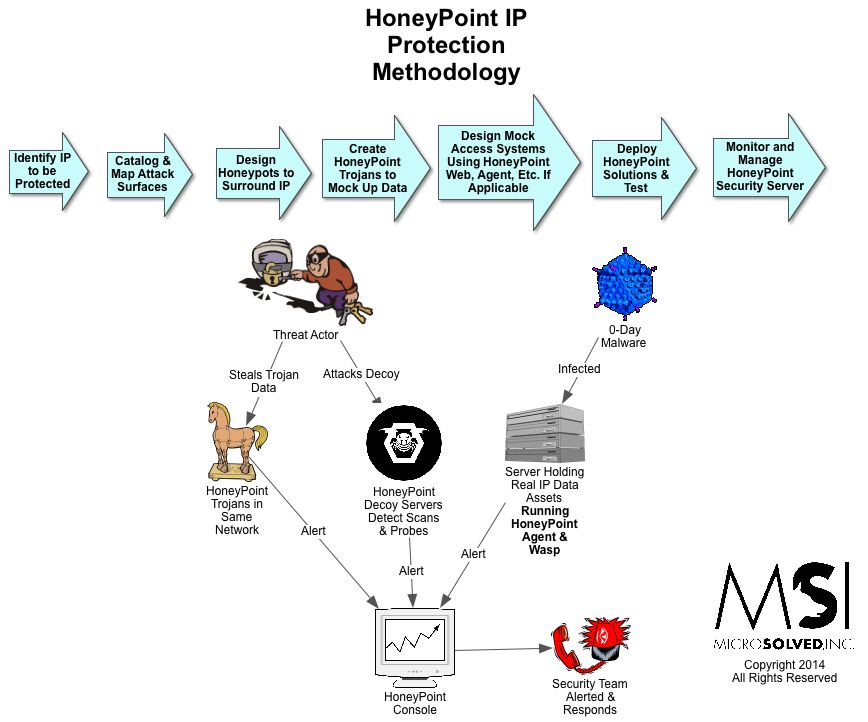
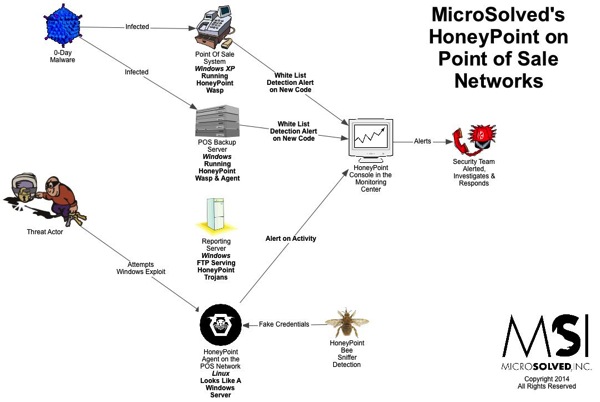
Good Day Chinese Cyber Conflict Fans…the following post about Chinese Information Warfare Doctrine as written by Lu Yong, Department of National Defense Strategy, 中國人民解放軍, 總參謀部..yes The People’s Liberation Army…circa 2005. This post was discovered by the Red Dragon a week ago and has already been removed from the web…sinister?
Here it is folks, a glimpse into Chinese Information Warfare Doctrinal Development in 2005…
“Information Warfare Challenges and Countermeasures For Executing the People’s War”
http://www.chinamil.com.cn/site1/zgmb/2005-08/18/content_148840.htm
Lu Yong, Department of National Defense Strategy, 中國人民解放軍, 總參謀部
People’s War is a traditional weapon to defeat the enemy army. Since the 90s of last century, with the world’s burgeoning revolution in military affairs, and high-tech weapons in the war widely used form of war started by the mechanized warfare to information warfare changes, “Information warfare is the major wars of the 21st century form “has become a consensus. In the semi-mechanized and mechanized warfare formed and developed the people’s war, and how to address information warfare challenges, how to continue in the information war play its unique advantages to ensure winning future possible war, is we are faced with a major theoretical issues and practical issues urgent. First, information warfare launched the people’s war is faced with severe challenges (a) the purpose of information warfare, the limited size of the previous national war, the country is facing severe challenges the way to meet the enemy since World War II, especially in the last century 80 years, the international situation has undergone major changes, “peace and development” instead of “war and revolution”, a theme of the times. Correspondingly, local war to replace the previous world wars and the full-scale war, become the world’s major warfare. We may face future information warfare, must be local wars, which makes the whole war, lasting way to defeat the enemy is facing severe challenges.
