This post builds on the What is HPSS? Series. Previous posts are here and here.
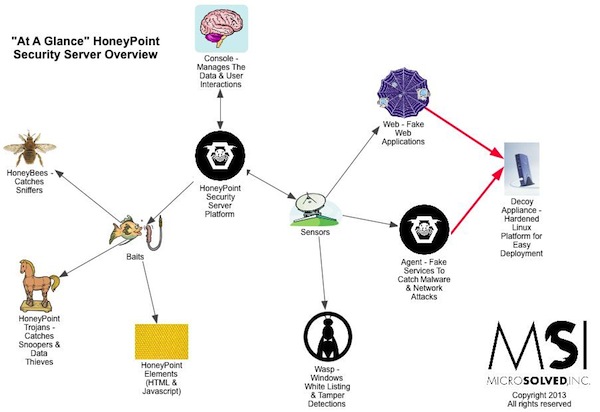
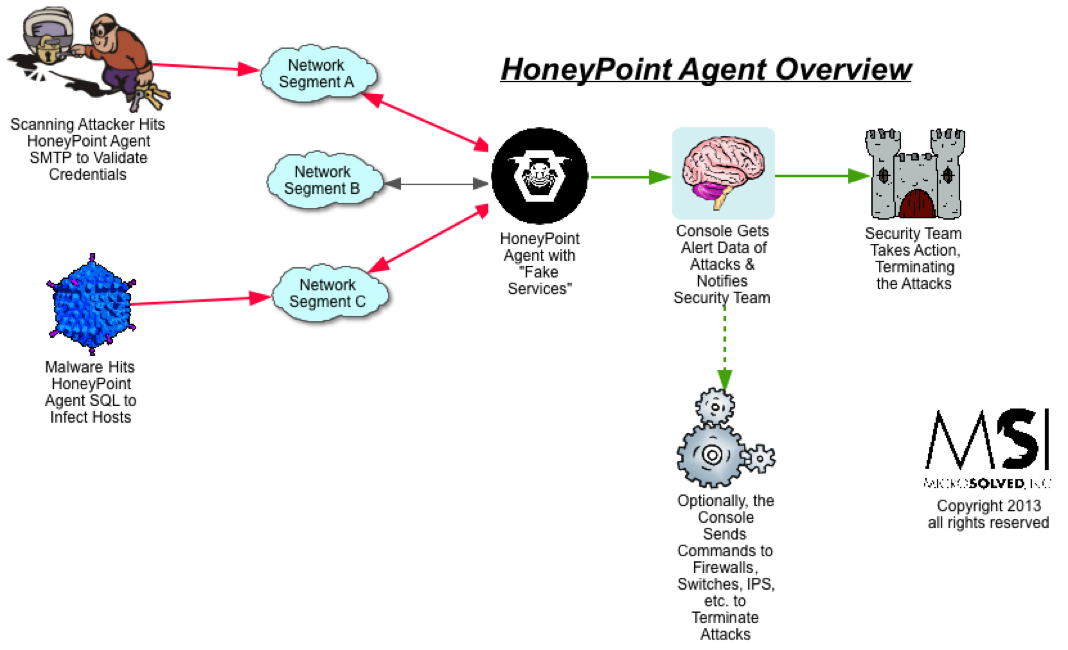
HoneyPoint Agent is the original detection capability of the HoneyPoint Security Server suite. Basically, it allows a system to offer up a variety of “fake services” to the network for the purpose of detection. These services can either be simple port listeners or can be complex, deeper emulations of protocols like SMTP, HTTP, Telnet, FTP, etc. These ports have no real users and no legitimate traffic flows to them. This means that anytime these ports are tampered with, the interactions are “suspicious at best and malicious at worst”.
