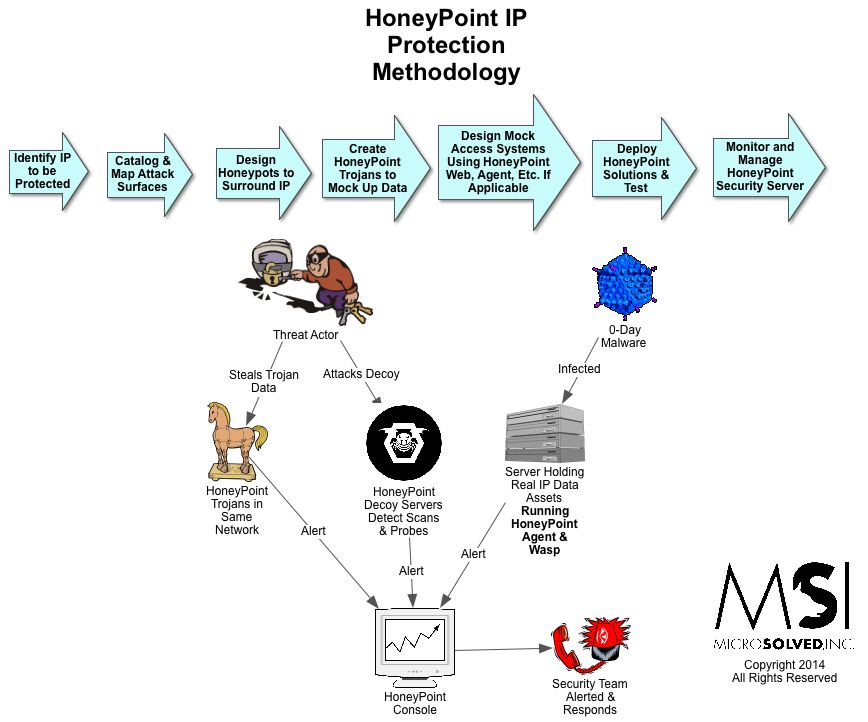
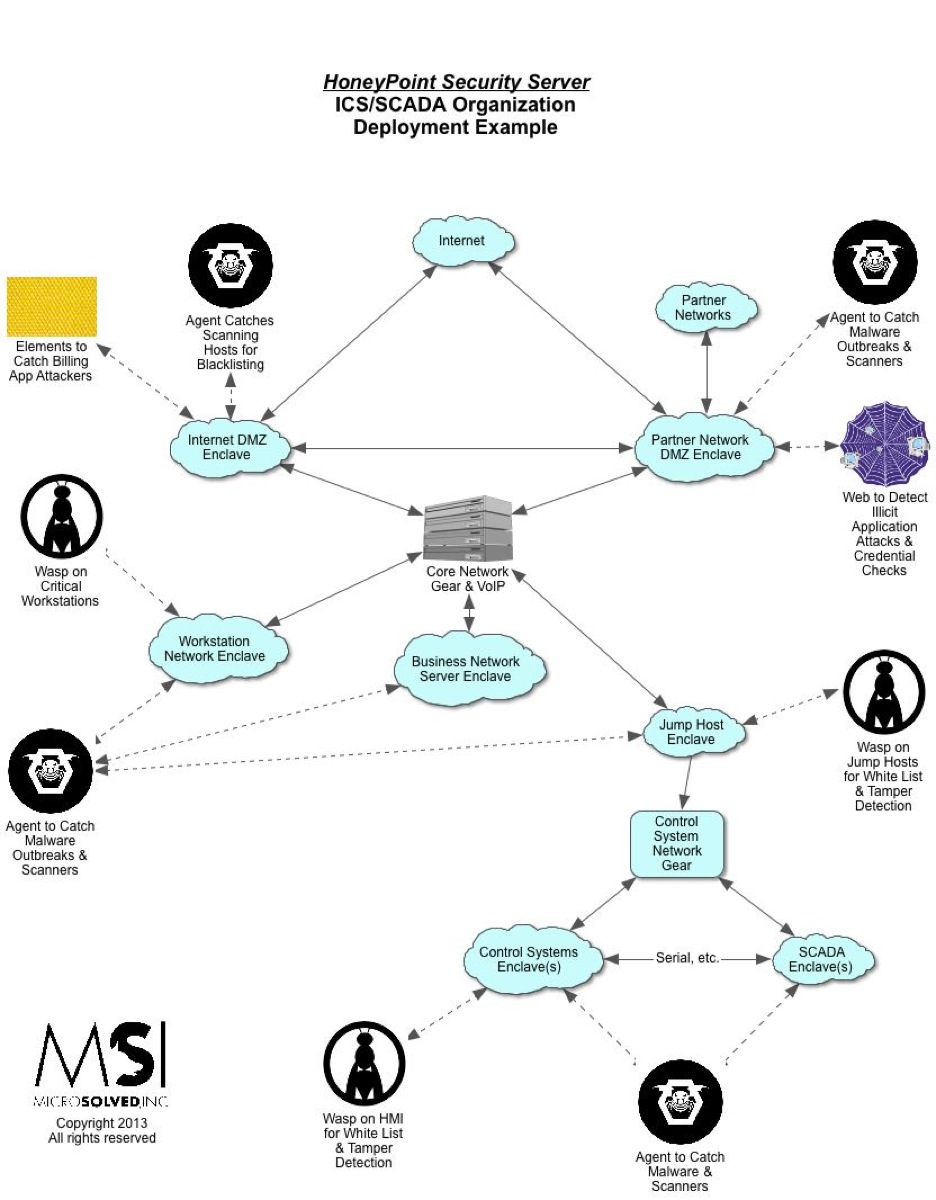
Did you know that less than one out of five security incidents are detected by the organization being affected? Most organizations only find out they’ve experienced an information security incident when law enforcement comes knocking on their door, if they find out about it at all, that is. And what is more, security compromises often go undetected for months and months before they are finally discovered. This gives attackers plenty of time to get the most profit possible out of your stolen information, not to mention increasing their opportunities for further compromising your systems and the third party systems they are connected to.
Of the Big Three strategies for fighting modern cyber-crime, (incident detection, incident response and user education and awareness), incident detection is by far the hardest one to do well. This is because information security incident detection is not a simple process. No one software package or technique, no matter how expensive and sophisticated, is going to detect all security events (or even most of them to be completely honest). To be just adequate to the task, incident detection requires a lot of input from a lot of systems, it requires knowledge of what’s supposed to be on your network and how it works, it requires different types of security incident detection software packages working together harmoniously and, most importantly, it requires human attention and analysis.
First of all, you need complete sources of information. Even though it can seem to be overwhelming, it behooves us to turn on logging for everything on the network that is capable of it. Many organizations don’t log at the workstation level for example. And you can see their point; most of the action happens at the server and database level. But the unfortunate reality is that serious security compromises very often begin with simple hacks of user machines and applications.