First, the purpose of information technology local wars, limited size, the possibility of universal war greatly reduced. Compared with the world wars and the full-scale war, information local war by political, economic, diplomatic and other factors more directly, the purpose of war is often limited to a certain political and economic goals, the scale of war is also controlled in a certain range. In this case, the state can not disrupt the overall national development strategic steps, the state transferred from peacetime “Everything for the front, everything for victory in the war,” the wartime regime, to mobilize all the people participate in the war. Secondly, information warfare, the power of the warring parties is not primarily the number of competitions contest, but the quality of competition, the number of people’s war in the traditional pattern of strengths compensate for disadvantages quality hard work. In information warfare, weapons and equipment quality exists “Time difference” has been impossible to quantify the advantage to make the war directly to the performance of quality and efficiency, technology-intensive confrontation between elite standing army.
Therefore, national mobilization, national war is neither necessary, nor can fundamentally change the balance of forces contrast. Again, the limited capacity of information warfare battlefield, the war directly to the masses are severely constrained. Information warfare battlefield often limited to the parties directly within a certain depth, certain waters or airspace, such as the Anti-Japanese war the Japanese into my territory impossible to reproduce the situation, which makes the past that a large number of armed and unarmed masses to direct war Traditional methods are severely constrained, even though the war is also useless. (Two) Information sudden outbreak of war increased, shortening the process of war, lasting defeat the enemy’s strategic facing severe challenges in the past war, war lasted a relatively long time to carry out the people’s war, it is possible to mobilize the masses to participate in the war, give full play to the advantages of quantity, quality and quantity of weapons and equipment to make up for the disadvantages, to make up for military, material deficiencies, gradual change through sustained combat enemy forces, and ultimately win the war. This is the victory of people’s war past, the basic experience, but also from the other instructions, the traditional gathering of people’s war and the release force take a long time.
Information warfare is one of the important features of the sudden outbreak of war increased, the process of shortening the war. Provoke a war party, in order to create a fait accompli and a more favorable situation, often with a sudden attack caught off guard the way to the other side to blow, and seeks to achieve a decisive victories in a short time. In addition, information warfare consumption increased dramatically, both sides are trying to combat a quick fix with little cost to achieve the purposes of war. In this case, change through sustained combat enemy forces greatly reduces the possibility. Therefore, the information warfare conduct civil wars, not only faced with how to release in a short test of the people’s war Weili, and the possibility of lasting defeat the enemy becomes negligible. (Three) high-tech information warfare, and more in the sparsely populated border and coastal areas as well as sea and air for the masses traditional way of war frontline facing serious challenges in the past war, a large scale because of the war and the relatively tech weaponry low, logistical and equipment support technical requirements are not high, coupled with the war mainly on land, ordinary people will be able to directly participate in a little training operations, delivering supplies to the front or to the way frontline. Therefore, human and human frontline war is war frontline people’s traditional way of war.
In the information war, the warring parties tend to use one or the most advanced aircraft, ships, tanks, artillery, missiles, and other cutting-edge technology, greatly improve the technical content of war, battle space from the past in order to develop a terrestrial land-based , sea, air, space, electricity multidimensional space to support security operations equipment and technical means of highly specialized equipment. In addition, information warfare unit time combat strength increases rapidly, fighting more intense, direct combatants psychological and physical quality put forward higher requirements. No rigorous professional training not only ordinary people cannot use advanced weapons and equipment and well-trained and have high-tech weapons of the enemy to make a direct confrontation, and even logistical and equipment support is difficult to carry out the task. Coupled with the war mostly in sparsely populated border and coastal areas as well as sea and air, greatly increased the masses direct war frontline of difficulty. Therefore, information warfare, the masses will direct the war, supporting the front of the main changes is indirect war, supporting the front main support for the war is also supported by the human and material resources into technology-based intelligence support based.
