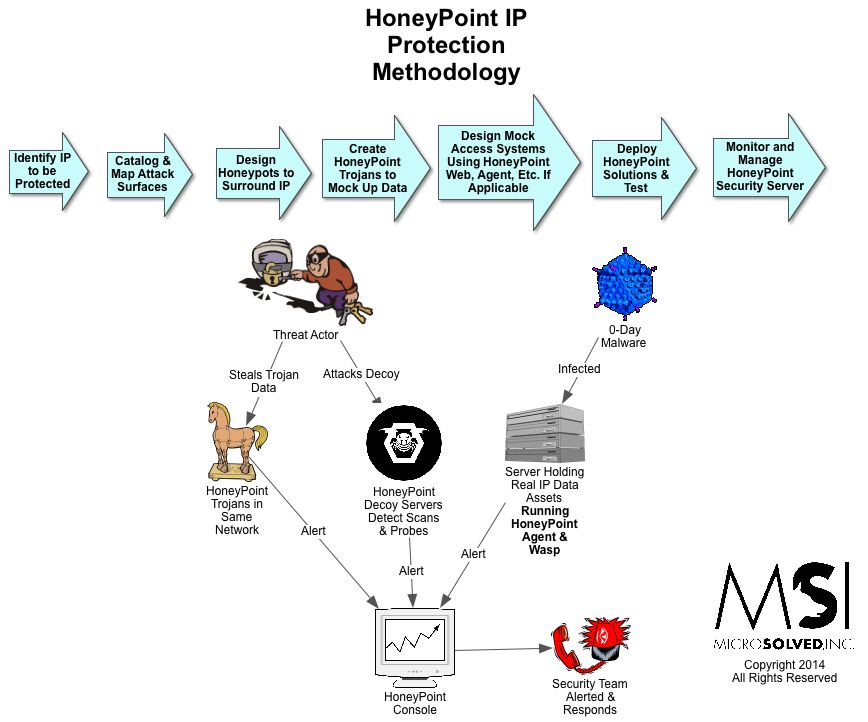
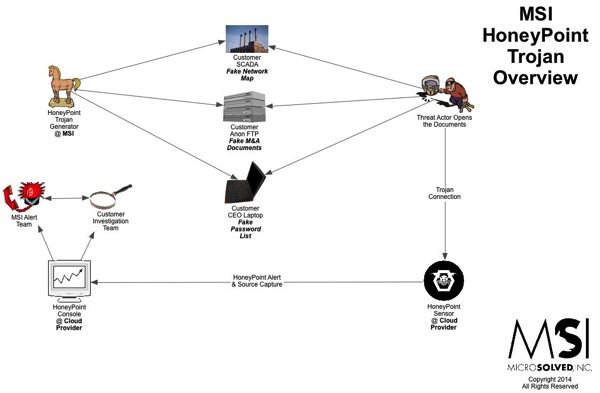
US Concocting People’s War to Hype China Cyber Fears – FreeBeacon is Wrong…People’s Republic of China Rebuttal….
http://world.huanqiu.com/exclusive/2013-08/4195091.html
U.S. media reports the magazine when the internal network fabricated Chinese people’s war planning
RedDragon’s Insight…there have been very few if any ‘cyber’ madness stories pointing the finger at the People’s Republic of China (中華人民共和國) since the traitorous Snowden left for Hong Kong and ended up in Russia working for the Soviet version of Facebook…This latest amplification by Gertz’ ‘Washington Free Bacon sorry Beacon…is yet another attempt by the unknowing and ignorant to cause controversy where there isn’t any…maybe the Free Bacon needs press, I expect the China hyperbole is the ticket..
Nonetheless, below is a story from within the People’s Republic of China indicating that Free Bacon is both incorrect (I wonder if Mr. Gertz speaks or understands Chinese or he is simply manufacturing a new enemy for the DIB?) and full of mis and dis- information…
The suggestion is to read the news story below and decide for yourself…having met with China’s Elite Hackers I can tell you they pout the trousers on one leg at a time just like we do….
Semper Fi –
謝謝您 紅龍
At 07:19 on August 1, 2013 Source: Global Times Author: Chen Chong Sun Micro Flow Limei Wang Xiaoxiong Roshan love Tu draft selection: Wei Zheng
Original title: U.S. media reports the magazine when the internal planning cyber war concocted China
LONDON August 1 message: “Chinese military theorists are the tactics of Mao’s peasant uprising to the United States for the next war,” U.S. “Washington Freedom Beacon” July 30 come to the surprising conclusion, is trying to set off another one pair of “Chinese cyber warfare,” the siege. However, the “Global Times” reporter found that the report mentioned in the article is not what the “internal defense report,” U.S. media’s most in-depth study of the U.S. cyber warfare theory originated from China just for grafted to the sensational.
”Washington Freedom Beacon” July 30 reported that China an internal defense report noted that China’s military is preparing for the cyber warfare, including the launch of the satellite from space attacks and the use of military and civil personnel initiating digital ” people’s war. ” The newspaper said the report, “Space Network warfare research,” the report by the Shanghai Research Center of a home defense drafted four engineers, including disclosure of Chinese cyber warfare and space warfare plans for further details, “This report makes the outside world a rare Beijing to peep into the most secret military projects: Future plans cyber warfare against the United States. ” The report concludes that, in the past, nuclear war strategy is based, but in the information age, with a strategic war should be cyber warfare. “Due to rely on information warfare in space, cyberspace will become a fight for control of the network hotspots.”
