Spike in HITME NTP Probes Following Recent Exploits



Prior to joining MicroSolved as an Intelligence Engineer, I was the Information Security Officer and Infrastructure Manager for a medical management company. My company provided medical care and disease management services to over 2 million individuals. Throughout my tenure at the medical management organization, I kept a piece of paper on my bulletin board that said “$100,000,000”.
Why “$100,000,000”? At the time, several studies demonstrated that the average “street value” of a stolen medical identity was $50. If each record was worth $50, that meant I was responsible for protecting $100,000,000 worth of information from attackers. Clearly, this wasn’t a task I could accomplish alone.
Enter: MicroSolved & HoneyPoint
Through my membership with the Central Ohio Information Systems Security Association, I met several members of the MicroSolved team. I engaged them to see if they could help me protect my organization from the aforementioned attackers. They guided me through HIPPA/HITECH laws and helped me gain a further understanding of how I could protect our customers. We worked together to come up with innovative solutions that helped my team mitigate a lot of the risks associated with handling/processing 2 million health care records.
A core part of our solution was to leverage the use of HoneyPoint Security Server. By using HoneyPoint, I was able to quickly gain visibility into areas of our network that I was often logically and physically separated from. I couldn’t possibly defend our company against every 0-day attack. However, with HoneyPoint, I knew I could quickly identify any attackers that had penetrated our network.
Working for a SMB, I wore many hats. This meant that I didn’t have time to manage another appliance that required signature updates. I quickly found out that HoneyPoint didn’t require much upkeep at all. A majority of my administrative tasks surrounding HoneyPoint were completed when I deployed agents throughout our LAN segments that mimicked existing applications and services. I quickly gained the real-time threat analysis that I was looking for.
If you need any assistance securing your environment or if you have any questions about HoneyPoint Security Server, feel free to contact us by sending an email to: info@microsolved.com.
This post contributed by Adam Luck.
For those of you that are unfamiliar with the HITME project, it is a set of deployed HoneyPoints that gather real-world, real-time attacker data from around the world. The sensors gather attack sources, frequency, targeting information, vulnerability patterns, exploits, malware and other crucial event data for the technical team at MSI to analyze. We frequently feed these attack signatures into our vulnerability management service to ensure that our customers are tested against the most current forms of attacks being used on the Internet.
It’s also important that we take a step back and look at our HITME data from a bird’s-eye view to find common attack patterns. This allows us to give our customers a preemptive warning in the event that we identify a significant increase in a specific threat activity. We recently analyzed some of the data that we collected during the month of November. We found that over 47% of the observed attacks in the public data set were against the Remote Desktop Protocol (RDP)(often also known as Microsoft Terminal Services). This was more than attacks against web servers, telnet servers and FTP servers combined!
Be sure that all recommended security measures are applied to RDP systems. This should include requiring the use of RDP clients that leverage high levels of encryption. If you need any assistance verifying that you are protected against attacks against your terminal servers, feel free to contact us by sending an email to info(at)microsolved(dot)com.
This post by Adam Luck.
One of the clients we were working with recently wanted me to share their thoughts on deploying HoneyPoint Security Server with the blog audience.
His company recently installed the HoneyPoint Security Server suite into their network. Their management teams were a little nervous, at first, that offering a honeypot to attackers might attract bad people to their networks. But, when the security team explained that these were going to be simply deployed on the INTERNAL networks and not visible from the Internet, so someone would already have to be inside the network to see them, they gained approval. The security team explained that they planned to use HoneyPoint as a supplement to their existing perimeter network IDS, and their log monitoring tools.
The security team convinced their immediate manager of the HoneyPoint product by describing it as a “No Lose” product to deploy. If they dropped in the HoneyPoint Agents and captured bad actors or malware moving in the network, they would win by identifying existing compromises. If they dropped in HoneyPoint and never got a hit at all, they would win, and could tell the management that even upon closer examination with the new detection tools, the network seemed to be clean of malware and overt attacker activity. This, in combination with the other forms of detection and reporting they were doing would further strengthen their position with management that the security team was remaining vigilant.
In the end, the team observed a few pieces of malware within the first 90 days and quickly eliminated the infections. They then began to plan on deploying HoneyPoint Agent into a malware black hole, in coordination with their internal DNS team. As of this writing, the deployment in the new position should go live within 30 days. In most cases, teams using HoneyPoint in this fashion quickly identify other more deeply hidden malware. The security team looks forward to leveraging the data from the HoneyPoint black hole to clean the environment more aggressively.
So, there you have it. Another client strikes a win with HoneyPoint. You can learn more about this “No Lose” product by getting in touch with your MSI account executive. You can also find more information by clicking here.
