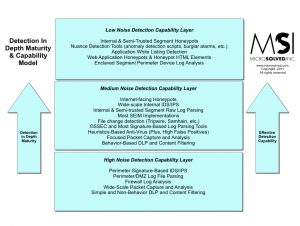
I have been discussing the idea of doing detection depth pretty heavily lately. One of the biggest questions I have been getting is about maturity of detection efforts and the effectiveness of various types of controls. Here is a quick diagram I have created to help discuss the various tools and where they fit into the framework of detection capability versus maturity/effectiveness.
Category Archives: General InfoSec
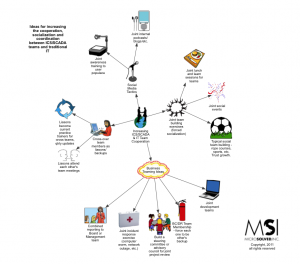
How To Increase Cooperation Between SCADA/ICS and the IT Department
Here is a mind map of a set of ideas for increasing the cooperation, coordination and socialization between the ICS/SCADA operations team and their traditional IT counterparts. Last week, at the Ohio SCADA Security Symposium this was identified as a common concern for organizations. As such, we wanted to provide a few ideas to consider in this area. Let us know in the comments or on twitter if you have any additional ideas and we’ll get them added to a future version of the mind map. Click here to download the PDF.
Control Valuable Data By Using Maps
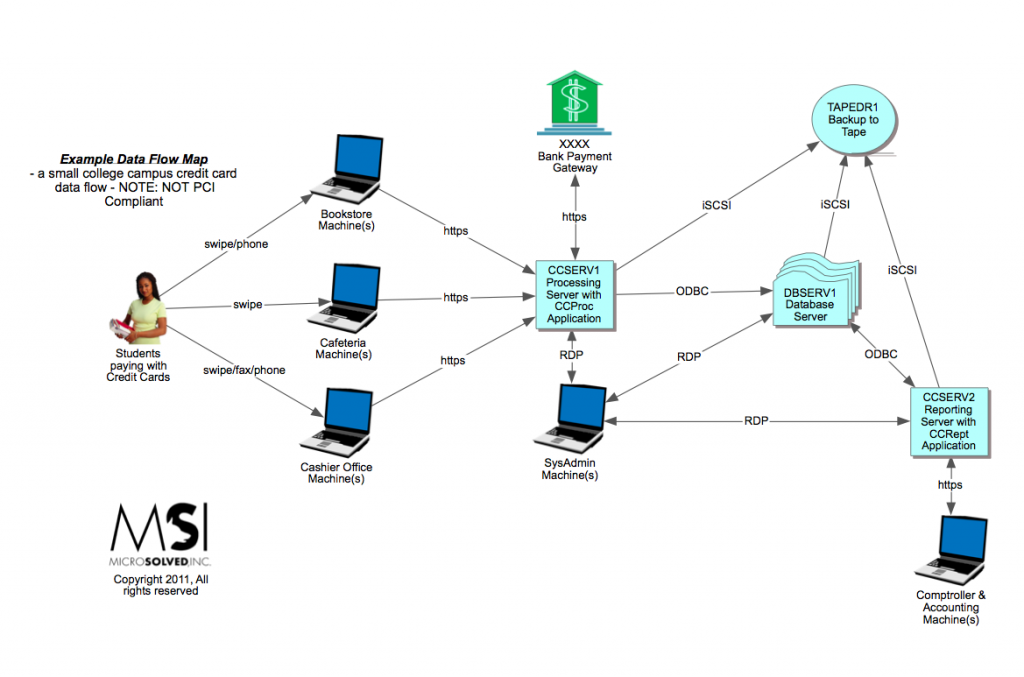
As the battle rages, attackers look for every angle they can leverage in order to access your data. Our team has spent countless hours discussing the importance of identifying what ‘valuable data’ means (it is NOT the same for everyone), learning where that data lives, and understanding how it is accessed. Data flow mapping provides a useful tool that helps illustrate how data moves through any given process or system. When approaching this project in the field, we often see how compartmentalized our business processes are as each person, department, and/or unit knows a little about the target system/process. But when we take an in depth look, rarely does anyone understand it thoroughly! While this philosophy presents a challenge to any organization, the payoff can be priceless- especially in the case of a breach!