Next, you need to be aware of all the software, firmware and hardware that are on your network at any given time. It is very difficult to monitor and detect security incidents against network resources that you aren’t even aware exist. In fact, I’ll go a step further and state that you can improve your chances of detection significantly by removing as much network clutter as possible. Only allow the devices, applications and services that are absolutely necessary for business purposes to exist on your network. The less “stuff” you have, the fewer the attack surfaces cyber-criminals have to work with and the easier it is to detect security anomalies.
The third thing that helps make information security incident detection more manageable is tuning and synchronizing the security software applications and hardware in your environment. We often see organizations that have a number of security tools in place on their networks, but we seldom see one in which all of the output and capabilities of these tools have been explored and made to work together. It is an unfortunate fact that organizations generally buy tools or subscribe to services to address particular problems that have been brought to their attention by auditors or regulators. But then the situation changes and those tools languish on the network without anyone paying much attention to them or exploring their full capabilities. Which brings to the most important factor in security incident detection: human attention and analysis.
No tool or set of tools can equal the organizational skills and anomaly detection capabilities of the human brain. That is why it is so important to have humans involved with and truly interested in information security matters. It takes human involvement to ensure that the security tools that are available are adequate to the task and are configured correctly. It takes human involvement to monitor and interpret the various outputs of those tools. And it takes human involvement to coordinate information security efforts among the other personnel employed by the organization. So if it comes down to spending money on the latest security package or on a trained infosec professional, I suggest hiring the human every time!
—Thanks to John Davis for this post!