(Four) of information warfare undergone revolutionary change, people’s war is facing severe challenges the traditional tactics of people’s war in the long-term practice, the army formed a set of flexible strategies and tactics of people’s war, created numerous “survival of the fittest,” the war miracle. However, we should see that in the past we have conducted a people’s war, is the relatively low level of weaponry semi-mechanized warfare, the main battle, the battle is on the ground, thus forming the main form of combat – trench warfare, warfare and a series of guerrilla warfare and related, are conducive to our full advantage of the number of people. Especially in irregular warfare guerrilla warfare that, in the proportion of combat operations and the impact of the outcome of the war is relatively large. Engels pointed out: “Once technological advances can be used for military purposes and has been used for military purposes, they will almost immediately forcibly, and often is a violation of the will of the commander of the changes caused by warfare or even revolution.”
With IT The rapid development of high-tech weapons and the widespread use of information warfare revolutionary change taking place. For example: Battlefield to the five-dimensional space development; missiles, electronic warfare, network warfare, and many other new combat styles have been in war; C4 ISR against the increasingly fierce battle to win control of information and operational command of the army to become the premise and focus; to become independent of combat raids, much warfare, night fighting, the proportion of firepower increases; emphasize more arms, a variety of weapons to combat the overall implementation of the integration of diverse, asymmetric, non-contact, non-linear operations become an important mode of combat, etc. and so on. In this case, the traditional to the Army mainly to ground-based battlefield warfare, warfare, guerrilla warfare combat forms and information warfare will be difficult to adapt to the requirements. For example, in past wars, melee midnight oil has been the army’s forte. But in the information war, faced with advanced surveillance technology and long-range precision strike weapons of the enemy, we will be faced with melee midnight oil does not rely on rope, unseen challenges, and even enemies in the night-side occupy a greater advantage.
How to deal with the challenges of information warfare, the development of people’s war strategy and tactics, to carry out the people’s war to become an urgent problem.
Second, information warfare still insist on carrying out the people’s war (a) information warfare does not change the inherent social and political attributes of war, still have to carry out the basic conditions of the people’s war and class produced since private ownership since the war is never left over politics. Compared with previous wars, although the scale of information warfare, duration, and other aspects of weapons and equipment have undergone significant changes, showing a lot of new features, but the war itself has properties and not because of social and political development of warfare change.
Information warfare is still a continuation of politics, there is still justice and injustice of distinction, the nature of war and the people’s support or oppose the war are still often contributing factors, the basic conditions for the conduct of civil war, that the justice of the war and mass still exists. The justice of the war is the political basis for the conduct of civil war, but also an important factor in the outcome of war. China’s socialist nature and a defensive national defense policy decisions for our future information warfare is necessarily oppose hegemonism and safeguarding national security and unity, the protection of national survival and development interests, building a moderately prosperous society to ensure the smooth conduct of the just war . The justice of this war is that we carry out in the information warfare solid political foundation for the people’s war is our war to win the final victory of the future fundamental guarantee.
War mass is the source of strength to win the victory. Our future of information warfare, represents the fundamental interests of the overwhelming majority of people just war, and thus be able to get the full support of the masses. Information warfare is a comprehensive national strength, is the political, economic, military, technological, diplomatic, cultural, social and psychological fronts, including the overall war. Although the majority of the people cannot direct a large scale as before the war, supporting the front, but they are in the war embodied the role of the masses through the comprehensive national strength of support and backing for the war action reflected. In this sense, the people and the comprehensive national strength, and is inextricably linked to the outcome of war in the vast masses of people, there remains a great power war deepest roots, as long as this kind of hidden among the great masses of the people forces play out, we can still win the information war.
(Two) information war did not change the outcome of the basic laws of war, the determinants of the outcome of war is still the person information warfare, the growing importance of weaponry, an advantage in weaponry easier to win the war party initiative and even war. However, no matter how the change in the form of war, the basic law of the outcome of war is constant, that is, people are the main body of the war, the determining factor is winning the war, weapons and equipment is an important factor in the decision outcome of the war. In information warfare dominance and decisive role, not because of the extensive application of high-tech weaponry and all reduced. Engels long ago: “gun that he is not moving, you need to by a brave heart and a strong hand to use them.” Then advanced weaponry, once removed from the people, will lose its proper performance. U.S. Department of Defense submitted to the U.S. Congress in the Gulf War report: “Winning the war victory is people, not machines or technology.” Justice of the people’s war and mass decisions, our combatants are equipped with more high political consciousness and consciously contribute to achieve the purpose of the war, they better than the enemy weapons in the hands full performance.