”China’s cyber warfare capabilities and anti-satellite missiles and interference projects, the PLA hide the deepest secrets. Held earlier this month in China-US Strategic and Economic Dialogue, the topic of cyber warfare by the U.S. and Chinese military defense officials instituted.” ” Washington Freedom Beacon “In reaching this conclusion, but re-claimed the newspaper received a copy of a translation of the report, marked above dates are December 2012, published in the” Aerospace Electronic Warfare “journal . The journal is the China Aerospace Science and Industry Group 8511 Nanjing Institute publications.
”Washington Freedom Beacon” really got China’s internal defense report yet? “Global Times” reporter July 31 telephone interview, “Aerospace Electronic Warfare” magazine. The magazine one person familiar with the situation told reporters, “Aerospace Electronic Warfare” is a publicly issued bimonthly, anyone want to see you can get this magazine, which is a little secret the contents of the article are not, let alone is the “internal defense report.” Specific to the thing I read entitled “Space Cyber warfare research,” the article, by the Shanghai Institute of Satellite Engineering of Huanghan Wen and other four people to write, mainly for the Chinese readers “Space cyberwar” no unified concept, the lack of clear understanding of the U.S. space-related cyber warfare concepts, definitions introduced to China, is not what the Chinese military theorists in the study of people’s war in cyberspace.
”Global Times” reporter easily downloaded from the Internet this article. In the reporter seems more like a science article describes, beginning on several U.S. cites the definition of cyber warfare. Which describes the characteristics of cyber war, said: “Cyber warfare is not limited to military personnel to participate, with the information systems expertise and skilled personnel, can be implemented cyber warfare, cyber warfare can be said to be a people’s war.”
China National Innovation Strategy Research and Development Center for Strategic Studies cyberspace Renqin An 31, 2011, the “Global Times” said that the people’s war and cyber warfare irrelevant, network warfare is “elite war”, how could become the “People’s war “?
美媒把杂志当内部报告 编造中国筹划网络人民战争
【环球时报综合报道】“中国军方理论学者正在将毛泽东的农民起义战术用于未来对美战争”,美国《华盛顿自由灯塔报》7月30日得出的惊人结论,正试图掀起另一轮对“中国网络战”的围攻。然而,《环球时报》记者调查发现,文章中提到的报告根本不是什么“内部防务报告”,美国媒体把美国研究最深入的网络战理论嫁接到源于中国只是为了耸人听闻。
《华盛顿自由灯塔报》7月30日报道称,中国一份内部防务报告指出,中国军方正在为网络战争做准备,其中包括从太空对卫星发起袭击,并利用军事和民间人员发起数字化的“人民战争”。该报称,这份名为“空间网络战研究”的报告由上海某家国防研究中心的4名工程师起草,其中披露了中国网络战和太空战计划的详细细节,“这份报告使得外界罕见地窥视到北京最为秘密的军事项目:未来针对美国的网络战计划”。这份报告认为,过去,战略战争是以核武器为基础,但在信息时代,具有战略意义的战争应该是网络战。“由于信息战要依赖于太空,网络空间将成为争夺网络控制权的热点。”
“中国的网络战能力与反卫星导弹和干扰项目一样,是解放军隐藏最深的秘密。在本月初召开的中美战略与经济对话中,网络战的话题被美国和中国军事防务官员提起。”《华盛顿自由灯塔报》在得出这一结论时,却又转口声称,该报获得了这份报告的翻译件复印件,上面标注的日期是2012年12月,发表在《航天电子对抗》期刊上。这份期刊是中国航天科工集团南京8511研究所的出版物。
《华盛顿自由灯塔报》真的搞到中国的内部防务报告了吗?《环球时报》记者7月31日电话采访了《航天电子对抗》杂志。该杂志一名熟悉情况的人士告诉记者,《航天电子对抗》是一份对外公开发行的双月刊,任何人只要想看就可以得到这份杂志,里面的文章一点涉密内容都没有,更不可能是“内部防务报告”。具体到那篇题为“空间赛博战研究”的文章,是由上海卫星工程研究所的黄汉文等4人写的,主要针对的是中国读者对“空间网络战”没有统一的概念,缺乏明确的认识,把美国有关空间网络战的概念、定义介绍给中国,根本不是什么中国军方理论家在研究网络空间的人民战争。
《环球时报》记者轻易地从网上下载了这篇文章。在记者看来,文章更像是一篇科普介绍,开头就引用了几个美国对赛博战的定义。其中介绍赛博战特点时说:“赛博战并不限于军人参加,具备信息系统专门知识和技能的人员,都可以实施赛博战,可 以说赛博战是一种人民战争 。”
中国国家创新与发展战略研究会网络空间战略研究中心主任秦安31日对《环球时报》说,人民战争与网络战风马牛不相及,网络战是“精英战”,怎么可能变成“人民战争”?
【环球时报驻美国、英国特约记者 谌庄流 孙微 环球时报记者 屠丽美 王晓雄 罗山爱】