Today, I just wanted to remind folks about the capabilities and use cases for HoneyPoint Security Server™. Got questions? Just ping us at info@microsolved.com.

Today, I just wanted to remind folks about the capabilities and use cases for HoneyPoint Security Server™. Got questions? Just ping us at info@microsolved.com.

A honeypot is a security system that creates a fake trap to attract attackers so that organizations can detect and protect against harmful digital activity.
A honeypot acts as a decoy system or server that is deployed alongside production systems within a network. It is designed to look attractive to attackers by containing vulnerable data, luring them in, and then detecting their attempts, providing organizations with valuable insights into the threats they face.
Honeypots can provide an organization with real-time information about the threats they face, including the techniques used by attackers and the types of attacks they are targeting. Additionally, honeypots can act as an early warning system by alerting an organization when an attack is detected.
There are different types of honeypots available, such as low-interaction honeypots, which simulate vulnerable services but are not actually connected to networks; high-interaction honeypots, which contain full operating systems; and virtual honeypots, which use virtual machines to simulate the behavior of real systems.
We sure do! We have a unique, patented platform for creating, managing, and monitoring distributed honeypots across your environment or in the cloud. You can learn more about it here. To schedule a discussion about the platform and its capabilities, drop us an email or give us a call.
Now through November 1st, 2020 – I am proud to announce a new special for HoneyPoint Security Server.
We are running a “Getting Started with HoneyPoint” promotion. If you’ve ever thought of deploying internal honey pots, but thought that it would take a huge budget to get a real enterprise product deployed, this special is for you!
Now through November 1st, 2020, you can buy 5 HoneyPoint Agents (either stand-alone software, or our decoy host virtual machine (or Raspberry Pi if you bring your own hardware)) and get a 20% discount on your first year. As always, we’ll include the Console, email/phone support and upgrades/fixes for one year for all deployments. The first year cost is $4,000 (a 20% discount). After that, the price returns to the normal $1,000 per sensor, per year as is the current pricing for the platform.
This will get you five deployed honeypots, reporting to a centralized Console and capable of passing events into SEIM solutions or other logging platforms. You also get all of the ability for HoneyPoint to securely emulate thousands of services, capture UDP transactions, perform all of our deception capabilities and even our patented autonomous defensive fuzzing self defense. Read all about it on the website, or by searching for more information on StateOfSecurity.
Of course, you can add on other HoneyPoint components as well, such as Wasp, AirWasp, Bees, Trojans, etc. Additional charges apply.
To learn more or discuss this special offer, you can get in touch with us via this web form, or by calling (614) 351-1237.
In this episode, the tables get turned on me and I become the one being interviewed. The focus is on honeypots, intrusion deception and bounces from technology to industry and to overall trends.
This is a great conversation with an amazing young man, Vale Tolpegin, a student from Georgia Tech with an amazing style and a fantastic set of insights. He really asks some great questions and clarifying follow ups. This young man has a bright future ahead!
Tune in and check it out! Let me know on Twitter (@lbhuston) what you liked, hated or what stuck with you.
One of the most common questions I get is, “Where does attack traffic come from?”. I want to present a quick and dirty answer, just to show you how diverse illicit traffic sources are.
To give you a glimpse into that, here is a list of the top 20 ISPs, based on the number of unique malicious source IP addresses who touched one of my HoneyPoint deployments in a single 24 hour period.
The list:
9 korea telecom
7 hinet
6 dynamic distribution ip’s for broadband services ojsc rosteleom, regional branch “urals”
5 sl-reverse
5 sfr
5 rr
5 chinanet jiangsu province network china telecom no.31,jingrong street beijing 100032
5 china mobile communications corporation mobile communications network operator in china internet service provider in china
4 turknet-dsl
4 superonline
4 sbcglobal
4 chinanet jiangsu province network china telecom 260 zhongyang road,nanjing 210037
3 zenlayer inc
3 virginm
3 verizon
3 totbb
3 jsc rostelecom regional branch “siberia”
3 intercable
3 comcastbusiness
3 comcast
3 charter
3 broadband multiplay project, o/o dgm bb, noc bsnl bangalore
3 as13285
As you can see by the above, the list is pretty diverse. It covers sources in many countries and across both domestic and foreign ISPs. In my experience, the list is also pretty dynamic, at least in terms of the top 10-20 ISPs. They tend to spike and fall like waves throughout different time periods. One of these days, maybe I will get around to visualizing some of that data to get a better view of the entropy around it. But, for now, I hope this gives you an idea of the diversity in sources of attacks.
The diversity also makes it very difficult to baseline log activity and such. As such, there may be some effective risk reduction in blocking ISPs by netblock, if your organization can tolerate the risk associated with doing so. But, more on that in another post. Hit me up on Twitter (@lbhuston) and let me know what your firm’s experience with that type blocking has been; if you’ve tried it or are doing it today. I’d love to hear if it reduced log noise, made traffic modeling easier or led to any specific risk reductions.
Thanks for reading!