These maps are not only helpful to a new employee; but can also explain the system/process to an auditor or regulatory authority in a fraction of the time, and more thoroughly than most employees can. Realizing how our data is handled is vital to the next stage in protecting the data as the battlefield continually changes!
We have to focus on wrapping better controls around our valuable data. Don’t be discouraged by the challenge ahead. Instead, embrace the opportunity to help change the way the world thinks about Information Security! Nothing worth doing is ever easy, and applying this strategy to your environment won’t be either. But as we repeat the process over each facet of our organizations we become more efficient. After all, practice makes perfect!
The graphic below is what the finished product looks like. Yours will look entirely different, no doubt! Don’t focus on this map or this process, but on the underlying principle instead. By combining this with a network map, trust map, and surface map, we can create a comprehensive mechanism to provide useful, accurate intelligence that is easily parsed and processed on demand.
Why a Data Flow Map Will Make Your Life Easier
 It’s impossible to protect everything in your environment if you don’t know what’s there. All system components and their dependencies need to be identified. This isn’t a mere inventory listing. Adding the dependencies and trust rela- tionships is where the effort pays off.
It’s impossible to protect everything in your environment if you don’t know what’s there. All system components and their dependencies need to be identified. This isn’t a mere inventory listing. Adding the dependencies and trust rela- tionships is where the effort pays off.
This information is useful in many ways
- If Server A is compromised incident responders can quickly assess what other components may have been affected by reviewing its trust relationships
- Having a clear depiction of component dependencies eases the re-architecture process allowing for faster, more efficient upgrades
- Creating a physical map in accordance with data flow and trust relationships ensures that components are not forgotten
- Categorizing system functions eases the enclaving process
Don’t know where to start? It’s usually easiest to map one business process at a time. This enables everyone to better understand the current environment and data operations. Once the maps are completed they must be updated peri- odically to reflect changes in the environment.
Click here to see an example of a Data Flow Map. The more you know, the better prepared you can be!
Apple’s iOS5 and the iCloud: Great Ideas, Huge Security Impact
 Wondering how Apple’s iOS5 and the iCloud will affect your life? Check our recent slide deck that tackles some potential challenges as Apple gets ready to roll out their newest creation. In this deck, you’ll learn:
Wondering how Apple’s iOS5 and the iCloud will affect your life? Check our recent slide deck that tackles some potential challenges as Apple gets ready to roll out their newest creation. In this deck, you’ll learn:
- What is key
- iOS5 idealism and reality
- The good news and bad news
- What do do and not do
As always, we’re here for discussion. Follow Brent Huston on Twitter to engage even more!
Chaos, Insecurity, and Crime
 We recently presented the attached slide deck at an OWASP meeting and it was well-received. In it, you’ll learn:
We recently presented the attached slide deck at an OWASP meeting and it was well-received. In it, you’ll learn:
- What are the new targets for hackers?
- The new crimeware model
- What we’re seeing and what we’re not
- Thoughts on controls
Feel free to contact us with questions. Follow Brent Huston on Twitter and engage him. He’s more than happy to talk security!
HoneyPoint Maturity Model
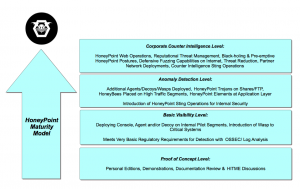 Many folks have asked for a quick review of the way HoneyPoint users progress as they grow their confidence in the product suite and in their capability to manage threat data. To help answer those questions and to give folks a quick way to check out how some folks use HoneyPoint beyond simple scan/probe detection, we put together this quick maturity model to act as a roadmap.
Many folks have asked for a quick review of the way HoneyPoint users progress as they grow their confidence in the product suite and in their capability to manage threat data. To help answer those questions and to give folks a quick way to check out how some folks use HoneyPoint beyond simple scan/probe detection, we put together this quick maturity model to act as a roadmap.MSI Strategy & Tactics Talk Ep. 11: Managing Mobile Security
“We’re not seeing good reporting processes yet. Many organizations… do not know who has these mobile devices or where they are located and what they’re being used for.” – Brent Huston, CEO, MicroSolved, Inc.
