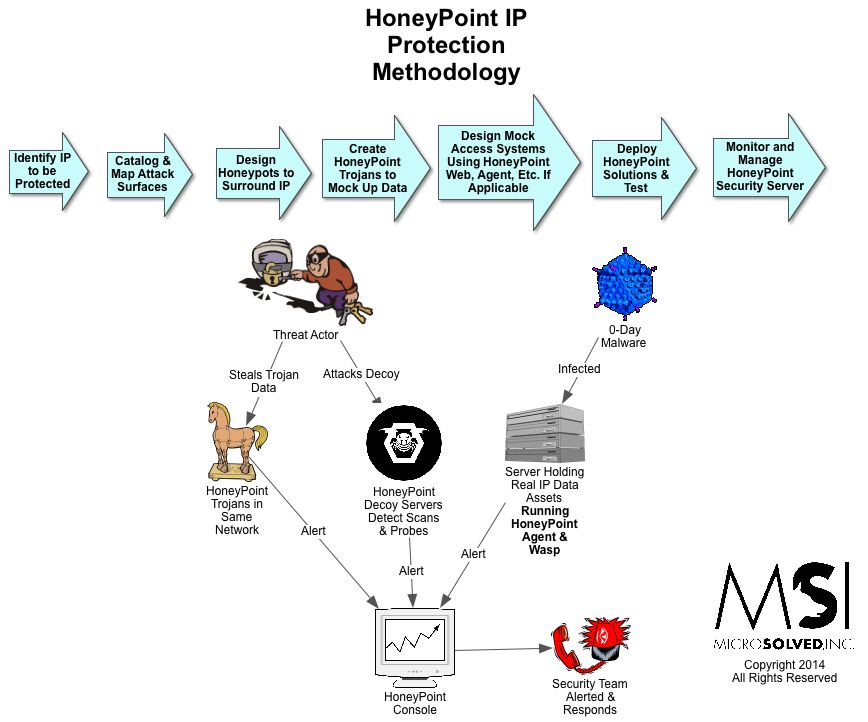
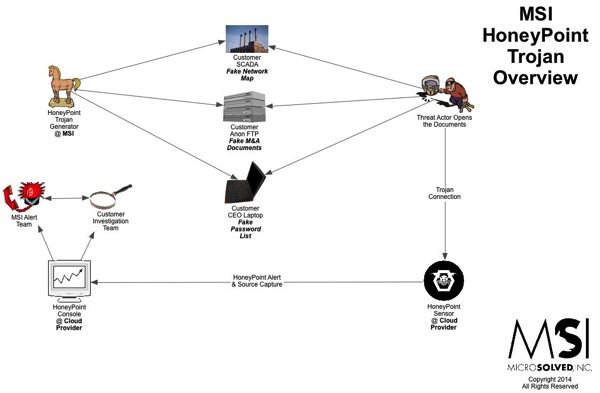
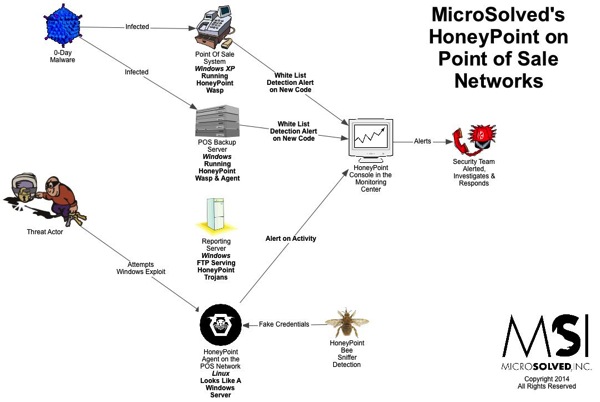
TigerTrax™ is MSI’s proprietary platform for gathering and analyzing data from the social media sphere and the overall web. This sophisticated platform, originally developed for threat intelligence purposes, provides the team with a unique capability to rapidly and effectively monitor the world’s data streams for potential points of interest.
The uses of the capability include social media code of conduct monitoring, rapid “deep dive” content gathering and analysis, social media investigations & forensics, organizational monitoring/research/profiling and, of course, threat intelligence.
The system is modular in nature, which allows MSI to create a number of “on demand” and managed services around the platform. Today the platform is in use in some of the following ways:
- Sports teams are using the services to monitor professional athletes for potential code of conduct and brand damaging behaviors
- Sports teams are also using the forensics aspects of the service to help defend their athletes against false behavior-related claims
- Additionally, sports teams have begun to use the service for reputational analysis around trades/drafts, etc.
- Financial organizations are using the service to monitor social media content for signs of illicit behavior or potential legal/regulatory violations
- Talent agencies are monitoring their talent pools for content that could impact their public brands
- Law firms are leveraging the service to identify potential issues with a given case and for investigation/forensics
- Companies have begun to depend on the service for content monitoring during mergers and acquisitions activities, including quiet period monitoring and pre-offer intelligence
- Many, many more uses of the platform are emerging every day
If your organization has a need to understand or monitor the social media sphere and deep web content around an issue, a reputational concern or a code of conduct, discuss how TigerTrax from MSI can help meet your needs with an account executive today.
At a glance call outs:
- Social media investigation/forensics and monitoring services
- Customized to your specific concerns or code of conduct
- Can provide deep dive background information or ongoing monitoring
- Actionable reporting with direct support from MSI Analysts
- Several pricing plans available
Key Differentiators:
- Powerful, customizable, proprietary platform
- Automated engines, bleeding edge analytics & human analysts to provide valuable insights
- No web portal to learn or analytics software to configure and maintain
- No heavy lifting on customers, MSI does the hard work, you get the results
- Flexible reporting to meet your business needs