are built to mitigate average risk. But in Extremistan, ruin is what you plan for. The difference? A thousand phishing attempts don’t matter if one spear phish opens the gates.
-
Design for Blast Radius: Assume breach. Isolate domains. Install circuit breakers in your architecture.
-
Plan for the Unseen: Run tabletop exercises where the scenario doesn’t exist in your IR plan. If that makes your team uncomfortable, you’re doing it right.
-
Offline Backups Are Sacred: If they touch the internet, they’re not a backup—they’re bait.
There are no do-overs after ruin.
6. Beware the Turkey Problem
A turkey fed every day believes the butcher loves him—until Thanksgiving. A network with zero incidents for three years might just be a turkey.
-
Continuous Validation, Not Annual Audits: Trust your controls as much as you test them.
-
Negative Empiricism: Don’t learn from the shiny success story. Learn from the company that got wrecked.
You are not safe because nothing has happened. You are safe when you have survived what should have killed you.
Closing Thought: Security as Immune System, Not Armor
If you’re still thinking of your security stack as armor—hard shell, resist all—you’re already brittle. Instead, think biology. Think immune system. Think antifragility.
Expose your system to small, survivable threats. Learn from every wound. Build muscle. Be lean, not large. Be hard to kill, not hard to touch.
In a world governed by Extremistan, the best cybersecurity strategy isn’t to avoid failure—it’s to get stronger every time you fail.
Because someday, something will break through. The question is—will you be better afterward, or gone completely?
* AI tools were used as a research assistant for this content, but human moderation and writing are also included. The included images are AI-generated.