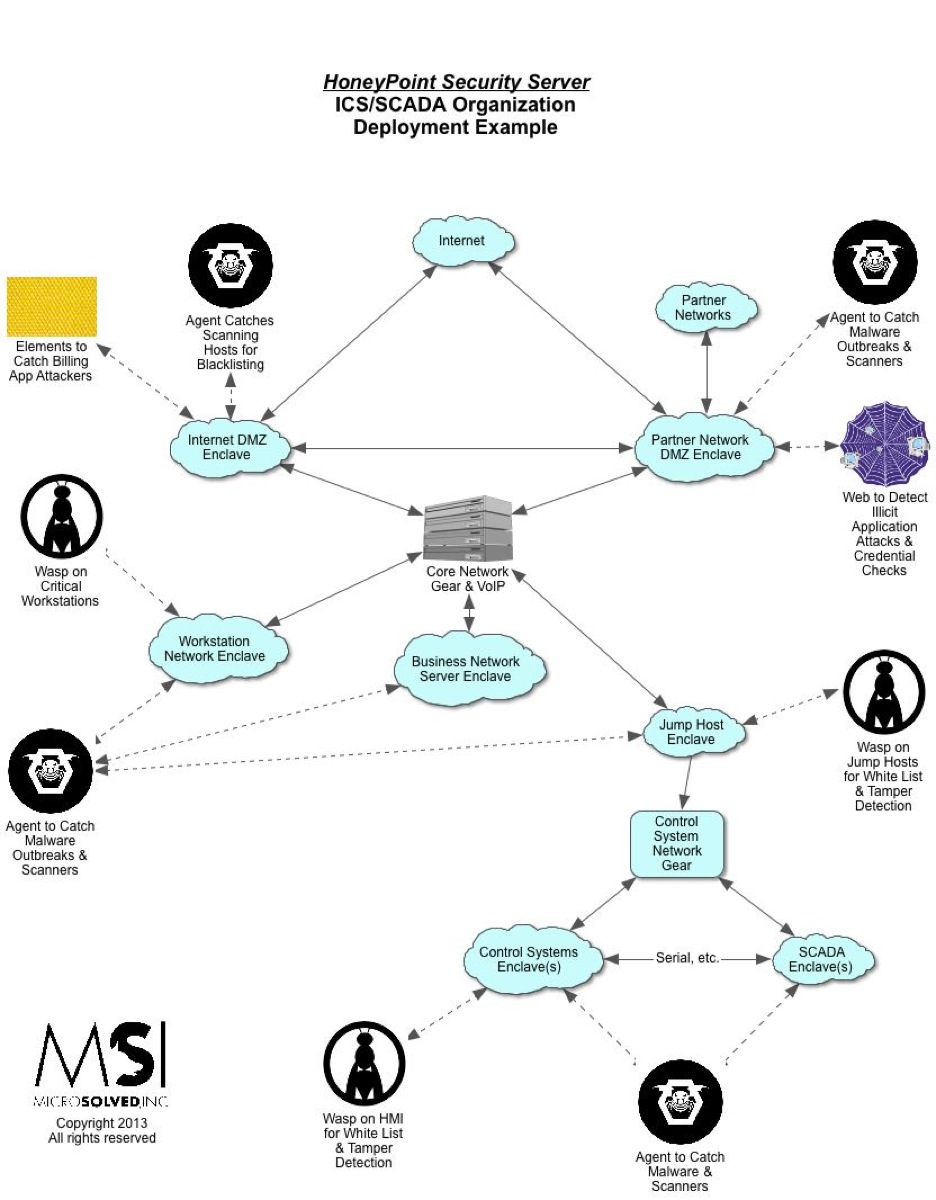
Because the Agent is designed to be extremely light weight in terms of computing power needed, the Agents can be sprinkled throughout the network environment easily. Many organizations simply add Agent into default server and workstation builds, turning most of the systems in their network into sensors for detection.
Other organizations deploy Agent more sporadically, either using virtual or physical appliances dedicated to HoneyPoint hosting. These organizations often assign multiple physical or virtual interfaces to the devices, allowing them to have a presence on many network segments at the same time.
Still other users leverage an approach called “scattersensing” by deploying HoneyPoint on systems that they move periodically around their environment. This makes for a less dependable detection mechanism, but gives them the capability to get more vision into “hotspots” where targeting is expected or where malware is more likely to pop-up.
The most successful HoneyPoint Agent deployments use a combination of these tactics, along with including strategies like DNS redirection of known command and control sites and other more active forms of getting bad traffic into the HoneyPoint systems.
HoneyPoint Agent has proven to be very useful in identifying scanning and malware outbreaks. Customers with supposedly secure networks have found malware that had been missed for years by their traditional internal security tools. These were detected when the ongoing slow and low scanning triggered HoneyPoint deployments, particularly for SQL, Terminal Server and other commonly targeted ports.
HoneyPoint Agent can be configured through the command line or via a GUI application, making it easy to manage and deploy. Once installed, it is a “deploy and forget” style tool which doesn’t require ongoing tuning or signature updates. Generally speaking, customers deploy Agent and it runs for years without feeding and care.
HoneyPoint Agent also features MSI’s patented “defensive fuzzing” capabilities (previously known as HornetPoint mode), which can create self-defending services that attempt to take down attacker tools during their probing to interfere with propagation. Still other users automate defense with Agent using it as a means for black holing hosts that probe their environment. In these optional, more active roles, Agent can help organizations strengthen their posture with a “one strike and you’re out” kind of approach.
HoneyPoint Agent runs in Linux, Windows and OS X. It communicates securely with the HoneyPoint Console. It also features user configurable services, a known scanning host ignore list (for ongoing vulnerability assessment clients) and a wide variety of common service emulation templates (available through support).
To learn more about HoneyPoint Security Server or to get a demo, please contact us. We would be happy to walk you through the product and discuss how it might fit into your environment. There is even a free for personal use “Community Edition” available to get you started or to let you experience the power, ease and flexibility of the platform yourself. Just give us a call to learn more about HoneyPoint Security Server and HoneyPoint Agent. You’ll be glad you did!