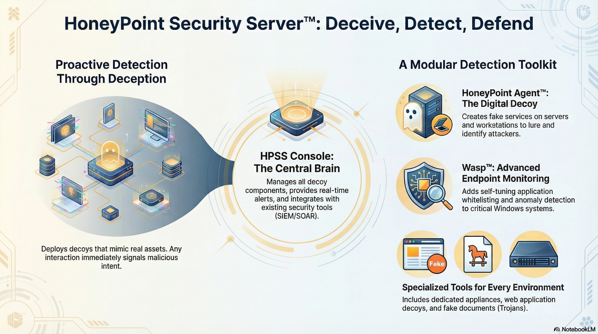
For over a decade, HoneyPoint has been proving that passive detection works like a charm. Our users have successfully identified millions of scans, probes and malware infections by simply putting “fake stuff” in their networks, industrial control environments and other strategic locations.
Attackers have taken the bait too; giving HoneyPoint users rapid detection of malicious activity AND the threat intelligence they need to shut down the attacker and isolate them from other network assets.
HoneyPoint users have been asking us about manageable ways to detect and monitor for new WiFi networks and we’ve come up with a solution. They wanted something distributed and effective, yet easy to use and affordable. They wanted a tool that would follow the same high signal, low noise detection approach that they brag about from their HoneyPoint deployments. That’s exactly what AirWasp does.
We created AirWasp to answer these WiFi detection needs. AirWasp scans for and profiles WiFi access points from affordable deck-of-cards-sized appliances. It alerts on any detected access points through the same HoneyPoint Console in use today, minimizing new cost and management overhead. It also includes traditional HoneyPoints on the same hardware to help secure the wired network too!
Plus, our self-tuning white list approach means you are only alerted once a new access point is detected – virtually eliminating the noise of ongoing monitoring.
Just drop the appliance into your network and forget about it. It’ll be silent, passive and vigilant until the day comes when it has something urgent for you to act upon. No noise, just detection when you need it most.
Use Cases:
More Information
To learn how to bring the power and flexibility of HoneyPoint and AirWasp to your network, simply contact us via email (info@microsolved.com) or phone (614) 351-1237.
We can’t wait to help you protect your network, data and users!
Last week, Hos and I worked on identifying how to emulate a SIP endpoint with HoneyPoint Security Server. We identified an easy way to do it using the BasicTCP capability. This emulation component emulates a basic TCP service and performs in the following manner:
In our testing, we were able to closely emulate a SIP connection by creating a banner file that was blank or contained only a CR/LF. Then we added the appropriate SIP messaging into the response file. This emulates a service where thew connection is completed and logged, and the system appears to wait on input. Once input is received, then a SIP message is delivered to the client. In our testing, the SIP tools we worked with accepted the emulation as SIP server and did not flag any anomalies.
I’ll leave the actual SIP messaging as a research project for the reader, to preserve some anonymity for HPSS users. But, if you are an HPSS user and would like to do this, contact support and we will provide you with the specific messaging that we used in our testing.
As always, thanks for reading and especially thanks for being interested in HoneyPoint. We are prepping the next release, and I think you will be blown away by some of the new features and the updates to the documentation. We have been hard at work on this for a while, and I can’t wait to share it with you shortly!
Want to easily build out a scalable, customizable, easily managed, distributed honey pot sensor array? You can do it in less than a couple of hours with our HoneyPoint Security Server platform.
This enterprise ready, mature & dependable solution has been in use around the world since 2006. For more than a decade, customers have been leveraging it to deceive, detect and respond to attackers in and around their networks. With “fake” implementations at the system, application, user and document levels, it is one the most capable tool sets on the market. Running across multiple operating systems (Linux/Windows/OS X), and scattered throughout network and cloud environments, it provides incredible visibility not available anywhere else.
The centralized Console is designed for safe, effective, efficient and easy management of the data provided by the sensors. The Console also features simple integration with ticketing systems, SEIM and other data analytics/management tools.
If you’d like to take it for a spin in our cloud environment, or check out our localized, basic Personal Edition, give us a call, or drop us a line via info (at) microsolved (dot) com. Thanks for reading!
Another clever use for HoneyPoint™ Agent, running on a Linux system without SMB components, is to have the system listen on the Windows SMB ports (135-139 & 445). The HoneyPoint will then inventory the Windows machines and other SMB speaking tools that attempt to contact it. Since this traffic is pretty routine, it will serve as an inventory mechanism for these types of systems on the local collision domain, or other “same-as-on-the-LAN” segments.
Running HoneyPoint in this fashion has been very useful to several of our ICS customers and has allowed them a quick, and most importantly, passive way to identify hosts on the same segment. No probes or scans needed!
Give us a call today at (614) 351-1237 or email us at info@microsolved.com if you want to discuss how HoneyPoint might be used in your environment. We look forward to talking with you, and as always, thanks for reading!