A honeypot is a trap set to detect or deflect attempts at unauthorized use of information systems. Generally it consists of a computer, data or a network site that appears to be part of a network but which is actually isolated and protected, and which seems to contain information that would be of value to attackers.
It is important to note that honeypots are not a solution in themselves. They are a tool. How much they can help you depends upon what you are trying to achieve.
There are two different types of honeypots: production and research. Production honeypots are typically used by companies and corporations. They’re easy to use and capture only limited information.
Research honeypots are more complex. They capture extensive information, and used primarily by research, military, or government organizations.
The purpose of a production honeypot is to mitigate risk to an organization. It’s part of the larger security strategy to detect threats. The purpose of a research honeypot is to collect data on the blackhat community. They are used to gather the general threats against an organization, enabling the organization to strategize their response and protect their data.
The value of honeypots lies in their simplicity. It’s technology that is intended to be compromised. There is little or no production traffic going to or from the device. This means that any time a connection is sent to the honeypot, it is most likely to be a probe, scan, or even attack. Any time a connection is initiated from the honeypot, this most likely means the honeypot was compromised. As we say about our HoneyPoint Security Server, any traffic going to or from the honeypot is, by definition, suspicious at best, malicious at worst. Now, this is not always the case. Mistakes do happen, such as an incorrect DNS entry or someone from accounting inputting the wrong IP address. But in general, most honeypot traffic represents unauthorized activity. What are the advantages to using honeypots?
- Honeypots collect very little data. What they do collect is normally of high value. This eliminates the noise, making it much easier to collect and archive data. One of the greatest problems in security is sifting through gigabytes of useless data to find something meaningful. Honeypots can give users the exact information they need in a quick and easy to understand format.
- Many security tools can drown in bandwidth usage or activity. NIDs (Network Intrusion Detection devices) may not be able to handle network activity, and important data can fall through the cracks. Centralized log servers may not be able to collect all the system logs, potentially dropping logs. The beauty of honeypots is that they only capture that which comes to them.
Many of our clients swear by our HoneyPoint family of products to help save resources. With its advantages, it’s easy to see why! Leveraging the power of honeypots is an excellent way to safeguard your data.
How HoneyPoint Security Server Minimizes Risk For Your Network
 If you’re looking for a security tool that goes beyond NIDS, you’re in luck.
If you’re looking for a security tool that goes beyond NIDS, you’re in luck.
MicroSolved’s HoneyPoint Security Server has revolutionized the ease and power of what honeypots can do and be. With the emergence of HoneyPoint Wasp, you can also apply the HoneyPoint magic to your Windows desktops.
HoneyPoint Wasp monitors your desktops for any new applications it has not seen before (Anomaly Detection). Should Wasp detect new code, the end-user will never see a pop-up alert. Instead, you will be notified and able to quickly take action. Should the notification go without follow-up action, HoneyPoint Wasp assumes the allowed application, and no future notification will be sent to the console (Self-Tuning White Listing).
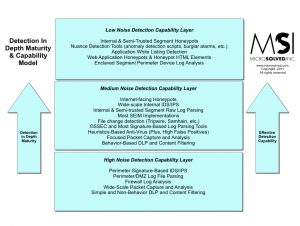
As you’ll see in a moment, the HoneyPoint Security Server is much more than a mere intrusion detection system.. It’s an underlying framework of rock-solid code that’s been built to achieve three important goals: identify real threats, isolate and tamper with the attacker’s results, and “smart” detection processes that allow you to target attacker availability.
Let’s take a look at each of these goals, and why they matter to what you’re doing online…
Click to continue…