Practice shows that war, weaponry weaknesses, you can play to people’s subjective initiative to change. Person’s conscious activity, not only in understanding the dynamic laws of war, revealing the possibility of victory, the most important is to actively create conditions for the use of various means of victory possibility into reality. Information warfare unprecedented fierce, brutal, war scale and process more vulnerable to a variety of factors, which also enhances the role of people in the war. Weaponry at a disadvantage in the case, as long as the person’s subjective initiative into full play, relying on the excellent political and military qualities, based on the existing equipment, creating and choosing the right strategy and tactics to achieve the best combination of people and weapons, we will be able to superior weaponry against the enemy find ways to make up for the lack of weapons, and promote superior enemy on the battlefield transformed my bad posture, and ultimately win the war.
(Three) for the development of information technology to carry out the people’s war has injected new vitality into this world, things are always dialectical, we must address the information war against the people’s war presented challenges, while also saw rapid information technology development but also to carry people’s war has injected new vitality. First, the rapid development of information technology, in order to build a strong people’s war potential to provide a new historical opportunity. Since the reform and opening up, Deng Xiaoping’s “Science and technology are primary productive forces” and Jiang Zemin’s “education” under the correct guidance of strategic thinking, China’s information technology as the representative of the rapid development of high-tech, cutting-edge technology in a number of breakthrough has been made, in biotechnology, computer technology, rocket technology, satellite communications technology, superconducting materials and other fields of research, has been close to or reach the world advanced level.
At present, the annual output value of China’s information industry to more than 2 times higher than the GDP growth rate for the overall national socio-economic structure of the increasing influence for the conduct of the people’s war has laid a relatively solid material and technological foundation. Secondly, the rapid development of information technology, the war for the people supporting the front provides a new technical support. The level of development of science and technology determine the masses of the people to participate in and support the war, way, way. Although the material basis of information warfare and warfare has undergone a fundamental change, but the people on the course and outcome of the war has not reduced, but with the advancement of science and technology as well as improving the quality of people’s technology and growing. Compatible with the characteristics of modern high-tech military and civilian increasingly prominent in the current level of information of our military forces with a larger gap between the Western powers in the case, widely hidden in the masses of scientific and technological resources, will be the future of information warfare army survival of the fittest and the strong support necessary complement. As long as these potential technological forces in a planned, organized mobilization, we can effectively compensate for the overall military weaponry disadvantage, the formation of local areas, local battlefield technological advantages, to achieve survival of the fittest.
Finally, the development of information technology for innovative tactics to expand the people’s war, the new space. As Mao Zedong pointed out: “the world of things, always a thing down, there is one thing offensive, it also has a thing down. …… We believe that relying on the people, the world would not unassailable ‘magic’ . “On the one hand, the information it has its advanced weaponry side, but there are also weaknesses and limitations. Especially advanced information technology structure is very large and complex weapons systems, it is difficult for all-round protection. In recent years, several global epidemic of vicious computer viruses caused huge losses for countries that modern information systems vulnerability proof. On the other hand, the development of information technology, people’s war for us to provide new technical means, expanding the innovative tactics of people’s war room.
In the past people’s war, we have to rely on relatively backward technology and weaponry, yet it can create a lot of strategy and tactics to defeat the enemy. Today, we already have in information technology for a foundation, but also for the specific characteristics of information warfare, transformation and creating new tactics, research and exploration play win the information war “trick.”
Third, information warfare to carry out the people’s war Countermeasures (a) accelerate the development of comprehensive national strength, and lay a solid foundation of people’s war of information warfare in the final analysis is a comprehensive national strength. Refers to a country’s comprehensive national strength have all the resources and material and spiritual strength, marking the country’s economic, political, technological, military, cultural and other aspects of the overall level of development. To carry out the people’s war winning the information war, you must have a strong comprehensive national strength. On China’s national conditions, in order to accelerate the development of comprehensive national strength, lay the foundation of people’s war, we must focus on grasping the following aspects:
First, to develop the economy. Economic strength of a country’s comprehensive national strength is an important indicator. Strong economic strength, winning the information war can lay a solid material foundation.Meanwhile, the economic strength is the material basis for the modernization of national defense, there are no certain economic forces for support, defense modernization will lose the foundation. Therefore, we must persist in taking economic construction as the center, concentrating on the development of social productive forces, the country’s overall economic construction to consciously obey.