Samsung Galaxy, Google Android, Apple iPad — mobile devices are a hot item and consumers are bringing them to their workplaces. Along with the popularity are malware developers who would like nothing better than to steal sensitive information from them. How can you protect your organization’s data from mobile device usage? Discussion questions include:
- Who is managing mobile devices?
- There needs to be some reporting – who does this and who should be involved?
- Who are the groups that should be included when talking about mobile security? How should an organization start their strategy?
- Regarding the data layer: what controls can we wrap around the data itself?
Adam Hostetler, Network Engineer and Security Analyst
Phil Grimes, Security Analyst
John Davis, Risk Management Engineer
Click the embedded player to listen. Or click this link to access downloads. Stay safe!
Yet Another Lesson on the Basics from DigiNotar
 This time it was a Certificate Authority (again). Not just any CA, either, but an official CA that manages the “PKIOverheid” for the government of the Netherlands. In other words, a really important CA, even in a league where most, if not all, CA’s are important.
This time it was a Certificate Authority (again). Not just any CA, either, but an official CA that manages the “PKIOverheid” for the government of the Netherlands. In other words, a really important CA, even in a league where most, if not all, CA’s are important.
What happened? They got breached. They got breached in a way that allowed attackers to create at least 531 rogue certificates with their trust models. How did they get breached? It seems to stem from a combination of attackers exploiting basic issues to gain access, then leveraging more advanced custom skills to get the certificates generated and extrude them. I am basing that opinion on the Fox-IT report located here. (The report itself is well worth a read).
The critical issues identified?
- Lack of a secure architecture for CA servers (1 Windows domain, connectivity from management network)
- Missing patches
- Lack of basic controls (AV, in this case) which allowed exploitation by basic attacker tools such as Cain/Abel
- Poor password policies, logging and management of detective controls
If you follow our blog, attend our talks or listen to our podcasts, you should be seeing this as another reminder of just how critical it is to do the basics. Having powerful tools that no one watches, engaging vendors to do assessments that you ignore and spending money on controls that don’t matter won’t create an effective information security program. Getting the basic controls and processes in place might not protect you from breaches against resourced, skilled attackers completely, either, but it will go a long way toward giving you some protection from the most common threat models. In this case, it might have helped a CA know when they were under attack and take action against their threat sources to mitigate the breach before they got to the crown jewels or in this case, the crown certificates.
The attacker has been posting to Pastebin, (presumably the attacker), that they have access to other CA providers. If you are a CA or run a certificate system, now might be a good time to have someone take an independent third-party look around. It might be a good time to spend a few extra cycles on “just checking things out”.
If your organization is still stuck chasing vulnerabilities and hasn’t done a holistic review of their overall program, this would be a good impetus to do so. It should become an action item to look at your program through the lens of something like the SANS CAG or our 80/20 of Information Security lens and ensure that you have the basics covered in an effective manner. If you have questions or want to discuss the impacts or issues some of these recent breaches have against your organization, give us a call. As aways, thanks for reading and stay safe out there.
MSI Strategy & Tactics Talk Ep. 10: Security For Windows Consumers & Their Home System
“You can be doing all the right things and still get your home machine compromised. It becomes less about prevention and more about what we do when our machines become compromised.” – Brent Huston, CEO, MicroSolved, Inc.
Are you “the computer guy” for your family? Listen in as our tech team discusses common problems of Windows users and steps they can take to help protect their data. Discussion questions include:
- How do Windows users stay safe in a world of modern malware and online crime?
- What do Windows users do when their box gets infected?
- What do you do to secure the Windows boxes of your family members?
- What tools does every Windows box need and how should windows security settings be configured?
- What about the browser?
Adam Hostetler, Network Engineer and Security Analyst
Phil Grimes, Security Analyst
John Davis, Risk Management Engineer
Click the embedded player to listen. Or click this link to access downloads. Stay safe!