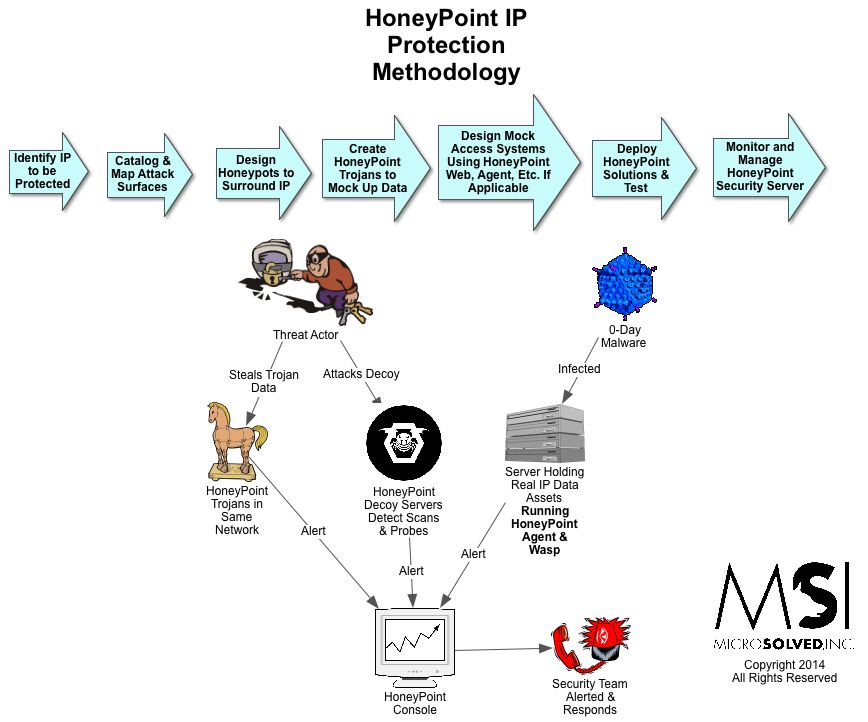
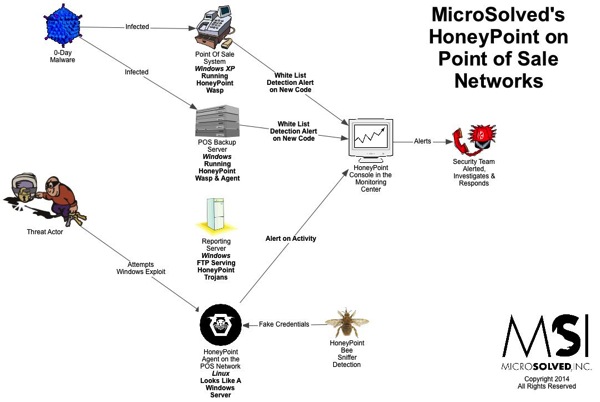
This time around we had a question from a reader (thanks for the question!):
“My organization is very concerned about malware on desktop machines. We run anti-virus on all user systems but have difficulty keeping them clean and are still having outbreaks. What else can we do to keep infected machines from hurting us? –LW”
Phil Grimes (@grap3_ap3) responds:
In this day and age, preventing infection on desktop workstations is a losing battle. While Anti-virus and other measures can help protect the machine to some extent, the user is still the single greatest point of entry an attacker can leverage. Sadly, traditional means for prevention don’t apply to this attack vector, as tricking a user into clicking on the “dancing gnome” often launches attacks at levels our prevention solutions just can’t touch.
Realizing this is the first, and biggest step to success here.
Once we’ve embraced the fact that we need better detection and response mechanisms, we start to see how honeypots can help us but also how creating better awareness within our users can be the greatest investment an organization might make in detection. Teach your people what “normal” looks like. Get them in the habit of looking for things that go against that norm. Then, get them to want to tell someone when they see these anomalies! A well trained user base is more efficient, effective, and reliable detection mechanism an organization can have. After that, learn how to respond when something goes wrong.
John Davis added:
Some of the best things you can do to combat this problem is to implement good, restrictive egress filtering and ensure that users have only those local administration rights to their workstations that they absolutely need.
There are different ways to implement egress filtering, but a big part of the most secure implementation is whitelisting. Whitelisting means that you start by a default deny of all outbound connections from your network, then only allow those things outbound that are specifically needed for business purposes. One of the ways that malware can infect user systems is by Internet surfing. By strictly limiting the sites that users can visit, you can come close to eliminating this infection vector (although you are liable to get plenty of blowback from users – especially if you cut visiting social networking sites).
Another malware infection vector is from users downloading infected software applications to their machines on disks or plugging in infected portable devices such as USB keys and smart phones to their work stations. This can be entirely accidental on the part of the user, or may be done intentionally by hostile insiders like employees or third party service providers with access to facilities. So by physically or logically disabling users local administration rights to their machines, you can cut this infection vector to almost nil.
You still have to worry about email, though. Everybody needs to use email and antivirus software can’t stop some malware such as zero day exploits. So, for this vector (and for those users who still need Internet access and local admin rights to do their jobs), specific security training and incentive programs for good security practices can go a long way. After all, a motivated human is twice as likely to notice a security issue than any automated security solution.
Adam Hostetler also commented:
Ensure a policy for incident response exists, and that it meets NIST guidelines for handling malware infections. Take the stand that once hosts are infected they are to rebuilt and not “cleaned”. This will help prevent reinfection from hidden/uncleaned malware. Finally, work towards implementing full egress controls. This will help prevent malware from establishing command and control channels as well as combat data leakage.
Got a question for the experts? If so, leave us a comment or drop us a line on Twitter (@microsolved). Until next time, stay safe out there!