Second, in order to accelerate the development of high-tech information technology as the representative. On the one hand, science and technology to enhance the comprehensive national strength has a decisive, transformative role. In the current form of society by the industrialized to the process of information, who can seize the technology “commanding heights” and “frontier”, whoever may enhance the comprehensive national strength to win. On the other hand, science and technology are primary productive forces, but also the first combat, defense construction is inseparable from the support of advanced science and technology. Especially information technology compared to other technologies, the military and civilian compatibility stronger, the new information technologies emerging, in accelerating national and social information, but also for the military information construction provides a rare historical opportunity.
Third, comprehensively promote the construction of military information, and constantly enhance military strength. After the war directly to the performance of military forces of the contest, to winning the information war is inseparable from a strong line with the requirements of the military information warfare. To seize the world’s new military revolution brought to the army building historic opportunity to accelerate weaponry leapfrog development, modernization of the means to achieve the people’s war; unswervingly implement the strategic project, training a large number of qualified military personnel; at all levels to strengthen joint and combined arms training to improve joint operational capabilities; according elite, synthesis, efficient principle, establish and perfect an appropriate scale, reasonable structure, organization lean, agile command of military system; study the characteristics of information warfare, innovation and the development of information warfare theory.
Fourth, for the information war characteristics, strengthen national defense reserve forces. For information militia building should be the characteristics of high-tech warfare, and universality in keeping the masses on the basis of outstanding quality construction. Primary militia and militia on the distinction between ordinary and should not be confined to the age criteria, but to combine their technological quality measure. To further reduce the size of infantry units, focus on strengthening the missiles, artillery, communications, chemical defense, information and other high-tech special unit of the building. Reserve forces to comprehensively enhance the quality of construction, vigorously improve the rapid mobilization and the ability to carry out combat missions, narrowing the gap with the active forces fighting efforts to achieve the establishment of an appropriate scale, reasonable structure, compiled scientific, reliable and workable objectives reserve forces.
Fifth, to carry out various forms of national defense education, improve national defense. The strength of the concept of national defense exhibit a country preparing for war ideological foundation is solid, countries in the world to enhance the national defense concept placed in improving comprehensive national strength in an important position. To adhere to the masses of people’s war, we must carry out effective, diverse forms of national defense education, so that the masses has always been to establish a strong national defense, information warfare is carried out in the people’s war to lay a solid ideological foundation.
(Two) features in-depth study of information warfare, development and innovation strategy and tactics of people’s war strategy and tactics of people’s war, is to carry out the soul of the people’s war. As the saying goes: “The Sword inferior to sword better than people.” In past wars, people’s war has been able to repeatedly create a “survival of the fittest” miracle, one of the important reasons is that we have a set of adjustable strategy and tactics. In the future for a long period of time, we will be at a disadvantage on the weaponry, and the traditional people’s war strategy and tactics as the development of warfare changes facing severe challenges, so winning the information war under conditions of people , must examine the characteristics of information warfare, development and innovation strategy and tactics of people’s war. Create new tactics in the development process, should focus grasp the following principles:
Ffirst, to establish and adapt to information warfare operational concepts. Since there has been no information warfare military practice, so in the process of creating new tactics, the concept of mechanized warfare vulnerable bondage. Therefore, the idea is to create new tactics update the premise that only break the shackles of old ideas, establish and adapt to information warfare operational concepts in order to provide a fresh perspective, with the correct way of thinking to create new tactics. For example: In the assessment of combat forces, we should abandon the labor-intensive, the number and scale of their concepts, technology-intensive, quality and efficiency concepts; choice of target in combat, to abandon the idea of annihilating the enemy’s effective strength-based, establish a centralized main forces to fight the enemy vital concept.
Second, pay attention to the traditional military tactics absorb nutrients. Information warfare is a new form of war, our military has created in the last war tactics, may not apply to today’s wars, and some tactics need to abandon, and some need to be improved. We study and research the traditional tactics of war, not in the future information warfare copy of these tactics, but to learn the older generation of revolutionaries, military strategist creating new tactics stand, viewpoint and method. This is our future development and creating new tactics and source of wisdom. For example, in China’s Revolutionary War created a “concentrate superior forces to fight a war of annihilation” of war, in the information war, as a means of long-range precision strike extensive use of the practice of concentration of forces no longer feasible. However, we should understand the tactics of Mao Zedong created the spiritual essence, that the enemy superior in the case of my poor, through a certain method, the local formation of the war situation in who wins. This idea is still in the information war has important guiding significance. We can use this as a guide, according to the specific characteristics of information warfare, the development of the traditional tactics to “concentrate superior firepower to fight the enemy vital” new tactics.