We are proud to announce the immediate availability of HoneyPoint Security Server training videos. You can now learn more about installing and using the Console, Agents, the HPSS Proxy and soon Wasp, HoneyBees and Trojans.
Jim Klun (@pophop) put the videos together and will continue to build the series over the coming months. Check them out and give Jim some feedback over Twitter. Also, let us know what other videos you would like to see.
You can get access to the videos using the credentials provided to you with your HoneyPoint license. The videos, along with a brand new User Guide, are now available from the distro web site.
Thanks to all HPSS users, and we promise to continue to evolve HPSS and make it even easier and more powerful over the coming year. As always, thanks for choosing MSI as your security partner. We appreciate it and greatly value your input!

MSI is proud to announce the immediate availability of the HoneyPoint Console version 4.0!
The new version of the Console for HPSS is now available for Windows, Linux and Mac OS X. In addition to the Console, new installer tools and documentation is also available.
The new Console finally includes operation as a service/daemon WITHOUT the need to have the GUI running. That’s right, finally headless consoles that work immediately with SEIM and other monitoring tools. Configuration of the Console and management is still available through the GUI, but headless operation is now at the core of the Console product line!
Other improvements include bug fixes, increased error handling, better memory management, improved installers and installation tools and much much more. If you haven’t upgraded your Console or seen the new 4.0 Console yet, we think you will find it much improved.
To obtain the new Console, refer to your QuickStart Guide. It is now available through the HoneyPoint distribution site. No changes to the database or license key are required, however, you must have a current license to qualify for the upgrade. Please back up your Console databases prior to upgrading, though we have experienced no issues with the upgrade process.
Thanks, as always, for choosing HoneyPoint Security Server and MSI. We value your partnership and trust.
MSI has built a reputation that spans decades in and around testing hardware and software for information security. Our methodology, experience and capability provides for a unique value to our customers. World-class assessments from the chip and circuit levels all the way through protocol analysis, software design, configuration and implementation are what we bring to the table.
Some of the many types of systems that we have tested:
To find out more about our testing processes, lab infrastructure or methodologies, talk to your account executive today. They can schedule a no charge, no commitment, no pressure call with the testing engineer and a project manager to discuss how your organization might be able to benefit from our experience.
At A Glance Call Outs:
Key Differentiators:
Other Relevant Content:
Project EVEREST Voting Systems Testing https://stateofsecurity.com/?p=184
Lab Services Blog Post https://stateofsecurity.com/?p=2794
Lab Services Audio Post https://stateofsecurity.com/?p=2565
Here’s another use case scenario for HoneyPoint Security Server. This time, we show the methodology we use to scope a HoneyPoint implementation around protecting a specific set of Intellectual Property (IP).
If you would like an in-depth discussion of our process or our capability, please feel free to reach out to us and schedule a call with our team. No commitment and no hard sale, guaranteed.
If the graphic below is blurry on your device, you can download a PDF version here.
Here’s another quick overview graphic of how HoneyPoint Trojans work. We have been using these techniques since around 2008 and they are very powerful.
We have incorporated them into phishing exercises, piracy studies, incident response, intrusion detection, intelligence gathering, marketing analysis and even privacy research. To hear more about HoneyPoint Trojans, give us a call.
If the graphic below is blurry on your device, you can download a PDF version here.
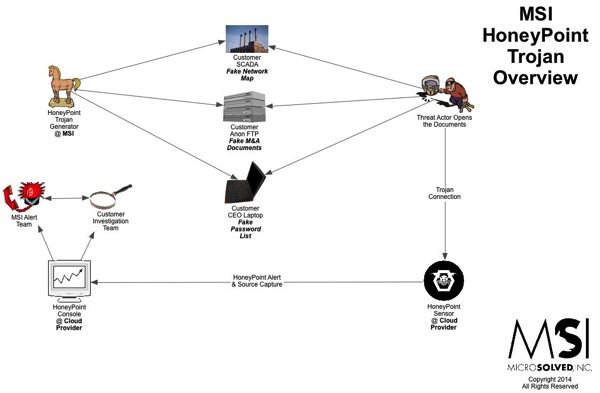
We have been getting a LOT of questions lately about how HoneyPoint Security Server (HPSS) fits into a Point of Sale (POS) network.
To make it pretty easy and as a high level overview, below is a use case diagram we use to discuss the solution. If you would like a walkthrough of our technology, or to discuss how it might fit into your specific use cases, please let us know.
As always, thanks for reading and for partnering with MicroSolved, Inc.
PS – If the graphic below is difficult to read on your device, you can grab a PDF version here.