Third, the combination of the actual record of our military tactics. Creating new tactics, not behind closed doors, not on paper, must be combined with the actual situation of our army. Currently, the army is actually the largest in weaponry compared with the developed countries there is still a big gap, though they have some advanced weaponry, but still in a lot of low-tech equipment. Which determine our tactics neither copying Western countries of war, in order to avoid committing “Porgy and dragon than treasure” low-level errors, nor imagined, impractical so-called “new tactics.” Measure one kind of tactics is correct or not, not to see how its name sounds good, how novel methods, means, how advanced the key depends on whether it is really effective in combat. Enhance the value of research tactics, is that correct tactics to make up the gap weaponry to achieve superior weaponry with inferior equipment to defeat the purpose of the enemy. We should adhere to the “you hit, I hit my”, the focus on tactical innovation to existing equipment on high-tech enemy and seize enemy weapons and equipment information some of the weaknesses, give full play to existing weapons equipment performance, and strive to me for so long, and strike the enemy’s weaknesses, research, and create a “soil”, “foreign” combination of low high school weaponry combined tactics. (Three) to establish a sound mechanism for rapid mobilization of national defense, to ensure the people’s war potential for rapid accumulation and transformation of information warfare to carry out the people’s war, faced with the short duration of the war and the people gathered the forces of war and transformation contradiction between the relatively long time. To resolve this conflict, we must establish a sound mechanism for rapid mobilization of national defense. The range includes the formation of rapid military expansion and expand quickly, persons and goods transport and complement fast, fast track to a wartime economy, the restructuring of the industrial structure and expand military production and fast; rapid mobilization mechanism of this standard is to be able to adapt to the information sudden outbreak of the war, the war is characterized by short duration, so that the potential of the people’s war in a very short time and quickly gathered quickly converted into national defense capabilities. Establishment of mechanisms for rapid mobilization of national defense, for the power of the people’s war play, winning the information war has very important significance.
Rapid mobilization mechanism must have the following elements: First, clear objectives and tasks. Should be included in national defense mobilization of economic and social development plans, incorporating national defense and army building master plan, clearly defined stages at different times under different circumstances and people’s armed mobilization, economic mobilization, civil air defense mobilization and mobilization readiness transportation and other aspects of the target with the task.
Second, laws and regulations are complete. On the mobilization of rights and obligations, rewards and penalties, responsibilities and benefits should be based on the laws and regulations in the form of regulations, the mobilization of all aspects of the various aspects and rule-based, law. Third, the mobilization plan carefully. Troops, economy, transportation, civil air defense, telecommunications, health and other aspects of the mobilization of both careful planning in order to prepare for mobilization in peacetime, wartime mobilization provide the basis for implementation.Army and local levels, according to the national mobilization plan to develop this level of mobilization plans and safeguards.
Fourth, science and technology to mobilize prominent position. In information warfare launched the people’s war, the way people’s war frontline war intelligence and intelligence is mainly supporting the front, which determines the future of science and technology for national defense mobilization will be the prominent content.
Fifth, the formal procedures quickly and efficiently. According to the characteristics of information warfare, military departure from China’s national conditions, to establish a war in the war potential into the strength of the effective ways and methods. For example, the expansion of the armed forces, civilian products, converting, transportation capacity for the acquisition, implementation of civil air defense, compensation for economic losses as well as other financial and material resources mobilization, should form a set of rapid and effective mobilization of forms and procedures, so that the people’s war bringing power and conversion speed can meet the requirement of information warfare.
(Four) combining various approaches to play the overall power of the people’s war of revolutionary war in the past, an important part of people’s war, is dominated by the armed struggle, the combination of a variety of forms of struggle to play the overall power of the people’s war . In information warfare, military struggle and political, economic, diplomatic, cultural, ideological struggles fields more closely intertwined, in some cases even non-dominant armed struggle. Therefore, adherence to the combination of a variety of forms of struggle, for winning the information war has a more important significance.
In information warfare, military by political factors more prominent political and military action, strong policy, and even a small tactical actions may be related to the overall strategic situation in the international community have a broad impact. Therefore, the information warfare conduct civil wars, on the one hand to make war all soldiers and civilians establish the overall concept of policy ideas, with significant international influence in the issue, in relation to the overall operations, ensure that the needs of the military and political obedience. On the other hand struggle in the UN and other international arena widespread publicity, win public support, and strive to get politically active.
Information warfare increasingly focused on economic efficiency, greater dependence on the economy. In the rapidly growing trend of economic globalization, the case of economic blockade, economic sanctions would weaken the enemy’s comprehensive national strength is an important initiative, and to combat the economic center of the enemy, the better to play a drastic effect. During the Gulf War, the Kosovo War and the war in Iraq, the United States launched the war before the war and implementation process, are complemented by economic sanctions.
It is foreseeable that in the information war, economic sanctions and counter-sanctions, blockade and counter-blockade as a primary means of economic sectors will be fierce struggle to become another battlefield of information warfare. We conduct information warfare people’s war, on the one hand to use economic means of struggle, economic base and destroy the enemy’s ability to regenerate, maximize the economic loss to the enemy, eroding its war potential; hand to mobilize kind of strength, positive and effective implementation of economic protection, maintaining the normal operation of the national economy, efforts to develop production, economic development, for the victory of the war to lay a solid material foundation. Any one country to war are very focused use of diplomatic means to secure more state support to maximize isolate each other, give each other causing huge political and moral pressure. Even superpowers also paid great attention to diplomacy with military struggle. In information warfare launched the people’s war, of course, but also actively through diplomatic struggle to establish a broad international united front.
Reform and opening up, China has actively conducted exchanges and cooperation in the international political, economic, cultural and other fields has played an active and important role in the international community to establish a peace-loving, maintain stability, to just and responsible handling of international affairs the image of a big country, it’s all for us in the information warfare fruitful diplomatic struggle to create the conditions. In the information war, we want to make good use of all kinds of contradictions, give full play to all efforts conducive to my various international factors. To take full advantage of the favorable as a permanent member of the UN’s international status, to consolidate and expand the role of the United Nations, especially the UN Security Council in dealing with the leading role of international security to thwart any so-called international intervention against our country; give full play and the developing countries consistent with the fundamental interests of political advantage, and properly handle the relationship with the countries concerned, differentiation enemy’s allies; pay attention and have a special country with the same or equivalent national strategic interests of the military establishment of some form of collaboration or partnership, the strategic formation of a certain degree of cooperation and coordinate mechanisms.
As long as we are able to unite all forces that can be united, to win the support of as many countries as to maximize isolate and attack the enemy, you can establish a broad international united front for the victory to carry out the people’s war to create a favorable international environment. Information warfare, media warfare, warfare has become increasingly important. In the field of public opinion and propaganda, should make full use of newspapers, television, radio, Internet, multimedia and other traditional and non-traditional media, the Western developed countries of the world and strive to break the monopoly of public opinion, crushing hostile nations attempt to demonize the image of our country, torn hegemony doctrine of “human rights”, “humanitarian aid”, “democracy” and so gorgeous packaging, with true, correct public opinion supported the war inspired the masses of enthusiasm and self-consciousness, for the support of the international community on China.
In the legal battle field, we should make good use of existing international law, to carry out the people’s war for me to provide a legal basis to prevent the enemy to international law as an excuse for me to intervene and wage war, but also to actively participate in international law and various international mechanisms the development and establishment, to prevent the establishment of prejudicial interests of our country, is conducive to hostile forces and international mechanisms of international law, but also to strengthen domestic legislation in the field work, so that hostile forces without loopholes. At the same time, pay attention to the psychological protection, encouraging all people to fight, winning the information war and build a strong psychological defense.
信息化战争中开展人民战争面临的挑战和对策思考
国防大学战略教研室 卢 勇
中國人民解放軍
總參謀部
人民战争是我军克敌制胜的传统法宝。上个世纪90年代以来,随着世界新军事变革的蓬勃兴起和高技术兵器在战争中的广泛应用,战争形态开始由机械化战争向信息化战争转变,“信息化战争将是21世纪的主要战争形态”已经成为共识。在半机械化、机械化战争中形成和发展起来的人民战争思想,如何正视信息化战争所带来的挑战、如何继续在信息化战争中发挥其特有的优势,确保打赢未来可能发生的战争,是我们面临的一个重大的理论问题和紧迫的实践问题。